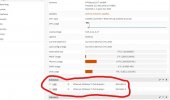
Currently, I have a PfSense VM running on Proxmox. I can access the internet and Proxmox through the LAN port, however, I can't access the internet from the Proxmox Host, or any VMs or containers. I am unsure if this is a problem with PfSense or Proxmox.
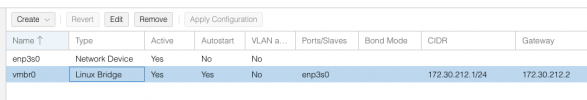
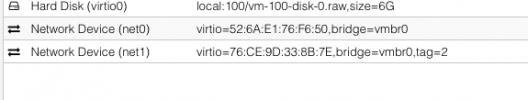
I have two virtual switches that correspond to two real ports. I have the WAN port (vmbr0) and the LAN port (vmbr1). The WAN port goes out to my school's network, and the LAN port goes out to my Nighthawk router running in AP mode.
That works perfectly and I can access the internet from all devices through the Nighthawk router (LAN).
But, I can't access the internet through Proxmox itself. I can access Proxmox through the LAN using the IP specified on vmbr1 which is 10.0.0.100. On the Proxmox host, I can ping 10.0.0.1 (PfSense VM) but I can't ping google.com. This holds true with VMs and containers under Proxmox too.
It is not a DNS issue because hosts resolve to an IP. It just can't get data once the DNS resolves.
Proxmox Host Shell:
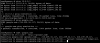
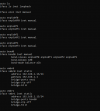
The network setup is outlined below (/etc/network/interfaces):
I have two virtual switches that correspond to two real ports. I have the WAN port (vmbr0) and the LAN port (vmbr1). The WAN port goes out to my school's network, and the LAN port goes out to my Nighthawk router running in AP mode.
That works perfectly and I can access the internet from all devices through the Nighthawk router (LAN).
But, I can't access the internet through Proxmox itself. I can access Proxmox through the LAN using the IP specified on vmbr1 which is 10.0.0.100. On the Proxmox host, I can ping 10.0.0.1 (PfSense VM) but I can't ping google.com. This holds true with VMs and containers under Proxmox too.
It is not a DNS issue because hosts resolve to an IP. It just can't get data once the DNS resolves.
Proxmox Host Shell:

The network setup is outlined below (/etc/network/interfaces):
Code:
auto lo
iface lo inet loopback
iface eno1 inet manual
iface eno2 inet manual
iface eno3 inet manual
iface eno4 inet manual
auto vmbr0
iface vmbr0 inet manual
bridge-ports eno1
bridge-stp off
bridge-fd 0
auto vmbr1
iface vmbr1 inet static
address 10.0.0.100
netmask 255.255.255.0
gateway 10.0.0.1
bridge-ports eno2
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
#pfSense