Hi,
I just downloaded proxmox and am loving it so far, but I cannot, for the life of me, figure out how to mount an exfat drive into an LXC.
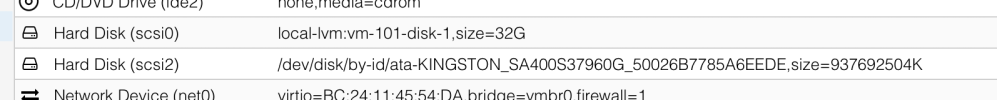
So to start with, I plugged in my external hard drive (formatted as exFAT) and it showed up inside the proxmox gui under the nodes>disks tab.
After this, I opened a shell on the host and navigated to the /dev/disk/by-label and found my drive.
By running mount inside the host I can mount the exfat drive but any user besides the root user is unable to write to the drive (the drive permissions are drwxr-xr-x, and they cannot be changed because it's exfat). So to fix this, I ran mount with the umask=000 option which then set the default permissions of the drive to drwxrwxrwx. Now, any user on my host shell can read and write to the drive. Note: I mounted the drive on the host just to test it, when running the container the host does not have the drive mounted.
Next, I created a Ubuntu 22 lxc (unprivelaged) and added a mount point in the 102.conf file as follows:
mp0: /dev/disk/by-label/mydrive mp=/mnt/nas, backup=0
This successfully added the drive into the lxc container, however, the drive had the old drwxr-xr-x permissions, and the owner was of ID 65534 (nobody:nogroup).
To fix this, I looked up some id mappings of host root to container root, which worked. Also, simply setting the container as privilaged worked too.
However, this came with two problems. One, the root user on the container now either had an ID of 0 or was privileged. And two, additional users on the container still cannot write to the drive because of its permissions.
While looking for other solutions, I also tried creating fstab files which did not work and also tried forwarding the drive entirely using cgroup.allow which also did not work.
Is there any way to forward the umask=000 parameters to the container mountpoint configuration (mp0 = /drive)? If not, is there any proper way to create an ID mapping of root to a group maybe? Because the exfat mount point is mounted as root, it would also work if we could id map the root user to a group on the container which would allow all users in the group write access to the drive?
Tl;dr: exFat drive is mounted with root ownership and no write permissions. Fixing it with id mappings or setting the container to privelaged worked but does not allow multiple users write access.
I just downloaded proxmox and am loving it so far, but I cannot, for the life of me, figure out how to mount an exfat drive into an LXC.
So to start with, I plugged in my external hard drive (formatted as exFAT) and it showed up inside the proxmox gui under the nodes>disks tab.
After this, I opened a shell on the host and navigated to the /dev/disk/by-label and found my drive.
By running mount inside the host I can mount the exfat drive but any user besides the root user is unable to write to the drive (the drive permissions are drwxr-xr-x, and they cannot be changed because it's exfat). So to fix this, I ran mount with the umask=000 option which then set the default permissions of the drive to drwxrwxrwx. Now, any user on my host shell can read and write to the drive. Note: I mounted the drive on the host just to test it, when running the container the host does not have the drive mounted.
Next, I created a Ubuntu 22 lxc (unprivelaged) and added a mount point in the 102.conf file as follows:
mp0: /dev/disk/by-label/mydrive mp=/mnt/nas, backup=0
This successfully added the drive into the lxc container, however, the drive had the old drwxr-xr-x permissions, and the owner was of ID 65534 (nobody:nogroup).
To fix this, I looked up some id mappings of host root to container root, which worked. Also, simply setting the container as privilaged worked too.
However, this came with two problems. One, the root user on the container now either had an ID of 0 or was privileged. And two, additional users on the container still cannot write to the drive because of its permissions.
While looking for other solutions, I also tried creating fstab files which did not work and also tried forwarding the drive entirely using cgroup.allow which also did not work.
Is there any way to forward the umask=000 parameters to the container mountpoint configuration (mp0 = /drive)? If not, is there any proper way to create an ID mapping of root to a group maybe? Because the exfat mount point is mounted as root, it would also work if we could id map the root user to a group on the container which would allow all users in the group write access to the drive?
Tl;dr: exFat drive is mounted with root ownership and no write permissions. Fixing it with id mappings or setting the container to privelaged worked but does not allow multiple users write access.