Hi, first I want to thank everyone who answers on this thread and assists me with my issue!
GOAL
Have SDN VNet's for communication between VMs on different compute nodes and access the internet through SNAT on the VNet.
ISSUE
VMs configured with a VNet can't access the internet
Communication between VMs on the same VNet WORKS just fine, on both the same and different compute nodes. So the issue is only related to accessing the internet.
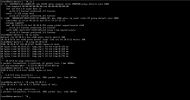
As you can see in the screenshot ping to 10.10.0.52 (VM on CN002 node) works. Any other ping fails.
INFO
I've tested with both VLAN and VXLAN SDN zone types, result is the same. The ideal bride/peers to use would be vmbr1 (peers 10.1.20.101...) but I've tested also with vmbr0 as I've notice that my vmbr1 for some reason cannot ping the internet too on the physcial node.
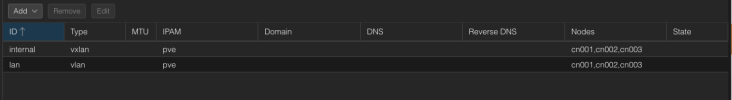
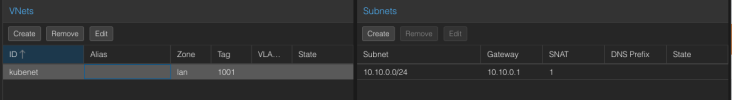
Network configuration on the nodes
Each now has the same network configuration only the IP's range from *.*.*.101 to *.*.*.104.
Network Configuration on the Fortigate
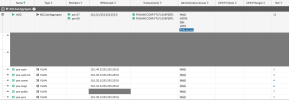
GOAL
Have SDN VNet's for communication between VMs on different compute nodes and access the internet through SNAT on the VNet.
ISSUE
VMs configured with a VNet can't access the internet
ping 8.8.8.8 fails. Communication between VMs on the same VNet WORKS just fine, on both the same and different compute nodes. So the issue is only related to accessing the internet.
As you can see in the screenshot ping to 10.10.0.52 (VM on CN002 node) works. Any other ping fails.

INFO
I've tested with both VLAN and VXLAN SDN zone types, result is the same. The ideal bride/peers to use would be vmbr1 (peers 10.1.20.101...) but I've tested also with vmbr0 as I've notice that my vmbr1 for some reason cannot ping the internet too on the physcial node.


Network configuration on the nodes
Each now has the same network configuration only the IP's range from *.*.*.101 to *.*.*.104.
Code:
auto lo
iface lo inet loopback
iface eno1 inet manual
iface eno2 inet manual
auto bond0
iface bond0 inet manual
bond-slaves eno1 eno2
bond-miimon 100
bond-mode 802.3ad
bond-xmit-hash-policy layer3+4
# Management Network (VLAN 110)
auto bond0.110
iface bond0.110 inet static
address 10.1.10.101/24
gateway 10.1.10.1
vlan-raw-device bond0
auto vmbr0
iface vmbr0 inet static
address 10.1.10.101/24
gateway 10.1.10.1
bridge-ports bond0.110
bridge-stp off
bridge-fd 0
# Cluster Communication Network (VLAN 120)
auto bond0.120
iface bond0.120 inet static
address 10.1.20.101/24
vlan-raw-device bond0
auto vmbr1
iface vmbr1 inet static
address 10.1.20.101/24
bridge_ports bond0.120
bridge_stp off
bridge_fd 0
# Corosync Network (VLAN 130)
auto bond0.130
iface bond0.130 inet static
address 10.1.30.101/24
vlan-raw-device bond0
# Ceph Public Network (VLAN 140)
auto bond0.140
iface bond0.140 inet static
address 10.1.40.101/24
vlan-raw-device bond0
auto vmbr2
iface vmbr2 inet static
address 10.1.40.101/24
bridge_ports bond0.140
bridge_stp off
bridge_fd 0
# Ceph Internal Network (VLAN 150)
auto bond0.150
iface bond0.150 inet static
address 10.1.50.101/24
vlan-raw-device bond0
auto vmbr3
iface vmbr3 inet static
address 10.1.50.101/24
bridge_ports bond0.150
bridge_stp off
bridge_fd 0
# Public Network for VMs (VLAN 200)
auto bond0.200
iface bond0.200 inet manual
vlan-raw-device bond0
auto vmbr4
iface vmbr4 inet manual
bridge_ports bond0.200
bridge_stp off
bridge_fd 0
iface eno3 inet manual
iface eno4 inet manual
source /etc/network/interfaces.d/*Network Configuration on the Fortigate


