Hi there,
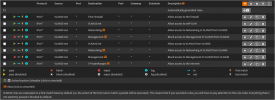
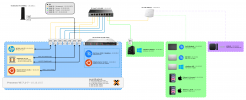
I am trying to create 2 VLANs or several of my VMs. The 2 VLANs in question are VLAN10 and VLAN20. They're a part of my network topology as seen in the image below:
The issue here is that I have a VM or two that I need in VLAN10 (such as my AdGuardHome DNS server), while I plan to place every other VM in VLAN20 (Such as my Gitlab Runner).
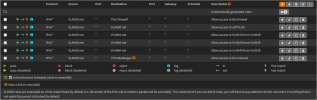
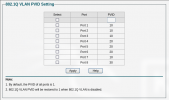
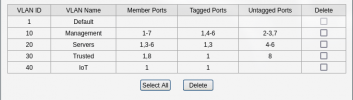
As seen in the graph, Port 3 of my TL-SG108E switch is PVID 10, while Port 4-5-6 are PVID 20. The tags/untags on my switch are as follows:
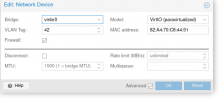
Thus, I created 2 Linux Bridges in Proxmox,
However, upon saving and either doing
Additionally, I tried just keeping
Can I request some assistance with this?
Thanks!
I am trying to create 2 VLANs or several of my VMs. The 2 VLANs in question are VLAN10 and VLAN20. They're a part of my network topology as seen in the image below:

The issue here is that I have a VM or two that I need in VLAN10 (such as my AdGuardHome DNS server), while I plan to place every other VM in VLAN20 (Such as my Gitlab Runner).
As seen in the graph, Port 3 of my TL-SG108E switch is PVID 10, while Port 4-5-6 are PVID 20. The tags/untags on my switch are as follows:

Thus, I created 2 Linux Bridges in Proxmox,
vmbr0 and vmbr1. I added 2 Linux VLANs, one under each Bridge and as a result, my /etc/network/interfaces looks like the following:
Code:
auto lo
iface lo inet loopback
iface eno1 inet manual
iface eno2 inet manual
iface eno3 inet manual
iface eno4 inet manual
iface ens2f0 inet manual
iface ens2f1 inet manual
auto vmbr0
iface vmbr0 inet static
bridge-ports eno1
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
auto vmbr0.10
iface vmbr0.10 inet static
address 10.10.10.5/24
gateway 10.10.10.1
auto vmbr1
iface vmbr1 inet static
bridge-ports eno2
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
auto vmbr1.20
iface vmbr1.20 inet static
address 10.10.20.1/24However, upon saving and either doing
systemctl restart networking.service or rebooting the server, I am unable to access my Proxmox GUI.Additionally, I tried just keeping
vmbr0, and keeping it VLAN Aware, and adding vmbr0 to my VMs with the VLAN ID, but when I do that, my VMs (specifically my DNS server) are unable to talk to my OPNsense or the internet.Can I request some assistance with this?
Thanks!