Hello!
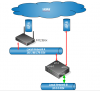
I have setup a network with 2 ISP, 2 gateways, 2 subnets (see attached graphic) on Proxmox VE host.
ISP A is connected to Fritz!Box (router A), ISP B is connected to eth0 of Proxmox VE host (router B).
Subnet A 192.168.178.0/24 with gateway 192.168.178.1 (= router A) is connected to eth1 of Proxmox VE host.
Virtual Bridge vmbr0 is configuring a private network (Subnet B) 10.0.0.0/24 according to instructions of Proxmox Network Model.
Any client in subnet B is routed to 10.0.0.1 (= router B).
Virtual Bridge vmbr1 is configuring the additional default gateway to force any client in subnet 192.168.178.0/24 to be routed to 192.168.178.1.
The routing table is this:
The problem is, that currently any client in subnet A 192.168.178.0/24 cannot ping, ssh another client in subnet B 10.0.0.0/24 and vice versa.
I assume I need another route to fix this.
If this is confirmed, there are two questions:
1. How should the route be defined? From subnet A (192.168.178.0/24) to subnet B (10.0.0.0/24)? Or from subnet B to subnet A?
2. Where must the route be created? On router A (= Fritz!Box) or router B (= Proxmox VE host)?
When I'm connected to Proxmox VE host I can ping, ssh any client in subnet A and subnet B.
THX
I have setup a network with 2 ISP, 2 gateways, 2 subnets (see attached graphic) on Proxmox VE host.
ISP A is connected to Fritz!Box (router A), ISP B is connected to eth0 of Proxmox VE host (router B).
Subnet A 192.168.178.0/24 with gateway 192.168.178.1 (= router A) is connected to eth1 of Proxmox VE host.
Virtual Bridge vmbr0 is configuring a private network (Subnet B) 10.0.0.0/24 according to instructions of Proxmox Network Model.
Any client in subnet B is routed to 10.0.0.1 (= router B).
Virtual Bridge vmbr1 is configuring the additional default gateway to force any client in subnet 192.168.178.0/24 to be routed to 192.168.178.1.
The routing table is this:
Code:
route -n
Kernel-IP-Routentabelle
Ziel Router Genmask Flags Metric Ref Use Iface
0.0.0.0 217.8.50.xx 0.0.0.0 UG 0 0 0 eth0
10.0.0.0 0.0.0.0 255.255.255.0 U 0 0 0 vmbr0
192.168.178.0 0.0.0.0 255.255.255.0 U 0 0 0 vmbr1
217.8.50.xx 0.0.0.0 255.255.255.192 U 0 0 0 eth0
Code:
ip route show
default via 217.8.50.xx dev eth0
10.0.0.0/24 dev vmbr0 proto kernel scope link src 10.0.0.1
192.168.178.0/24 dev vmbr1 proto kernel scope link src 192.168.178.10
217.8.50.xx/26 dev eth0 proto kernel scope link src 217.8.50.xxThe problem is, that currently any client in subnet A 192.168.178.0/24 cannot ping, ssh another client in subnet B 10.0.0.0/24 and vice versa.
I assume I need another route to fix this.
If this is confirmed, there are two questions:
1. How should the route be defined? From subnet A (192.168.178.0/24) to subnet B (10.0.0.0/24)? Or from subnet B to subnet A?
2. Where must the route be created? On router A (= Fritz!Box) or router B (= Proxmox VE host)?
When I'm connected to Proxmox VE host I can ping, ssh any client in subnet A and subnet B.
THX