Hello everyone,
I am currently trying proxmox with opnsense as a VM and trying to understand more the VLAN functions und firewall rules. I have made a config and it is working but I am asking myself why some things work and some don't. Maybe one of you can answer them.
1. Why am I able to connect to the firewall and proxmox when my PC on switch port 5 is VLAN 10 untagged but the port 2 (Switch -> proxmox) is tagged VLAN 10?
2. When I put VLAN 10 untagged on port 2 and tagged vlan 20 & 30, I can't connect to the firewall or proxmox anymore.
3. I want to add new WLAN SSIDs called Users (e.g VLAN 11) and Guest (VLAN 12) on the access point. Do I need to add new linux bridges and linux VLANs? If so, do I need to make the bridge vlan aware? And on the opnsense VM: I would have to add the bridges to the network settings and add a VLAN tag (VLAN tag 11 and 12) to them right?
4. In the 192.168.178.0/24 network, the firewall is reachable with its WAN ip-address 192.168.178.254. Isn't this a security risk since it's reachable from the 192.168.178.0/24 network?
5. How does my current setup work when the opnsense VM doesn't have VLAN tag 10,20,30 assigned in the network settings?
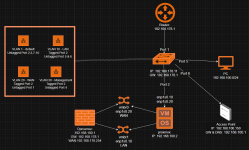
This is my whole setup:
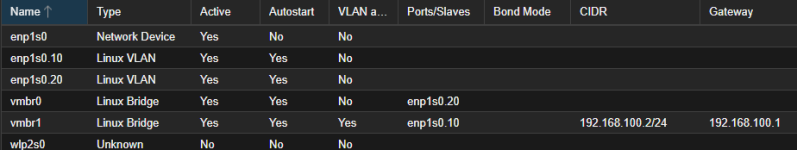
This is my proxmox setup:
/etc/network/interfaces
auto lo
iface lo inet loopback
iface enp1s0 inet manua
liface wlp2s0 inet manual
auto enp1s0.10
iface enp1s0.10 inet manual
#LAN VLAN 10
auto enp1s0.20
iface enp1s0.20 inet manual
#WAN VLAN 20
auto vmbr0
iface vmbr0 inet manual
bridge_ports enp1s0.20
bridge_stp off
bridge_fd 0
#WAN → no IP-Adress
auto vmbr1
iface vmbr1 inet static
address 192.168.100.2
netmask 255.255.255.0
gateway 192.168.100.1
bridge_ports enp1s0.10
bridge_stp off bridge_fd 0
bridge_vlan_aware yes
bridge_vids 2-4094
#LAN → Management-Access
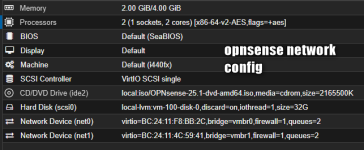
opnsense VM network config:
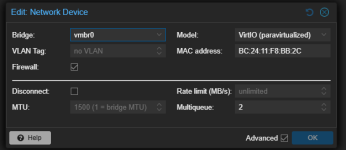
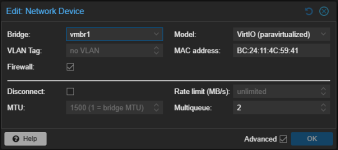
opnsense interface config:
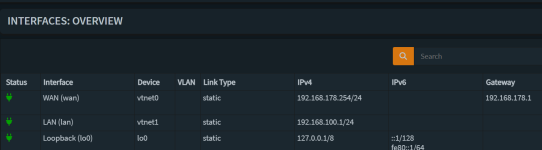
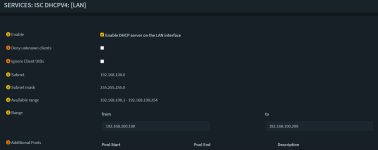
DHCP Config in opnsense:
I have no VLANs in opnsense.
This is my switch VLAN tagging:
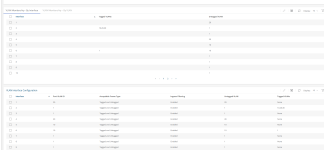
If you need any more information, let me know. Thank you for any help
I am currently trying proxmox with opnsense as a VM and trying to understand more the VLAN functions und firewall rules. I have made a config and it is working but I am asking myself why some things work and some don't. Maybe one of you can answer them.
1. Why am I able to connect to the firewall and proxmox when my PC on switch port 5 is VLAN 10 untagged but the port 2 (Switch -> proxmox) is tagged VLAN 10?
2. When I put VLAN 10 untagged on port 2 and tagged vlan 20 & 30, I can't connect to the firewall or proxmox anymore.
3. I want to add new WLAN SSIDs called Users (e.g VLAN 11) and Guest (VLAN 12) on the access point. Do I need to add new linux bridges and linux VLANs? If so, do I need to make the bridge vlan aware? And on the opnsense VM: I would have to add the bridges to the network settings and add a VLAN tag (VLAN tag 11 and 12) to them right?
4. In the 192.168.178.0/24 network, the firewall is reachable with its WAN ip-address 192.168.178.254. Isn't this a security risk since it's reachable from the 192.168.178.0/24 network?
5. How does my current setup work when the opnsense VM doesn't have VLAN tag 10,20,30 assigned in the network settings?
This is my whole setup:

This is my proxmox setup:
/etc/network/interfaces
auto lo
iface lo inet loopback
iface enp1s0 inet manua
liface wlp2s0 inet manual
auto enp1s0.10
iface enp1s0.10 inet manual
#LAN VLAN 10
auto enp1s0.20
iface enp1s0.20 inet manual
#WAN VLAN 20
auto vmbr0
iface vmbr0 inet manual
bridge_ports enp1s0.20
bridge_stp off
bridge_fd 0
#WAN → no IP-Adress
auto vmbr1
iface vmbr1 inet static
address 192.168.100.2
netmask 255.255.255.0
gateway 192.168.100.1
bridge_ports enp1s0.10
bridge_stp off bridge_fd 0
bridge_vlan_aware yes
bridge_vids 2-4094
#LAN → Management-Access

opnsense VM network config:



opnsense interface config:

DHCP Config in opnsense:
I have no VLANs in opnsense.
This is my switch VLAN tagging:

If you need any more information, let me know. Thank you for any help