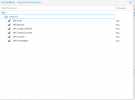
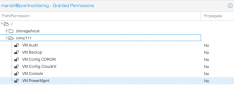
I have created PVE user and its API Token for a user manish@pve in proxmox cluster running version 7. When i assign user permission to VM as attached in screenshot1, the permission are showing with propagate=Yes whereas if I assign token permission to the same VM with same role, it is showing Propagate=No
Now Issue is if I assign only API permission and try to access the VM properties through API call, it is giving me all null and when I assign both user and API to the VM then only API is showing me correct permission
Why this weird behavior??
Now Issue is if I assign only API permission and try to access the VM properties through API call, it is giving me all null and when I assign both user and API to the VM then only API is showing me correct permission
Why this weird behavior??