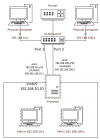
Just install my Proxmox server. My server has a dual Nic. Each nic port is connected to a VLAN switch port that serves two separate VLANs (port 2 for VLAN 10, port 3 for VLAN 100). The topology is below:
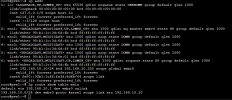
Here is what is on the console
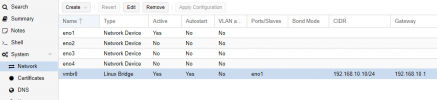
on the GUI
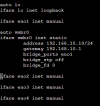
and in the /etc/network/interfaces
I am building VMs for both VLANs. The router will be doing all the routing between the VLANS. Questions I have:
1, Do I need to manually enable eno2? (when there is a link light on the switch.) Do I need to assign an IP address to eno2?
2, Do I need to add a static route for each VLAN on the host?
3. When I try to create a VMBR1 for 192.168.100.x network, the GUL failed and said the GW already exists. How can I make that work?
- can I just copy the VMBR0 config and modify it for the 192.168.100.x network?
Thank you very much for any help. I am new to Proxmox and did not need to do resolve networking when I was using VMware. Just trying to get a sense of what I should be doing.

Here is what is on the console

on the GUI

and in the /etc/network/interfaces

I am building VMs for both VLANs. The router will be doing all the routing between the VLANS. Questions I have:
1, Do I need to manually enable eno2? (when there is a link light on the switch.) Do I need to assign an IP address to eno2?
2, Do I need to add a static route for each VLAN on the host?
3. When I try to create a VMBR1 for 192.168.100.x network, the GUL failed and said the GW already exists. How can I make that work?
- can I just copy the VMBR0 config and modify it for the 192.168.100.x network?
Thank you very much for any help. I am new to Proxmox and did not need to do resolve networking when I was using VMware. Just trying to get a sense of what I should be doing.
Last edited:

