@spirit
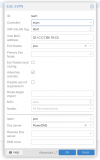
I tried to ping from my vmbr0.11 interface which is 10.0.1.1 to 10.0.101.254 (gateway of subnet on VNet)
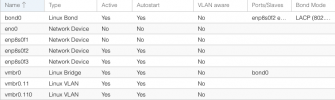
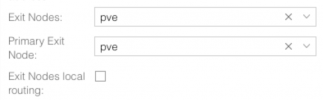
My route all route tables looks like this
It seems that something isn't working between communication on two route tables - default and the vrf_test1
It seems that this is a new issue that wasn't considered.
I tried to ping from my vmbr0.11 interface which is 10.0.1.1 to 10.0.101.254 (gateway of subnet on VNet)
Bash:
root@pve:~# ping 10.0.101.254 -I vmbr0.11
PING 10.0.101.254 (10.0.101.254) from 10.0.1.1 vmbr0.11: 56(84) bytes of data.
^C
--- 10.0.101.254 ping statistics ---
10 packets transmitted, 0 received, 100% packet loss, time 9193msMy route all route tables looks like this
Code:
root@pve:~# ip route show table all
10.0.101.0/24 dev test1 table vrf_test1 proto kernel scope link src 10.0.101.254
local 10.0.101.254 dev test1 table vrf_test1 proto kernel scope host src 10.0.101.254
broadcast 10.0.101.255 dev test1 table vrf_test1 proto kernel scope link src 10.0.101.254
default via 10.0.1.30 dev vmbr0.11
10.0.1.0/27 dev vmbr0.11 proto kernel scope link src 10.0.1.1
10.0.10.0/24 dev vmbr0.110 proto kernel scope link src 10.0.10.252
10.0.101.0/24 nhid 77 dev test1 proto bgp metric 20
172.17.0.0/16 dev docker0 proto kernel scope link src 172.17.0.1 linkdown
192.168.0.0/16 nhid 42 via 10.0.1.30 dev vmbr0.11 proto bgp metric 20
local 10.0.1.1 dev vmbr0.11 table local proto kernel scope host src 10.0.1.1
broadcast 10.0.1.31 dev vmbr0.11 table local proto kernel scope link src 10.0.1.1
local 10.0.10.252 dev vmbr0.110 table local proto kernel scope host src 10.0.10.252
broadcast 10.0.10.255 dev vmbr0.110 table local proto kernel scope link src 10.0.10.252
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
local 172.17.0.1 dev docker0 table local proto kernel scope host src 172.17.0.1
broadcast 172.17.255.255 dev docker0 table local proto kernel scope link src 172.17.0.1 linkdown
anycast fe80:: dev vrfbr_test1 table vrf_test1 proto kernel metric 0 pref medium
anycast fe80:: dev test1 table vrf_test1 proto kernel metric 0 pref medium
local fe80::301c:c7ff:feb6:78c5 dev test1 table vrf_test1 proto kernel metric 0 pref medium
local fe80::54d8:13ff:feed:6d1c dev vrfbr_test1 table vrf_test1 proto kernel metric 0 pref medium
fe80::/64 dev vrfbr_test1 table vrf_test1 proto kernel metric 256 pref medium
fe80::/64 dev test1 table vrf_test1 proto kernel metric 256 pref medium
multicast ff00::/8 dev vrfbr_test1 table vrf_test1 proto kernel metric 256 pref medium
multicast ff00::/8 dev test1 table vrf_test1 proto kernel metric 256 pref medium
::1 dev lo proto kernel metric 256 pref medium
fe80::/64 dev vmbr0 proto kernel metric 256 pref medium
fe80::/64 dev vmbr0.11 proto kernel metric 256 pref medium
fe80::/64 dev vmbr0.110 proto kernel metric 256 pref medium
local ::1 dev lo table local proto kernel metric 0 pref medium
anycast fe80:: dev vmbr0 table local proto kernel metric 0 pref medium
anycast fe80:: dev vmbr0.11 table local proto kernel metric 0 pref medium
anycast fe80:: dev vmbr0.110 table local proto kernel metric 0 pref medium
local fe80::21e:67ff:fe00:1101 dev vmbr0.11 table local proto kernel metric 0 pref medium
local fe80::21e:67ff:fe01:1053 dev vmbr0.110 table local proto kernel metric 0 pref medium
local fe80::21e:67ff:fe68:d0 dev vmbr0 table local proto kernel metric 0 pref medium
multicast ff00::/8 dev vmbr0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev vmbr0.11 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev vmbr0.110 table local proto kernel metric 256 pref mediumIt seems that something isn't working between communication on two route tables - default and the vrf_test1
Bash:
root@pve:~# ip route show table vrf_test1
10.0.101.0/24 dev test1 proto kernel scope link src 10.0.101.254
local 10.0.101.254 dev test1 proto kernel scope host src 10.0.101.254
broadcast 10.0.101.255 dev test1 proto kernel scope link src 10.0.101.254It seems that this is a new issue that wasn't considered.