Hi
I've been running proxmox and pfsense virtualized for some months now and am relatively happy about it. The proxmox-server is headless so when I once in a while screw things up, I physically move it and lose all internet connectivity, then plugin HDMI and usb keyboard so I can see what is going on - but without DHCP-server/network, it's a hazzle (home setup). The last week I was playing with openvpn and wireguard server and suddenly everything crashed and became unresponsive. This is where I realized that I need a better solution and a better setup to avoid moving the server and have the whole network down, until I've sorted things out... On the proxmox system, I currently have:
Network configuration:
Proxmox (host):
Remarks:
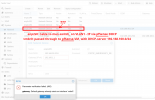
I think it's a problem that the gateway is 192.168.100.1, which is the ip address to the pfSense-router. Furthermore I do not wish to passthrough "enp1s0f3" to pfSense, because I would like to be able to access proxmox, even if pfSense crashes or is turned off. I experience some issues I don't understand, e.g. if try to create a whole new interface for "enp1s0f3" with ip 192.168.90.2/24 and gateway 192.168.90.1, then I get "Error: Parameter verification failed. (400) gateway: Default gateway already exists on interface 'vmbr0'... But vmbr0 depends on pfSense, right? I also don't understand why enp1s0f3 is not "active", but maybe it is waiting for a DHCP-server? I tried putting a network cable in my laptop, manually assigning the IP address to the correct subnet, but then I guess it does not make sense to talk about a gateway?
I'm just really confused and trying to learn more about networks. Maybe I need to bridge something - I hope someone can help me straighten things out and I hope my explanation of my thoughts is understandable, otherwise I'll try to elaborate where needed...
I've been running proxmox and pfsense virtualized for some months now and am relatively happy about it. The proxmox-server is headless so when I once in a while screw things up, I physically move it and lose all internet connectivity, then plugin HDMI and usb keyboard so I can see what is going on - but without DHCP-server/network, it's a hazzle (home setup). The last week I was playing with openvpn and wireguard server and suddenly everything crashed and became unresponsive. This is where I realized that I need a better solution and a better setup to avoid moving the server and have the whole network down, until I've sorted things out... On the proxmox system, I currently have:
Network configuration:
Proxmox (host):
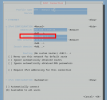
Code:
cat /etc/network/interfaces
auto lo
iface lo inet loopback
auto enp2s0
iface enp2s0 inet dhcp
iface enp1s0f0 inet manual
iface enp1s0f1 inet manual
iface enp1s0f2 inet manual
auto enp1s0f3
iface enp1s0f3 inet static
address 192.168.100.3/24
#STATIC_EMERGENCY_RESCUE
auto vmbr0
iface vmbr0 inet static
address 192.168.100.2/24
gateway 192.168.100.1
bridge-ports none
bridge-stp off
bridge-fd 0
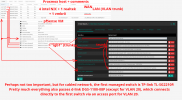
post-up /sbin/ethtool -s enp2s0 wol g- I can currently successfully connect to the proxmox webUI via https://192.168.1.2:8006 - but this is only because pfSense knows the MAC address so it statically assigns the IP address via DHCP.
- Furthermore, I can access the proxmox webUI via (vmbr0) https://192.168.100.2:8006/ - I this this because I wanted a static IP address in case pfsense misbehaves, so I should still be able to start/stop VMs and perform emergency tasks.
- The problem with (vmbr0) and access via https://192.168.100.2:8006/ is that (I think) it relies on pfSense being up and acting as a router/gateway. I created vmbr0 so VMs and a LXC fileserver can talk to each other (for config-backups, smb/cifs and nfs) and the whole 192.168.100.0/24 is an interface in pfSense, with a corresponding DHCP-server (responsible for handing out a statically assigned ip to the LXC fileserver on the same subnet, via DHCP).
I think it's a problem that the gateway is 192.168.100.1, which is the ip address to the pfSense-router. Furthermore I do not wish to passthrough "enp1s0f3" to pfSense, because I would like to be able to access proxmox, even if pfSense crashes or is turned off. I experience some issues I don't understand, e.g. if try to create a whole new interface for "enp1s0f3" with ip 192.168.90.2/24 and gateway 192.168.90.1, then I get "Error: Parameter verification failed. (400) gateway: Default gateway already exists on interface 'vmbr0'... But vmbr0 depends on pfSense, right? I also don't understand why enp1s0f3 is not "active", but maybe it is waiting for a DHCP-server? I tried putting a network cable in my laptop, manually assigning the IP address to the correct subnet, but then I guess it does not make sense to talk about a gateway?
I'm just really confused and trying to learn more about networks. Maybe I need to bridge something - I hope someone can help me straighten things out and I hope my explanation of my thoughts is understandable, otherwise I'll try to elaborate where needed...
Attachments
Last edited: