Hello,
my ISP (Vodafone cable) provides two internet access points:
- standard (like any ISP offers)
- static IP
The router (here: AVM Fritz!Box 6490 cable) basically works like any other Fritz!Box with only one exception:
1 port is configured for using the static IP.
I guess one could call this passthrough.
Anyway, this means that I have the following port configuration with this Fritz!Box:
Port 1 - LAN
Port 2 - LAN
Port 3 - static IP passthrough
Port 4 - Guest LAN
The other network device is a managed switch (here: D-Link DGS-1100).
The use case regarding Proxmox VE is this.
On a VM I want to setup OPNsense as a router and firewall.
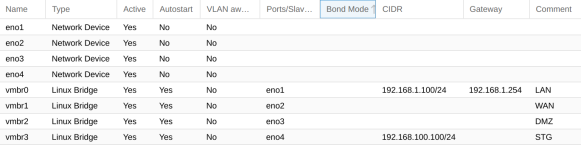
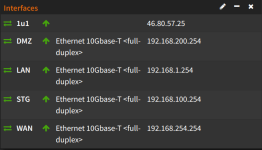
Having 5 ethernet ports on the Proxmox VE host, OPNsense VM will use 2 ports with PCI passthrough; eth0 for WAN (= static IP) and eth1 for LAN.
The other 3 ports are planned for this usage:
eth2+eth3: bond0
eth4: Management Network (VLAN)
In addition I want to setup different VLANs, e.g. a for Smarthome network, DMZ and PVE Guest network.
I also consider a VLAN for Fritz!Box LAN and Fritz!Box Guest LAN.
As a result the following VLANs would be available:
1 - Default
10 - Management network
20 - Fritz!Box LAN
30 - Fritz!Box Guest LAN
40 - OPNsense LAN
50 - Smarthome network
60 - DMZ
70 - PVE Guest network
Now the question is how to configure the VLAN on the managed switch?
Means, what VLAN should be used?
My current understanding is that 802.1Q is the preferred mode when using multiple VLANs on a single port.
And with 802.1Q there are different VLAN modes: Access Port, Trunk Port and Hybrid Port.
On the other hand one can configure port-based VLAN for the port that is connected to Fritz!Box Port 1 and Port 4 respectively.
But my managed switch allows either port-based VLAN or 802.1Q VLAN, and not a combination.
Can you please advise what is the recommended configuration on the managed switch, in particular the recommended VLAN mode?
What should be tagged? What should be untagged?
THX
my ISP (Vodafone cable) provides two internet access points:
- standard (like any ISP offers)
- static IP
The router (here: AVM Fritz!Box 6490 cable) basically works like any other Fritz!Box with only one exception:
1 port is configured for using the static IP.
I guess one could call this passthrough.
Anyway, this means that I have the following port configuration with this Fritz!Box:
Port 1 - LAN
Port 2 - LAN
Port 3 - static IP passthrough
Port 4 - Guest LAN
The other network device is a managed switch (here: D-Link DGS-1100).
The use case regarding Proxmox VE is this.
On a VM I want to setup OPNsense as a router and firewall.
Having 5 ethernet ports on the Proxmox VE host, OPNsense VM will use 2 ports with PCI passthrough; eth0 for WAN (= static IP) and eth1 for LAN.
The other 3 ports are planned for this usage:
eth2+eth3: bond0
eth4: Management Network (VLAN)
In addition I want to setup different VLANs, e.g. a for Smarthome network, DMZ and PVE Guest network.
I also consider a VLAN for Fritz!Box LAN and Fritz!Box Guest LAN.
As a result the following VLANs would be available:
1 - Default
10 - Management network
20 - Fritz!Box LAN
30 - Fritz!Box Guest LAN
40 - OPNsense LAN
50 - Smarthome network
60 - DMZ
70 - PVE Guest network
Now the question is how to configure the VLAN on the managed switch?
Means, what VLAN should be used?
My current understanding is that 802.1Q is the preferred mode when using multiple VLANs on a single port.
And with 802.1Q there are different VLAN modes: Access Port, Trunk Port and Hybrid Port.
On the other hand one can configure port-based VLAN for the port that is connected to Fritz!Box Port 1 and Port 4 respectively.
But my managed switch allows either port-based VLAN or 802.1Q VLAN, and not a combination.
Can you please advise what is the recommended configuration on the managed switch, in particular the recommended VLAN mode?
What should be tagged? What should be untagged?
THX
Last edited: