ZeroTier + Proxmox
We have been using ZeroTier over a year, when it came time to use it with Proxmox, I wasted hours due to my desire to over-complicate things. This four step process will let you access your containers and VMs remotely via the ZeroTier D-WAN / VPN
My goal is to configure several containers and vms on 10.101.101.0/24 on vmbr2
To do so:
1. Login to your ZeroTier account, add a network - we'll use 10.255.0.0/24
2. Join your remote workstation & PVE node to the network, assign the PVE node's IP address, we'll use 10.255.0.110
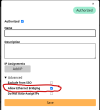
3. In my.zerotier.com add 10.101.101.0/24 as a managed route
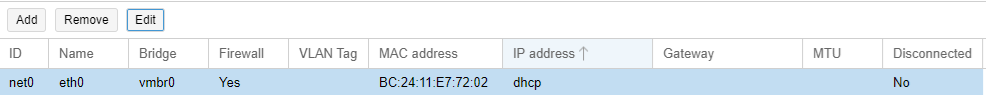
4. Add route to 10.101.101.0/24 on vmbr2
5. When building / modifying containers, use vmbr2 10.101.101.0/24
6. For system updates, you will want to enable masquerading
/etc/network/interfaces
grep -ris "vmbr2" /etc/pve:
my.zerotier.com:
We have been using ZeroTier over a year, when it came time to use it with Proxmox, I wasted hours due to my desire to over-complicate things. This four step process will let you access your containers and VMs remotely via the ZeroTier D-WAN / VPN
My goal is to configure several containers and vms on 10.101.101.0/24 on vmbr2
To do so:
1. Login to your ZeroTier account, add a network - we'll use 10.255.0.0/24
2. Join your remote workstation & PVE node to the network, assign the PVE node's IP address, we'll use 10.255.0.110
3. In my.zerotier.com add 10.101.101.0/24 as a managed route
4. Add route to 10.101.101.0/24 on vmbr2
5. When building / modifying containers, use vmbr2 10.101.101.0/24
6. For system updates, you will want to enable masquerading
/etc/network/interfaces
Code:
auto lo
iface lo inet loopback
auto eno5
iface eno5 inet manual
auto eno6
iface eno6 inet manual
iface eno7 inet manual
iface eno8 inet manual
auto enp193s0f4u4
iface enp193s0f4u4 inet dhcp
auto vmbr0
iface vmbr0 inet static
address 2.6.170.42/30
gateway 2.6.170.41
bridge-ports eno5
bridge-stp off
bridge-fd 0
bridge-maxwait 0
post-up ip route add 3.3.199.160/29 dev vmbr0
auto vmbr1
iface vmbr1 inet static
address 192.168.101.32/24
bridge-ports eno6
bridge-stp off
bridge-fd 0
bridge-maxwait 3
auto vmbr2
iface vmbr2 inet static
address 10.101.101.1/24
bridge-ports ztzlgi8qn1
bridge-stp off
bridge-fd 0
bridge-maxwait 3
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '10.101.101.0/24' -o vmbr0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '10.101.101.0/24' -o vmbr0 -j MASQUERADEgrep -ris "vmbr2" /etc/pve:
Code:
/etc/pve/nodes/vm101-01/qemu-server/103.conf:net0: e1000=F2:4E:F9:60:9A:40,bridge=vmbr2,firewall=1
/etc/pve/nodes/vm101-01/lxc/102.conf:net0: name=eth0,bridge=vmbr2,firewall=1,gw=10.101.101.1,hwaddr=86:11:17:5B:76:07,ip=10.101.101.10/24,type=veth
/etc/pve/nodes/vm101-01/lxc/100.conf:net1: name=eth1,bridge=vmbr2,firewall=1,gw=192.168.101.32,hwaddr=AE:79:8E:AD:E7:9D,ip=10.101.101.11/24,type=vethmy.zerotier.com: