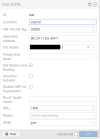
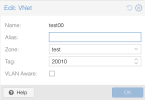
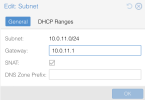
Hi all! I've been playing around with EVPN SDNs. I have SNAT enabled on some Vnets. After some ping tests on containers, 8.8.8.8 is unreachable only once enabling the datacenter firewall. All outbound traffic is accepted by default, not sure if EVPNs require inbound rules to the hosts in order for SNAT to function. I've tried allowing all inbound traffic from the Vnet's subnets, but this didn't work. Also tried explicitly allowing outbound traffic from those subnets, no luck either. Any idea how I could get this working? Thanks in advance!!
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Hi @najimurad,
Have you resolved this issue ?
I'm in the same situation, If I disable DC firewall my CT can ping outside, if I enable it, no ping.
I've tried to create an ACCEPT ALL IN rule but same problem ...
Have you resolved this issue ?
I'm in the same situation, If I disable DC firewall my CT can ping outside, if I enable it, no ping.
I've tried to create an ACCEPT ALL IN rule but same problem ...
Same problem! Even If I delete all firewall rules on the dashboard and set default policy to ACCEPT input, output and forward, once the datacenter firewall is enabled, return traffic cannot reach the VM. The SNAT logic is working fine but the iptables FORWARD rules are blocking the return traffic before it hits the VM
If I add the following in iptables, internet connectivity works:
iptables -I FORWARD 1 -j ACCEPT
But this is obviously too permissive, so is there a bug in the EVPN SNAT firewall implementation? I don't want to be making manual modifications and risk creating a security vulnerability.
If I add the following in iptables, internet connectivity works:
iptables -I FORWARD 1 -j ACCEPT
But this is obviously too permissive, so is there a bug in the EVPN SNAT firewall implementation? I don't want to be making manual modifications and risk creating a security vulnerability.
Last edited:
Have you tried enabling nftables tech preview under each node? I had lots of issues with the firewall with router VMs until I enabled that.
I have EVPN running on my prod cluster using nftables. iptables gave me the same symptoms, return traffic was blocked. I created a thread on that some months back, but just enabling it fixed all my issues. Maybe it's still experimental but worth testing it at minimum.
makes sense and thanks for mentioning. I abandoned EVPN as a result of this issue because it surprised me that the iptables version was broken even though I didn't see any warning that EVPN wasn't ready for production use, although entirely possible I was mistaken on that point. Seemed like EVPN wasn't too actively maintained, and much riskier given my skillset. I will definitely revisit the moment nftables is publicly approved for production use.
Do you have multiple exit nodes? In that case you need to set the rp_filter option, since return traffic can arrive on any exit node. [1]
[1] https://pve.proxmox.com/pve-docs/pve-admin-guide.html#_multiple_evpn_exit_nodes
[1] https://pve.proxmox.com/pve-docs/pve-admin-guide.html#_multiple_evpn_exit_nodes
Back when I was demoing it I had 2 exit nodes with a primary exit node. I tested extensively with different EVPN configurations to resolve this issue. And I set permissive PVE firewall rules. I logged all martian packets and had rp_filter configured. But like I mentioned, it turned out iptables was somehow blocking the forwarding of return traffic (I didn't have any custom iptables rules). And manually setting the following allowed the flow of return traffic "iptables -I FORWARD 1 -j ACCEPT". It's my understanding that iptables and rp_filter have independent logic so the firewall rules were somehow misconfigured. My skillset isn't polished, so it is possible I overlooked something. But I would have thought that EVPN SNAT would work out of the box, somehow that was not the case on my installation.
I did think FRR was approachable and I quite enjoyed learning about both. My issue currently is that every day I take a detour is another day until my app is launched.EVPN was fairly seamless to setup once you understand it, its just FRR under the hood. The documentation though is not really that great, we need lab examples and interop scenarios. We have it working with Dell OS10 switches now and external routing without SNAT.
I agree on the documentation. It's not bad but I would welcome:
- A deep dive video series explaining how Proxmox works under the hood
- A deep dive video series for every new feature release
No need for polish, just a technical guide that's easy to speed through
edit: sorry wrong infoBut I would have thought that EVPN SNAT would work out of the box, somehow that was not the case on my installation.
Ah, I see thanks. I was convinced it was supported. The fact that the UI doesn't hide disabled/irrelevant features can be super confusing at times.
Sorry, I was mistaken - it has been added. I'll take a closer look when the dust on PVE 9 release has settled.