Hi all,
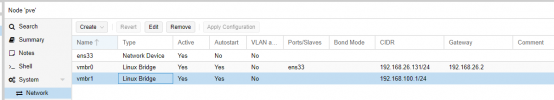
I'm in the process of migrating from VirtualBox and phpVirtualBox to Proxmox and most of my VMs are simply bridged to the public uplink of the host. I'm planning to change that to a suggested routed configuration, as my new hoster will be Hetzner providing a /28 subnet, which will only be used by my VMs in future.
Though, I have two special private networks as well: One of those was a bureau of my company in the past, has been cancelled and virtualized pretty much as-is. This means there's a firewall providing publicly available OVPN and some hosts behind that firewall. None of those hosts needs to be publicly available, but each needs to reach the outside world, e.g. to download updates for software. that is currently easily reached by making the firewall the gateway of all of the clients. Additionally, the clients need to see each other of course.
The second private network shared by some VMs is for strictly internal communication of those VMs as well. While each of those VMs is additionally bridged to the public interface of the host, they need a private, internal network on their own as well.
Using VirtualBox, both private networks were implemented by the concept of an internal network, simply by using different names. The firewall of described network 1 simply has multiple adapters and one of those is that private network.
If to use VLAN, which one? "VLAN awareness on the Linux bridge" and "Open vSwitch VLAN" read the most promising, so I should simply start with the first one?
Thanks!
I'm in the process of migrating from VirtualBox and phpVirtualBox to Proxmox and most of my VMs are simply bridged to the public uplink of the host. I'm planning to change that to a suggested routed configuration, as my new hoster will be Hetzner providing a /28 subnet, which will only be used by my VMs in future.
Though, I have two special private networks as well: One of those was a bureau of my company in the past, has been cancelled and virtualized pretty much as-is. This means there's a firewall providing publicly available OVPN and some hosts behind that firewall. None of those hosts needs to be publicly available, but each needs to reach the outside world, e.g. to download updates for software. that is currently easily reached by making the firewall the gateway of all of the clients. Additionally, the clients need to see each other of course.
The second private network shared by some VMs is for strictly internal communication of those VMs as well. While each of those VMs is additionally bridged to the public interface of the host, they need a private, internal network on their own as well.
Using VirtualBox, both private networks were implemented by the concept of an internal network, simply by using different names. The firewall of described network 1 simply has multiple adapters and one of those is that private network.
The closest I found for Proxmox was either masquerading/NAT or using a VLAN, with the latter reading more likely what I need. In my described network 1, the firewall would simply be publicly exposed using the routed config and besides that there are only really private/internal networks. So masquerading/NAT doesn't seem to make too much sense here. OTOH, the docs for the VLAN-approach read exactly like what I need:Internal networks are created automatically as needed. There is no central configuration. Every internal network is identified simply by its name. Once there is more than one active virtual network card with the same internal network ID, the Oracle VM VirtualBox support driver will automatically wire the cards and act as a network switch. The Oracle VM VirtualBox support driver implements a complete Ethernet switch and supports both broadcast/multicast frames and promiscuous mode.
So, should I use two different VLANs implementing the former internal networks? Or am I misunderstanding something about the purpose of those VLANs regarding VM-guests?So it is possible to have multiple networks (4096) in a physical network, each independent of the other ones.
If to use VLAN, which one? "VLAN awareness on the Linux bridge" and "Open vSwitch VLAN" read the most promising, so I should simply start with the first one?
Thanks!