Hello there! (Sorry for my bad english)
I am really new to proxmox (and linux in general), I'm not even sure if this is the place I'm supposed to write this.
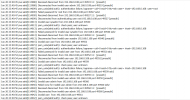
So I installed proxmox a week ago, I plan to set up a NAS and other stuff in the future, but now I only have an Ubuntu VM right now. I try to be as vigiliant as I can be, so I check the syslog every time before I shutdown my server. Things seemed to be pretty okay, but today I saw a few concerning things (the images I attached). This ip (192.168.0.108) belongs to a computer on my network, that my family only uses for stuff like watching youtube and Netflix, because it's an old computer, and we weren't sure if it had a malware or something. Nobody in my family tried to login from that computer, so it's either really infected by something, or I just really misunderstood what these logs say, or how networks work (I'm pretty new to that stuff too).
I've already set up 2fa, and these login attempts tried usernames like "Administrator", "Admin", "Sysadm", "user", etc., so whoever tried to login doesn't even know I'm using proxmox, because then they would've tried to login using root, so I think I should be safe.
How concerned should I be, and what should I do? Should I tighten my security somehow? Should I just simply erase everything from the suspected computer and reinstall an OS from zero, to erase the malware for good?
And since they only tried to login a couple of times, do you think they have the passwords stored on that computer, or they just tried some basic ones like "12345"? (I've never used that computer for anything, so my passwords aren't on it)
I am really new to proxmox (and linux in general), I'm not even sure if this is the place I'm supposed to write this.
So I installed proxmox a week ago, I plan to set up a NAS and other stuff in the future, but now I only have an Ubuntu VM right now. I try to be as vigiliant as I can be, so I check the syslog every time before I shutdown my server. Things seemed to be pretty okay, but today I saw a few concerning things (the images I attached). This ip (192.168.0.108) belongs to a computer on my network, that my family only uses for stuff like watching youtube and Netflix, because it's an old computer, and we weren't sure if it had a malware or something. Nobody in my family tried to login from that computer, so it's either really infected by something, or I just really misunderstood what these logs say, or how networks work (I'm pretty new to that stuff too).
I've already set up 2fa, and these login attempts tried usernames like "Administrator", "Admin", "Sysadm", "user", etc., so whoever tried to login doesn't even know I'm using proxmox, because then they would've tried to login using root, so I think I should be safe.
How concerned should I be, and what should I do? Should I tighten my security somehow? Should I just simply erase everything from the suspected computer and reinstall an OS from zero, to erase the malware for good?
And since they only tried to login a couple of times, do you think they have the passwords stored on that computer, or they just tried some basic ones like "12345"? (I've never used that computer for anything, so my passwords aren't on it)