Hello,
I have a weird issue since on proxmox 7.0-14+1 with pcie passthrough that I did not have with proxmox 6.4.
Right now on proxmox 7.0-14+, I am able to pass through a Nvidia GPU without any issues, but when I pass a complete USB hub to the windows VM via pcie passthough I get data corruption and the system becomes read-only giving this error message:
After that the console on the host is spammed with journalctl writting errors.
So here is the chain of events:
1- Vm is off I pass the USB pcie root
2- Turn vm on
3- Host System immediately spam the previous error and everything is dead
4- Hard reboot
5- Boot up and see proxmox login on host
6- Wait 10 seconds
7- Same error and journalctl message spam
The system is now corrupted and no amount of reboot and fsck does anything. I installed the system on two different ssd (different model) and had the same result everytime I tried the pcie passthrough.
Now at this point, I can boot without any issue in rescue mode, but I have no idea what to do to repair what's broken. I tried fsck on /dev/pve/root, but the system complains that the partition is mounted, so I booted a archlinux installation disk and ran it there. No error was found.
I have to admit that I'm a little bit confuse by the LVM setup so I might just be doing things wrong.
Last time, to «resolve» the issue, I just reinstalled the system, but this is hardly a solution.
So I humbly request the forums helps, if anyone has any idea it would be greatly appreciated.
Thanks!
Karl
I have a weird issue since on proxmox 7.0-14+1 with pcie passthrough that I did not have with proxmox 6.4.
Right now on proxmox 7.0-14+, I am able to pass through a Nvidia GPU without any issues, but when I pass a complete USB hub to the windows VM via pcie passthough I get data corruption and the system becomes read-only giving this error message:
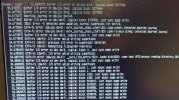
Code:
Buffer I/O error on device dm-5, logical block 5277386
Aborting journal on device dm-5-8.
Buffer I/O error on device dm-5, logical block 3178496, lost sync page write
JBD2: Error -5 detected when updating journal superblock for dm-5-8.
EXT4-fs error (device dm-5): ext4_journal_check_start:83: comm pvesh: Detected aborted journal
EXT4-fs error (device dm-5): ext4_journal_check_start:83: comm rs:main Q:Reg: Detected aborted journal
Buffer I/O error on device dm-5, logical block 0, lost sync page write
EXT4-fs (dm-5): I/O error while writing superblock
EXT4-fs (dm-5): Previous I/O error to superblock detected
EXT4-fs (dm-5): Remounting Filesystem read-only
Buffer I/O error on device dm-5, logical block 0, lost sync page writeAfter that the console on the host is spammed with journalctl writting errors.
So here is the chain of events:
1- Vm is off I pass the USB pcie root
2- Turn vm on
3- Host System immediately spam the previous error and everything is dead
4- Hard reboot
5- Boot up and see proxmox login on host
6- Wait 10 seconds
7- Same error and journalctl message spam
The system is now corrupted and no amount of reboot and fsck does anything. I installed the system on two different ssd (different model) and had the same result everytime I tried the pcie passthrough.
Now at this point, I can boot without any issue in rescue mode, but I have no idea what to do to repair what's broken. I tried fsck on /dev/pve/root, but the system complains that the partition is mounted, so I booted a archlinux installation disk and ran it there. No error was found.
I have to admit that I'm a little bit confuse by the LVM setup so I might just be doing things wrong.
Last time, to «resolve» the issue, I just reinstalled the system, but this is hardly a solution.
So I humbly request the forums helps, if anyone has any idea it would be greatly appreciated.
Thanks!
Karl