Hello everyone,
I've been struggling for hours with a strange problem that I don't understand.
I'll try to explain:
I have a VPS server on the Internet with a public IP 178.xxx.xxx.xxx/22.
Proxmox is installed on this server, and it should only be accessible via a VPN connection.
An opnsens is responsible for the vpn connection.
On Proxmox, there is an LXC container running that provides a VPN connection using Wireguard.
This part works.
For example, I can access Proxmox’s web interface or SSH into the LXC container from my local network (10.10.10.0/24).
However, there are some irregularities and certain things don't always work.
Sometimes, after restarting Proxmox, the LXC containers lose internet access.
It seems that the rule for outgoing NAT is not taking effect:
Although the rule is loaded, nothing is being routed through it:
That’s one issue. Another is that I can’t reliably SSH into an LXC container at 192.168.10.10.
It works once, but after a few minutes, if I try to open a second session, I get the error:
Network error: Software caused connection abort.
Other SSH sessions—such as to Proxmox directly at 192.168.10.1 or to the Wireguard gateway at 192.168.10.5—always work.
Even accessing the web interface at 192.168.1.1:8006 always works.
If I assign a different IP to the container at 192.168.10.10, it works at first but then stops working after a short time.
I see the same phenomenon with a new container.
What I’ve noticed is that establishing an SSH connection to 192.168.10.10 takes a few seconds longer than to 192.168.10.5 or 192.168.10.1.
During the period when an SSH connection cannot be established, I can still successfully ping the addresses.
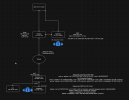
Based on the network diagram, this might be easier to understand.
When I track the packages with tcpdump, everything looks good so far.
it also makes no difference whether I switch the proxmox firewall off or on at all levels.
Where am I going wrong? This doesn't make sense to me.
Proxmox network/interfaces
I've been struggling for hours with a strange problem that I don't understand.
I'll try to explain:
I have a VPS server on the Internet with a public IP 178.xxx.xxx.xxx/22.
Proxmox is installed on this server, and it should only be accessible via a VPN connection.
An opnsens is responsible for the vpn connection.
On Proxmox, there is an LXC container running that provides a VPN connection using Wireguard.
This part works.
For example, I can access Proxmox’s web interface or SSH into the LXC container from my local network (10.10.10.0/24).
However, there are some irregularities and certain things don't always work.
Sometimes, after restarting Proxmox, the LXC containers lose internet access.
It seems that the rule for outgoing NAT is not taking effect:
Code:
iptables -t nat -A POSTROUTING -s '192.168.10.0/24' -o ens3 -j MASQUERADEAlthough the rule is loaded, nothing is being routed through it:
Code:
Chain POSTROUTING
pkts bytes target prot opt in out source destination
0 0 MASQUERADE 0 -- * ens3 192.168.10.0/24 0.0.0.0/0That’s one issue. Another is that I can’t reliably SSH into an LXC container at 192.168.10.10.
It works once, but after a few minutes, if I try to open a second session, I get the error:
Network error: Software caused connection abort.
Other SSH sessions—such as to Proxmox directly at 192.168.10.1 or to the Wireguard gateway at 192.168.10.5—always work.
Even accessing the web interface at 192.168.1.1:8006 always works.
If I assign a different IP to the container at 192.168.10.10, it works at first but then stops working after a short time.
I see the same phenomenon with a new container.
What I’ve noticed is that establishing an SSH connection to 192.168.10.10 takes a few seconds longer than to 192.168.10.5 or 192.168.10.1.
During the period when an SSH connection cannot be established, I can still successfully ping the addresses.
Based on the network diagram, this might be easier to understand.
When I track the packages with tcpdump, everything looks good so far.
it also makes no difference whether I switch the proxmox firewall off or on at all levels.
Where am I going wrong? This doesn't make sense to me.
Proxmox network/interfaces
auto lo
iface lo inet loopback
auto ens3
#real IP address
iface ens3 inet static
address 178.xxx.xxx.xxx/22
gateway 178.xxx.xxx.1
#privat sub network
auto vmbr0
iface vmbr0 inet static
address 192.168.10.1/24
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '192.168.10.0/24' -o ens3 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '192.168.10.0/24' -o ens3 -j MASQUERADE
post-up iptables -t nat -A PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64123 -i ens3 -j DNAT --to-destination 192.168.10.5:64123
post-down iptables -t nat -D PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64123 -i ens3 -j DNAT --to-destination 192.168.10.5:64123
post-up iptables -t nat -A PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64000 -i ens3 -j DNAT --to-destination 192.168.10.10:64000
post-down iptables -t nat -D PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64000 -i ens3 -j DNAT --to-destination 192.168.10.10:64000
post-up iptables -t nat -A PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64001 -i ens3 -j DNAT --to-destination 192.168.10.10:64001
post-down iptables -t nat -D PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64001 -i ens3 -j DNAT --to-destination 192.168.10.10:64001
post-up iptables -t raw -I PREROUTING -i fwbr+ -j CT --zone 1
post-down iptables -t raw -D PREROUTING -i fwbr+ -j CT --zone 1
source /etc/network/interfaces.d/*
iface lo inet loopback
auto ens3
#real IP address
iface ens3 inet static
address 178.xxx.xxx.xxx/22
gateway 178.xxx.xxx.1
#privat sub network
auto vmbr0
iface vmbr0 inet static
address 192.168.10.1/24
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '192.168.10.0/24' -o ens3 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '192.168.10.0/24' -o ens3 -j MASQUERADE
post-up iptables -t nat -A PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64123 -i ens3 -j DNAT --to-destination 192.168.10.5:64123
post-down iptables -t nat -D PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64123 -i ens3 -j DNAT --to-destination 192.168.10.5:64123
post-up iptables -t nat -A PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64000 -i ens3 -j DNAT --to-destination 192.168.10.10:64000
post-down iptables -t nat -D PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64000 -i ens3 -j DNAT --to-destination 192.168.10.10:64000
post-up iptables -t nat -A PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64001 -i ens3 -j DNAT --to-destination 192.168.10.10:64001
post-down iptables -t nat -D PREROUTING -p udp -d 178.xxx.xxx.xxx --dport 64001 -i ens3 -j DNAT --to-destination 192.168.10.10:64001
post-up iptables -t raw -I PREROUTING -i fwbr+ -j CT --zone 1
post-down iptables -t raw -D PREROUTING -i fwbr+ -j CT --zone 1
source /etc/network/interfaces.d/*
Last edited: