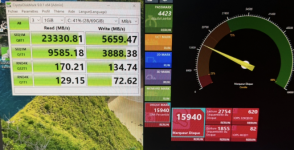
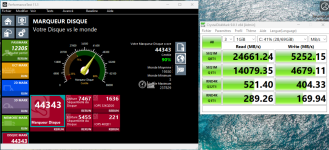
Went from 6.14 (6.14.11-3-pve) to the 6.17 (6.17.2-1-pve) in the pve repository as of right now.
Hardware:
Intel Platform (Vendor: HP)
CPU: i5 13500T
Did a dmesg comparison, discovered these 'differences':
1) In 6.17 I dont see the line 'zbud: loaded' - which I believe has something to do with zswap, although zswap wasn't being used, maybe just an optimization to not load zbud?
2) In 6.17 I dont see the line 'shpchp: Standard Hot Plug PCI Controller Driver version: 0.4', not sure why or what its for.
3)
I noticed a performance drop in the avx bench log output (update below, it seems the first boot after kernel upgrade was busy doing something which had an effect on the kernel log avx-bench report, so not an issue):
6.14:
raid6: avx2x4 gen() 35434 MB/s
raid6: avx2x2 gen() 41273 MB/s
raid6: avx2x1 gen() 40167 MB/s
raid6: using algorithm avx2x2 gen() 41273 MB/s
raid6: .... xor() 29475 MB/s, rmw enabled | 6.17:
raid6: avx2x4 gen() 19637 MB/s
raid6: avx2x2 gen() 22508 MB/s
raid6: avx2x1 gen() 17748 MB/s
raid6: using algorithm avx2x2 gen() 22508 MB/s
raid6: .... xor() 13855 MB/s, rmw enabled |
4) In 6.17 I dont see the line 'AES CTR mode by8 optimization enabled', not sure why.
5) I had to edit some driver code to get it to build in 6.17, there has been a change in hrtimer instantiation method:
C:
// If you get the error:
// error: implicit declaration of function ‘hrtimer_init’; did you mean ‘hrtimers_init’?
//
// The method hrtimer_init has been replaced by hrtimer_setup
// In 6.14:
hrtimer_init(&priv->agg_hrtimer, CLOCK_MONOTONIC, HRTIMER_MODE_REL);
priv->agg_hrtimer.function = dtcet_vnd_tx_agg_timer_cb;
// How to do the above in 6.17+:
hrtimer_setup(&priv->agg_hrtimer, dtcet_vnd_tx_agg_timer_cb, CLOCK_MONOTONIC, HRTIMER_MODE_REL);
I also notice an increase in RAM usage, about 2GB in my setup, obviously this isn't a value that would apply to everyone, but with just an upgrade of kernel the 2gb extra usage was noted. No longer an issue after a subsequent reboot. Seems after the upgrade the first reboot consumes more ram for some reason.
Also I noticed a longer delay in overall boot-time. No longer an issue after a subsequent reboot.
For now I will leave it running, and report back any other issues, but everything seems to be working as before, SRIOV nic vfs to gpu sriov to vfio passthrough gpu, all good.
UPDATE:
Did a hot reboot, now the boot delay is gone, and also the avx bench seems to be in the same ball-park as 6.14:
6.14
raid6: avx2x4 gen() 35434 MB/s
raid6: avx2x2 gen() 41273 MB/s
raid6: avx2x1 gen() 40167 MB/s
raid6: using algorithm avx2x2 gen() 41273 MB/s
raid6: .... xor() 29475 MB/s, rmw enabled | 6.17
raid6: avx2x4 gen() 35648 MB/s
raid6: avx2x2 gen() 40885 MB/s
raid6: avx2x1 gen() 38800 MB/s
raid6: using algorithm avx2x2 gen() 40885 MB/s
raid6: .... xor() 31003 MB/s, rmw enabled |