Hey guys, we experience the same problems at Hetzner with Proxmox machines that already exists many years! It happens exactly since the 04th of september 2021. After doing a tcpdump I could also see incoming traffic for these wrong MAC addresses. And I also have the same setup using a vmbr0 bridge linked to the physical interface. We also use Proxmox firewall. These guys here at reddit also have the same problems since exactly the 04.09.2021.
https://www.reddit.com/r/hetzner/co.../?utm_source=share&utm_medium=web2x&context=3
I have already written many times with the Hetzner Support but they can't help. I'm glad that I found this thread here. I think Hetzner has changed something in their configuration but since we don't get any information we have to deal with it.
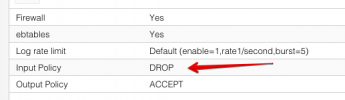
I've read about many solutions here in this thread. What's the most/best one at this time? Currently we're running Proxmox 6 but it should be no problem to upgrade to 7 now. Will this issue be fixed then or do I need to install the patch (deb packages) manually? Do I need further changes? The temporary solution with the Hetzner firewall sounds good and logical to me since this traffic won't get to the machine anymore but it would be also nice to fix this issue directly in Proxmox in the long run.
Best regards from germany