Preface
Hi together, this thread is highly connected to the issue I explained here: Connected issue
I think it has the same root cause but since I got no answer there I tried to narrow down the problem, reframe it. So now I have a different symptom that is based on a more "common" scenario, that I want to explain in this new thread here. I hope this is ok.
Issue
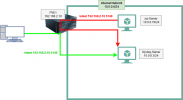
So, here is the overview:
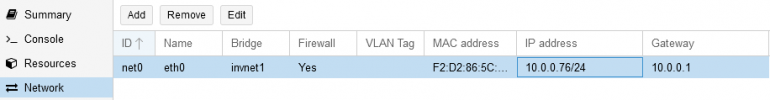
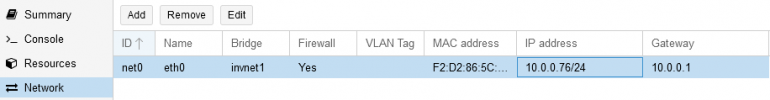
I have a base network (192.168.2.0/24) for PCs etc. where also a PVE node sits and hosts some services in a internal network (10.0.0.0/24) that is SNATed (Gateway = 10.0.0.1). More details down below.
To make services from the internal network available to the outside world I implemented firewall rules via iptables:
Connections from the PC to the syslog server are working fine (the green line).
Connections from another instance of the internal network that are pointing to the public IP address of the PVE node are not working (red line). This is expected so far because I need another rule here to enable loopback/hairpin NAT. Thats the rule I used:
But thats not working too.
When I trace the packet flow this is what I get:
So the packet seems to never reach the point where I can SNAT it to force loopback/hairpin NAT. Do you have any ideas how to troubleshoot this one?
Internal Network
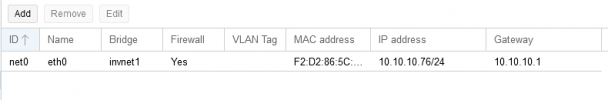
Some more infos to my internal network:
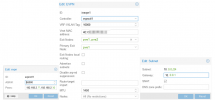
It is realized as EVPN/VNET/SUBNET with SNAT option enabled:
Hi together, this thread is highly connected to the issue I explained here: Connected issue
I think it has the same root cause but since I got no answer there I tried to narrow down the problem, reframe it. So now I have a different symptom that is based on a more "common" scenario, that I want to explain in this new thread here. I hope this is ok.
Issue
So, here is the overview:

I have a base network (192.168.2.0/24) for PCs etc. where also a PVE node sits and hosts some services in a internal network (10.0.0.0/24) that is SNATed (Gateway = 10.0.0.1). More details down below.
To make services from the internal network available to the outside world I implemented firewall rules via iptables:
Code:
iptables -t nat -A PREROUTING -i vmbr0 -p tcp --dport 5140 -j DNAT --to-destination 10.0.0.3:5140Connections from the PC to the syslog server are working fine (the green line).
Connections from another instance of the internal network that are pointing to the public IP address of the PVE node are not working (red line). This is expected so far because I need another rule here to enable loopback/hairpin NAT. Thats the rule I used:
Code:
iptables -t nat -I POSTROUTING -s 10.0.0.3 -p tcp --dport 5140 -j SNAT --to 192.168.2.10But thats not working too.
When I trace the packet flow this is what I get:
Code:
TRACE: raw:PREROUTING:policy:5 IN=vrfbr_inevpn1 MAC=7e:bf:55:eb:01:42:12:79:af:38:d5:b4:08:00 SRC=10.0.0.3 DST=192.168.2.10 LEN=60 TOS=0x10 PREC=0x00 TTL=63 ID=34947 DF PROTO=TCP SPT=41818 DPT=5140 SEQ=1911070483 ACK=0 WINDOW=64860 SYN
TRACE: mangle:PREROUTING:policy:1 IN=vrfbr_inevpn1 MAC=7e:bf:55:eb:01:42:12:79:af:38:d5:b4:08:00 SRC=10.0.0.3 DST=192.168.2.10 LEN=60 TOS=0x10 PREC=0x00 TTL=63 ID=34947 DF PROTO=TCP SPT=41818 DPT=5140 SEQ=1911070483 ACK=0 WINDOW=64860 SYN
TRACE: nat:PREROUTING:policy:10 IN=vrfbr_inevpn1 MAC=7e:bf:55:eb:01:42:12:79:af:38:d5:b4:08:00 SRC=10.0.0.3 DST=192.168.2.10 LEN=60 TOS=0x10 PREC=0x00 TTL=63 ID=34947 DF PROTO=TCP SPT=41818 DPT=5140 SEQ=1911070483 ACK=0 WINDOW=64860 SYN
TRACE: raw:PREROUTING:rule:4 IN=vrf_inevpn1 MAC=7e:bf:55:eb:01:42:12:79:af:38:d5:b4:08:00 SRC=10.0.0.3 DST=192.168.2.10 LEN=60 TOS=0x10 PREC=0x00 TTL=63 ID=34947 DF PROTO=TCP SPT=41818 DPT=5140 SEQ=1911070483 ACK=0 WINDOW=64860 SYN
TRACE: raw:PREROUTING:policy:5 IN=vrf_inevpn1 MAC=7e:bf:55:eb:01:42:12:79:af:38:d5:b4:08:00 SRC=10.0.0.3 DST=192.168.2.10 LEN=60 TOS=0x10 PREC=0x00 TTL=63 ID=34947 DF PROTO=TCP SPT=41818 DPT=5140 SEQ=1911070483 ACK=0 WINDOW=64860 SYN
TRACE: mangle:PREROUTING:policy:1 IN=vrf_inevpn1 MAC=7e:bf:55:eb:01:42:12:79:af:38:d5:b4:08:00 SRC=10.0.0.3 DST=192.168.2.10 LEN=60 TOS=0x10 PREC=0x00 TTL=63 ID=34947 DF PROTO=TCP SPT=41818 DPT=5140 SEQ=1911070483 ACK=0 WINDOW=64860 SYN
TRACE: mangle:INPUT:policy:1 IN=vrf_inevpn1 MAC=7e:bf:55:eb:01:42:12:79:af:38:d5:b4:08:00 SRC=10.0.0.3 DST=192.168.2.10 LEN=60 TOS=0x10 PREC=0x00 TTL=63 ID=34947 DF PROTO=TCP SPT=41818 DPT=5140 SEQ=1911070483 ACK=0 WINDOW=64860 SYN
TRACE: filter:INPUT:policy:3 IN=vrf_inevpn1 MAC=7e:bf:55:eb:01:42:12:79:af:38:d5:b4:08:00 SRC=10.0.0.3 DST=192.168.2.10 LEN=60 TOS=0x10 PREC=0x00 TTL=63 ID=34947 DF PROTO=TCP SPT=41818 DPT=5140 SEQ=1911070483 ACK=0 WINDOW=64860 SYN
TRACE: security:INPUT:policy:1 IN=vrf_inevpn1 MAC=7e:bf:55:eb:01:42:12:79:af:38:d5:b4:08:00 SRC=10.0.0.3 DST=192.168.2.10 LEN=60 TOS=0x10 PREC=0x00 TTL=63 ID=34947 DF PROTO=TCP SPT=41818 DPT=5140 SEQ=1911070483 ACK=0 WINDOW=64860 SYN
TRACE: nat:INPUT:policy:1 IN=vrf_inevpn1 MAC=7e:bf:55:eb:01:42:12:79:af:38:d5:b4:08:00 SRC=10.0.0.3 DST=192.168.2.10 LEN=60 TOS=0x10 PREC=0x00 TTL=63 ID=34947 DF PROTO=TCP SPT=41818 DPT=5140 SEQ=1911070483 ACK=0 WINDOW=64860 SYNSo the packet seems to never reach the point where I can SNAT it to force loopback/hairpin NAT. Do you have any ideas how to troubleshoot this one?
Internal Network
Some more infos to my internal network:
It is realized as EVPN/VNET/SUBNET with SNAT option enabled: