Enjoy your holiday 
The config as generated now is:
I would change it to:
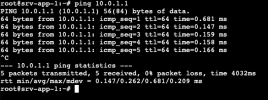
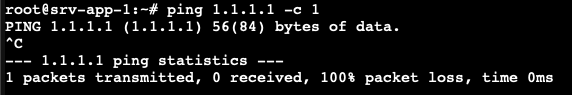
After I do this a session to my eBGP peer is no longer established.
Unfortunately I am not as fluent with routing and am not sure what I am doing, as a consequence there are probably some errors in there.
The config as generated now is:
Code:
frr version 8.0.1
frr defaults datacenter
hostname chsfl1-cl01-pve01
log syslog informational
service integrated-vtysh-config
!
!
vrf vrf_evpn
vni 500
exit-vrf
!
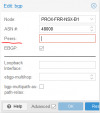
router bgp 65002
bgp router-id 100.111.64.3
no bgp default ipv4-unicast
coalesce-time 1000
neighbor BGP peer-group
neighbor BGP remote-as external
neighbor BGP bfd
neighbor BGP ebgp-multihop 4
neighbor 100.111.64.1 peer-group BGP
neighbor VTEP peer-group
neighbor VTEP remote-as external
neighbor VTEP bfd
neighbor 192.168.102.102 peer-group VTEP
neighbor 192.168.102.103 peer-group VTEP
!
address-family ipv4 unicast
neighbor BGP activate
neighbor BGP soft-reconfiguration inbound
import vrf vrf_evpn
exit-address-family
!
address-family ipv6 unicast
import vrf vrf_evpn
exit-address-family
!
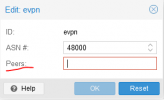
address-family l2vpn evpn
neighbor VTEP route-map MAP_VTEP_IN in
neighbor VTEP route-map MAP_VTEP_OUT out
neighbor VTEP activate
advertise-all-vni
autort as 65010
exit-address-family
!
router bgp 65002 vrf vrf_evpn
bgp router-id 192.168.102.101
!
address-family ipv4 unicast
redistribute connected
exit-address-family
!
address-family ipv6 unicast
redistribute connected
exit-address-family
!
address-family l2vpn evpn
route-target import 65010:500
route-target export 65010:500
default-originate ipv4
default-originate ipv6
exit-address-family
!
route-map MAP_VTEP_IN deny 1
match evpn route-type prefix
!
route-map MAP_VTEP_IN permit 2
!
route-map MAP_VTEP_OUT permit 1
!
line vtyI would change it to:
Code:
frr version 8.0.1
frr defaults datacenter
hostname chsfl1-cl01-pve01
log syslog informational
service integrated-vtysh-config
!
!
vrf vrf_evpn
vni 500
exit-vrf
!
router bgp 65002
bgp router-id 100.111.64.3
no bgp default ipv4-unicast
coalesce-time 1000
neighbor VTEP peer-group
neighbor VTEP remote-as external
neighbor VTEP bfd
neighbor 192.168.102.102 peer-group VTEP
neighbor 192.168.102.103 peer-group VTEP
!
address-family ipv4 unicast
neighbor BGP activate
neighbor BGP soft-reconfiguration inbound
exit-address-family
!
address-family ipv6 unicast
exit-address-family
!
address-family l2vpn evpn
neighbor VTEP route-map MAP_VTEP_IN in
neighbor VTEP route-map MAP_VTEP_OUT out
neighbor VTEP activate
advertise-all-vni
autort as 65010
exit-address-family
!
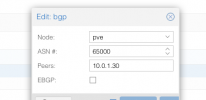
router bgp 65002 vrf vrf_evpn
bgp router-id 192.168.102.101
neighbor BGP peer-group
neighbor BGP remote-as external
neighbor BGP bfd
neighbor BGP ebgp-multihop 4
neighbor 100.111.64.1 peer-group BGP
!
address-family ipv4 unicast
exit-address-family
!
address-family ipv6 unicast
exit-address-family
!
address-family l2vpn evpn
route-target import 65010:500
route-target export 65010:500
default-originate ipv4
default-originate ipv6
exit-address-family
!
route-map MAP_VTEP_IN deny 1
match evpn route-type prefix
!
route-map MAP_VTEP_IN permit 2
!
route-map MAP_VTEP_OUT permit 1
!
line vtyAfter I do this a session to my eBGP peer is no longer established.
Unfortunately I am not as fluent with routing and am not sure what I am doing, as a consequence there are probably some errors in there.