Hi everybody,
I am struggeling with a problem where I did not figure out yet if it is a "basic" networking problem or something that has to do with my SDN configuration.
The setup is the following:
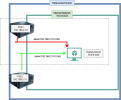
I have two VEs (192.168.2.10 and .11) coupled as a cluster. Within this cluster there is an internal network (10.0.0.0/24). It is realized as EVPN/VNET/SUBNET with SNAT option enabled:
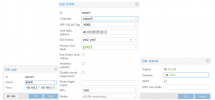
In this network there is a server (syslog server hosted on PVE1 listening on port 5140). To make this server available for resources outside of the internal network there is a active IPtables DNAT rule on each PVE node:
That is basically working. All hosts (including PVE2) of the network 192.168.2.0/24 can call the port 5140 via telnet ($> telnet 192.168.2.10 5140).
Now I want PVE1 to also use this syslog server by calling its own IP (192.168.2.10). But this does not work. Now I am struggeling to figure out the underlying problem. Is it a problem of the SDN configuration or just the NATting that needs more config?
Normally I would like to configure PVE1 to use the internal IP of the server (10.0.0.3) but this doesn't work either. I think this is because of the SDN and how it works. I thought that the "Exit Nodes local routing" option should have done the trick. But that one did not work as well and brought further networking problems I just did not want to troubleshoot yet as long as there is an option to use the external IP (192.168.2.10) and DNAT.
I am struggeling with a problem where I did not figure out yet if it is a "basic" networking problem or something that has to do with my SDN configuration.
The setup is the following:

I have two VEs (192.168.2.10 and .11) coupled as a cluster. Within this cluster there is an internal network (10.0.0.0/24). It is realized as EVPN/VNET/SUBNET with SNAT option enabled:

In this network there is a server (syslog server hosted on PVE1 listening on port 5140). To make this server available for resources outside of the internal network there is a active IPtables DNAT rule on each PVE node:
Code:
Chain PREROUTING (policy ACCEPT 654K packets, 32M bytes)
pkts bytes target prot opt in out source destination
10 748 DNAT tcp -- vmbr0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:5140 to:10.0.0.3:5140That is basically working. All hosts (including PVE2) of the network 192.168.2.0/24 can call the port 5140 via telnet ($> telnet 192.168.2.10 5140).
Now I want PVE1 to also use this syslog server by calling its own IP (192.168.2.10). But this does not work. Now I am struggeling to figure out the underlying problem. Is it a problem of the SDN configuration or just the NATting that needs more config?
Normally I would like to configure PVE1 to use the internal IP of the server (10.0.0.3) but this doesn't work either. I think this is because of the SDN and how it works. I thought that the "Exit Nodes local routing" option should have done the trick. But that one did not work as well and brought further networking problems I just did not want to troubleshoot yet as long as there is an option to use the external IP (192.168.2.10) and DNAT.

