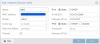
I had been trying to create a private IP (NAT) setup for my VMs and managed to do it as follows, heavily relying on infomation in reference [1]. I have re-titled this as a Tutorial now:
1. In the Proxmox web interface for the host network configuration create a second bridge: vmbr1 with IP address only e.g. 192.168.1.1/24
(Assumes vmbr0 is configured and in use by PVE host already for network access in this example on the 10.140.79.X)
2. On the PVE host node edit using nano /etc/network/interfaces to look like below:
# network interface settings; autogenerated
# Please do NOT modify this file directly, unless you know what
# you're doing.
#
# If you want to manage parts of the network configuration manually,
# please utilize the 'source' or 'source-directory' directives to do
# so.
# PVE will preserve these directives, but will NOT read its network
# configuration from sourced files, so do not attempt to move any of
# the PVE managed interfaces into external files!
auto lo
iface lo inet loopback
iface eth0 inet manual
auto vmbr0
iface vmbr0 inet static
address 10.140.79.120/24
gateway 10.140.79.1
bridge-ports eth0
bridge-stp off
bridge-fd 0
auto vmbr1
iface vmbr1 inet static
address 192.168.1.1/24
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '192.168.1.0/24' -o vmbr0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '192.168.1.0/24' -o vmbr0 -j MASQUERADE
3. Bring up the second (NAT) bridge:
ifup vmbr1
4. On the VM guest edit using nano /etc/network/interfaces to look like below:
auto lo
iface lo inet manual
iface ens18 inet manual
auto vmbr0
iface vmbr0 inet static
address 192.168.1.2
netmask 255.255.255.0
gateway 192.168.1.1
bridge-ports ens18
bridge-stp off
bridge-fd 0
For further virtual machines you can use these ips:
iptables -t nat -A PREROUTING -i vmbr0 -p tcp --dport 3033 -j DNAT --to 192.168.1.2:22
6. SSH onto the VM (via NAT) :
ssh -p 3033 root@ip_of_proxmox_host
7. Make iptables rule perminant (optional)
install iptables-persistent on the PVE host:
sudo apt-get iptables-persistent
Reference: [1] https://cyberpersons.com/2016/07/27/setup-nat-proxmox/
1. In the Proxmox web interface for the host network configuration create a second bridge: vmbr1 with IP address only e.g. 192.168.1.1/24
(Assumes vmbr0 is configured and in use by PVE host already for network access in this example on the 10.140.79.X)
2. On the PVE host node edit using nano /etc/network/interfaces to look like below:
# network interface settings; autogenerated
# Please do NOT modify this file directly, unless you know what
# you're doing.
#
# If you want to manage parts of the network configuration manually,
# please utilize the 'source' or 'source-directory' directives to do
# so.
# PVE will preserve these directives, but will NOT read its network
# configuration from sourced files, so do not attempt to move any of
# the PVE managed interfaces into external files!
auto lo
iface lo inet loopback
iface eth0 inet manual
auto vmbr0
iface vmbr0 inet static
address 10.140.79.120/24
gateway 10.140.79.1
bridge-ports eth0
bridge-stp off
bridge-fd 0
auto vmbr1
iface vmbr1 inet static
address 192.168.1.1/24
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '192.168.1.0/24' -o vmbr0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '192.168.1.0/24' -o vmbr0 -j MASQUERADE
3. Bring up the second (NAT) bridge:
ifup vmbr1
4. On the VM guest edit using nano /etc/network/interfaces to look like below:
auto lo
iface lo inet manual
iface ens18 inet manual
auto vmbr0
iface vmbr0 inet static
address 192.168.1.2
netmask 255.255.255.0
gateway 192.168.1.1
bridge-ports ens18
bridge-stp off
bridge-fd 0
For further virtual machines you can use these ips:
- 192.168.1.3
- 192.168.1.4
- ...
iptables -t nat -A PREROUTING -i vmbr0 -p tcp --dport 3033 -j DNAT --to 192.168.1.2:22
6. SSH onto the VM (via NAT) :
ssh -p 3033 root@ip_of_proxmox_host
7. Make iptables rule perminant (optional)
install iptables-persistent on the PVE host:
sudo apt-get iptables-persistent
Reference: [1] https://cyberpersons.com/2016/07/27/setup-nat-proxmox/
Last edited: