Hello! Ive been trying go get IOMMU Groups and PCI-E pass through, mainly GPU, to properly work for quite a while on my new server hardware, my DMAR output looks like this. Thank you in advance and sorry for the long post, this has been a multiweek and multi-reinstall battle
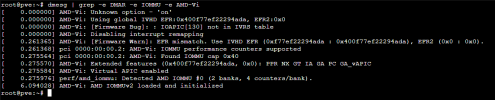
I haven't been able to get Interrupt Remapping to work no matter what I do, Ive tried enabling it in the "iommu_unsafe_interrupts.conf" with
- `echo "options vfio_iommu_type1 allow_unsafe_interrupts=1" > /etc/modprobe.d/iommu_unsafe_interrupts.conf
and also
- echo "Y" > /sys/module/vfio_iommu_type1/parameters/allow_unsafe_interrupts
I have only changed my Grub config to have "amd_iommu=on" and then updated my grub config and thats it, so I don't know if there is anything else that I should do there
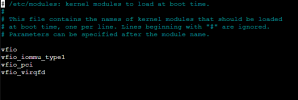
Ive also added these lines to my "etx/modules"
The Main thing that has been bugging me is this, Some PCIE and Boardside devices are getting an IOMMU Group, fully numbered and useable, I can pass through a GbE NIC to any machine, but I cannot pass ANY GPU through to VM, as they have a "-1" iommu group number. I dont know why that is and I would love to have an answer lol.
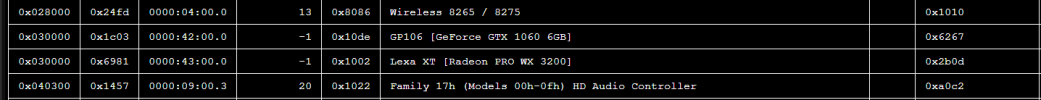
- output from: pvesh get /nodes/pve/hardware/pci --pci-class-blacklist ""
None of these GPU's have any displays plugged into the back of them, they both function as intened when they need to display.
Here are the specs for my machine, The motherboard is at the latest version and it has everything that I can turn on in the AMD CBS Menu turned on that I can have.
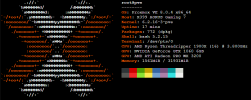
Here is all the relevant history commands wise for what I have tried
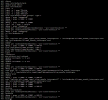

I haven't been able to get Interrupt Remapping to work no matter what I do, Ive tried enabling it in the "iommu_unsafe_interrupts.conf" with
- `echo "options vfio_iommu_type1 allow_unsafe_interrupts=1" > /etc/modprobe.d/iommu_unsafe_interrupts.conf
and also
- echo "Y" > /sys/module/vfio_iommu_type1/parameters/allow_unsafe_interrupts
I have only changed my Grub config to have "amd_iommu=on" and then updated my grub config and thats it, so I don't know if there is anything else that I should do there
Ive also added these lines to my "etx/modules"

The Main thing that has been bugging me is this, Some PCIE and Boardside devices are getting an IOMMU Group, fully numbered and useable, I can pass through a GbE NIC to any machine, but I cannot pass ANY GPU through to VM, as they have a "-1" iommu group number. I dont know why that is and I would love to have an answer lol.

- output from: pvesh get /nodes/pve/hardware/pci --pci-class-blacklist ""
None of these GPU's have any displays plugged into the back of them, they both function as intened when they need to display.
Here are the specs for my machine, The motherboard is at the latest version and it has everything that I can turn on in the AMD CBS Menu turned on that I can have.

Here is all the relevant history commands wise for what I have tried



