Hello, And:
I got: A PVE Cluster, A Managed Switch, And an access port from Core Switch ( That's the point, vlan and turnk will only exist in my private zone).
I want:
- Access PVE WebUI in vlan A
- Put trusted infrastructure like ntp dns in vlan B
- Put shared but trusted software (for dev) like jenkins gitlab in vlan C
- Put untrusted software (wrote by dev) dev/fat/uar/pre in vlan D
- Put untrusted VMs (used by devs playground) in vlan E
The meaning of Vlan is block boardcast, So I can devide trust and untrust zone.
So here is the problem:
If there is no requirement vlanE, I can simply use any config in `https://pve.proxmox.com/wiki/Network_Configuration`. But, Developers will grant root access of guest VM, SO I can't depend on any `configuration in the guest necessary.` solution. If they can do it, It will be an invasion.
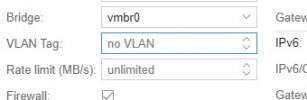
Is this config mean : Give guest an access port and tag the traffic as 8021Q to vmbr0? So the trunk is transparent for guest?
I got: A PVE Cluster, A Managed Switch, And an access port from Core Switch ( That's the point, vlan and turnk will only exist in my private zone).
I want:
- Access PVE WebUI in vlan A
- Put trusted infrastructure like ntp dns in vlan B
- Put shared but trusted software (for dev) like jenkins gitlab in vlan C
- Put untrusted software (wrote by dev) dev/fat/uar/pre in vlan D
- Put untrusted VMs (used by devs playground) in vlan E
The meaning of Vlan is block boardcast, So I can devide trust and untrust zone.
So here is the problem:
If there is no requirement vlanE, I can simply use any config in `https://pve.proxmox.com/wiki/Network_Configuration`. But, Developers will grant root access of guest VM, SO I can't depend on any `configuration in the guest necessary.` solution. If they can do it, It will be an invasion.
Is this config mean : Give guest an access port and tag the traffic as 8021Q to vmbr0? So the trunk is transparent for guest?


