Hello everyone,
We would like to use Proxmox on a Cisco UCS B200 M-Series Blade. We've already installed the latest Proxmox version on the Host.
From the network side on the switch we've configured two LACPs which has 4 ports each. With the VLANs 9 for management and 201, 4092 for data. This has also been configured on the Cisco Blade Center.
How must this be configured within Proxmox, in order to avoid any networking issues (e.g. Loops)?
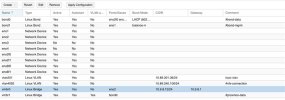
Our plan was to configure first one port (eno2) on the blade with the management network and put that on the bridge (vmbr0) afterwards we'd put every VLAN on all Ports (eno1 - eno4) and put all ports in the bridge vmbr0 (see attached image).
How would you configure it?
Thanks
We would like to use Proxmox on a Cisco UCS B200 M-Series Blade. We've already installed the latest Proxmox version on the Host.
From the network side on the switch we've configured two LACPs which has 4 ports each. With the VLANs 9 for management and 201, 4092 for data. This has also been configured on the Cisco Blade Center.
How must this be configured within Proxmox, in order to avoid any networking issues (e.g. Loops)?
Our plan was to configure first one port (eno2) on the blade with the management network and put that on the bridge (vmbr0) afterwards we'd put every VLAN on all Ports (eno1 - eno4) and put all ports in the bridge vmbr0 (see attached image).
How would you configure it?
Thanks


