just google "install windows with dism shift+f10". The steps are the same since vista or 7 I thinkCould you please tell me more precisely how you installed Windows 11 without TPM / SecureBoot?
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
I run a VM in Host CPU mode (E5-2650 v2), it does not complain about the CPU, but rather about the missing Secure Boot and TPM 2.0. Updating works well if I remove appraiserres.dll and appraiser.sdb from the source folder.Nope, it doesn't, fails the CPU test. I imagine there's some flags you can set though, haven't looked into it yet.
Or they could wait until current test stuff makes its way into the main release, I imagine it will be soon as W11 compatibility is a big deal.just google "install windows with dism shift+f10". The steps are the same since vista or 7 I think
it's still possible to disable tpm for win11
https://www.tomshardware.com/how-to/bypass-windows-11-tpm-requirement
(and windows server 2022 don't require it : https://www.networkworld.com/articl...ows-11-is-a-non-issue-for-windows-server.html)
https://www.tomshardware.com/how-to/bypass-windows-11-tpm-requirement
(and windows server 2022 don't require it : https://www.networkworld.com/articl...ows-11-is-a-non-issue-for-windows-server.html)
The required packages are already published in the community repo, but there seems to be a issue in it: You need to call upgrade twice as the first call is failing, see below (care: there are two calls to upgrade within it):
Another point: Win11 could be added here:
Bash:
account@host:~$ sudo apt-get update && sudo apt-get -V dist-upgrade
Hit:1 http://ftp.de.debian.org/debian bullseye InRelease
Hit:2 http://ftp.de.debian.org/debian bullseye-updates InRelease
Hit:3 http://security.debian.org bullseye-security InRelease
Hit:4 http://download.proxmox.com/debian/pve bullseye InRelease
Reading package lists... Done
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
Calculating upgrade... Done
The following NEW packages will be installed:
gnutls-bin (3.7.1-5)
libgnutls-dane0 (3.7.1-5)
libjson-glib-1.0-0 (1.6.2-1)
libjson-glib-1.0-common (1.6.2-1)
libopts25 (1:5.18.16-4)
libtpms0 (0.9.0+1)
libunbound8 (1.13.1-1)
swtpm (0.7.0~rc1+1)
swtpm-libs (0.7.0~rc1+1)
swtpm-tools (0.7.0~rc1+1)
The following packages will be upgraded:
libpve-access-control (7.0-4 => 7.0-5)
libpve-common-perl (7.0-9 => 7.0-10)
libpve-http-server-perl (4.0-2 => 4.0-3)
libpve-storage-perl (7.0-11 => 7.0-12)
proxmox-backup-client (2.0.10-1 => 2.0.11-1)
proxmox-backup-file-restore (2.0.10-1 => 2.0.11-1)
pve-edk2-firmware (3.20200531-1 => 3.20210831-1)
pve-manager (7.0-11 => 7.0-13)
qemu-server (7.0-14 => 7.0-16)
9 upgraded, 10 newly installed, 0 to remove and 0 not upgraded.
Need to get 19.8 MB of archives.
After this operation, 157 MB of additional disk space will be used.
Do you want to continue? [Y/n]
Get:1 http://ftp.de.debian.org/debian bullseye/main amd64 libunbound8 amd64 1.13.1-1 [504 kB]
Get:2 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 libpve-common-perl all 7.0-10 [112 kB]
Get:3 http://ftp.de.debian.org/debian bullseye/main amd64 libgnutls-dane0 amd64 3.7.1-5 [394 kB]
Get:4 http://ftp.de.debian.org/debian bullseye/main amd64 libopts25 amd64 1:5.18.16-4 [69.2 kB]
Get:5 http://ftp.de.debian.org/debian bullseye/main amd64 gnutls-bin amd64 3.7.1-5 [647 kB]
Get:6 http://ftp.de.debian.org/debian bullseye/main amd64 libjson-glib-1.0-common all 1.6.2-1 [56.9 kB]
Get:7 http://ftp.de.debian.org/debian bullseye/main amd64 libjson-glib-1.0-0 amd64 1.6.2-1 [65.4 kB]
Get:8 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 libpve-access-control all 7.0-5 [57.4 kB]
Get:9 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 libpve-http-server-perl all 4.0-3 [24.3 kB]
Get:10 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 proxmox-backup-client amd64 2.0.11-1 [2,583 kB]
Get:11 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 proxmox-backup-file-restore amd64 2.0.11-1 [2,651 kB]
Get:12 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 libpve-storage-perl all 7.0-12 [123 kB]
Get:13 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 libtpms0 amd64 0.9.0+1 [316 kB]
Get:14 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 pve-edk2-firmware all 3.20210831-1 [9,703 kB]
Get:15 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 swtpm-libs amd64 0.7.0~rc1+1 [34.1 kB]
Get:16 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 swtpm amd64 0.7.0~rc1+1 [17.5 kB]
Get:17 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 swtpm-tools amd64 0.7.0~rc1+1 [95.9 kB]
Get:18 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 qemu-server amd64 7.0-16 [246 kB]
Get:19 http://download.proxmox.com/debian/pve bullseye/pve-no-subscription amd64 pve-manager amd64 7.0-13 [2,058 kB]
Fetched 19.8 MB in 1s (17.1 MB/s)
Reading changelogs... Done
Selecting previously unselected package libunbound8:amd64.
(Reading database ... 49683 files and directories currently installed.)
Preparing to unpack .../00-libunbound8_1.13.1-1_amd64.deb ...
Unpacking libunbound8:amd64 (1.13.1-1) ...
Selecting previously unselected package libgnutls-dane0:amd64.
Preparing to unpack .../01-libgnutls-dane0_3.7.1-5_amd64.deb ...
Unpacking libgnutls-dane0:amd64 (3.7.1-5) ...
Selecting previously unselected package libopts25:amd64.
Preparing to unpack .../02-libopts25_1%3a5.18.16-4_amd64.deb ...
Unpacking libopts25:amd64 (1:5.18.16-4) ...
Selecting previously unselected package gnutls-bin.
Preparing to unpack .../03-gnutls-bin_3.7.1-5_amd64.deb ...
Unpacking gnutls-bin (3.7.1-5) ...
Selecting previously unselected package libjson-glib-1.0-common.
Preparing to unpack .../04-libjson-glib-1.0-common_1.6.2-1_all.deb ...
Unpacking libjson-glib-1.0-common (1.6.2-1) ...
Selecting previously unselected package libjson-glib-1.0-0:amd64.
Preparing to unpack .../05-libjson-glib-1.0-0_1.6.2-1_amd64.deb ...
Unpacking libjson-glib-1.0-0:amd64 (1.6.2-1) ...
Preparing to unpack .../06-libpve-common-perl_7.0-10_all.deb ...
Unpacking libpve-common-perl (7.0-10) over (7.0-9) ...
Preparing to unpack .../07-libpve-access-control_7.0-5_all.deb ...
Unpacking libpve-access-control (7.0-5) over (7.0-4) ...
Preparing to unpack .../08-libpve-http-server-perl_4.0-3_all.deb ...
Unpacking libpve-http-server-perl (4.0-3) over (4.0-2) ...
Preparing to unpack .../09-proxmox-backup-client_2.0.11-1_amd64.deb ...
Unpacking proxmox-backup-client (2.0.11-1) over (2.0.10-1) ...
Preparing to unpack .../10-proxmox-backup-file-restore_2.0.11-1_amd64.deb ...
Unpacking proxmox-backup-file-restore (2.0.11-1) over (2.0.10-1) ...
Preparing to unpack .../11-libpve-storage-perl_7.0-12_all.deb ...
Unpacking libpve-storage-perl (7.0-12) over (7.0-11) ...
Selecting previously unselected package libtpms0:amd64.
Preparing to unpack .../12-libtpms0_0.9.0+1_amd64.deb ...
Unpacking libtpms0:amd64 (0.9.0+1) ...
Preparing to unpack .../13-pve-edk2-firmware_3.20210831-1_all.deb ...
Unpacking pve-edk2-firmware (3.20210831-1) over (3.20200531-1) ...
Selecting previously unselected package swtpm-libs:amd64.
Preparing to unpack .../14-swtpm-libs_0.7.0~rc1+1_amd64.deb ...
Unpacking swtpm-libs:amd64 (0.7.0~rc1+1) ...
Selecting previously unselected package swtpm.
Preparing to unpack .../15-swtpm_0.7.0~rc1+1_amd64.deb ...
Unpacking swtpm (0.7.0~rc1+1) ...
Selecting previously unselected package swtpm-tools.
Preparing to unpack .../16-swtpm-tools_0.7.0~rc1+1_amd64.deb ...
Unpacking swtpm-tools (0.7.0~rc1+1) ...
Preparing to unpack .../17-qemu-server_7.0-16_amd64.deb ...
Unpacking qemu-server (7.0-16) over (7.0-14) ...
Preparing to unpack .../18-pve-manager_7.0-13_amd64.deb ...
Unpacking pve-manager (7.0-13) over (7.0-11) ...
Setting up proxmox-backup-file-restore (2.0.11-1) ...
Updating file-restore initramfs...
11652 blocks
Setting up libpve-common-perl (7.0-10) ...
Setting up libopts25:amd64 (1:5.18.16-4) ...
Setting up libunbound8:amd64 (1.13.1-1) ...
Setting up proxmox-backup-client (2.0.11-1) ...
Setting up libpve-storage-perl (7.0-12) ...
Setting up libpve-access-control (7.0-5) ...
Setting up libjson-glib-1.0-common (1.6.2-1) ...
Setting up libtpms0:amd64 (0.9.0+1) ...
Setting up libpve-http-server-perl (4.0-3) ...
Setting up pve-edk2-firmware (3.20210831-1) ...
Setting up libgnutls-dane0:amd64 (3.7.1-5) ...
Setting up swtpm-libs:amd64 (0.7.0~rc1+1) ...
Setting up libjson-glib-1.0-0:amd64 (1.6.2-1) ...
Setting up swtpm (0.7.0~rc1+1) ...
Setting up gnutls-bin (3.7.1-5) ...
Setting up swtpm-tools (0.7.0~rc1+1) ...
chown: invalid user: ‘tss:root’
dpkg: error processing package swtpm-tools (--configure):
installed swtpm-tools package post-installation script subprocess returned error exit status 1
dpkg: dependency problems prevent configuration of qemu-server:
qemu-server depends on swtpm-tools; however:
Package swtpm-tools is not configured yet.
dpkg: error processing package qemu-server (--configure):
dependency problems - leaving unconfigured
dpkg: dependency problems prevent configuration of pve-manager:
pve-manager depends on qemu-server (>= 6.2-17); however:
Package qemu-server is not configured yet.
dpkg: error processing package pve-manager (--configure):
dependency problems - leaving unconfigured
dpkg: dependency problems prevent processing triggers for pve-ha-manager:
pve-ha-manager depends on qemu-server (>= 6.0-15); however:
Package qemu-server is not configured yet.
dpkg: error processing package pve-ha-manager (--configure):
dependency problems - leaving triggers unprocessed
Processing triggers for libc-bin (2.31-13) ...
Processing triggers for man-db (2.9.4-2) ...
Errors were encountered while processing:
swtpm-tools
qemu-server
pve-manager
pve-ha-manager
E: Sub-process /usr/bin/dpkg returned an error code (1)
account@host:~$ sudo apt-get update && sudo apt-get -V dist-upgrade
Hit:1 http://ftp.de.debian.org/debian bullseye InRelease
Hit:2 http://ftp.de.debian.org/debian bullseye-updates InRelease
Hit:3 http://security.debian.org bullseye-security InRelease
Hit:4 http://download.proxmox.com/debian/pve bullseye InRelease
Reading package lists... Done
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
Calculating upgrade... Done
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
3 not fully installed or removed.
After this operation, 0 B of additional disk space will be used.
Do you want to continue? [Y/n]
Setting up swtpm-tools (0.7.0~rc1+1) ...
Setting up qemu-server (7.0-16) ...
Setting up pve-manager (7.0-13) ...
Processing triggers for pve-ha-manager (3.3-1) ...Another point: Win11 could be added here:

Last edited:
Thanks for the report, a fixed build of swtpm which ensures the respecive users are created even with reduced dependencies is now available.The required packages are already published in the community repo, but there seems to be a issue in it: You need to call upgrade twice as the first call is failing, see below (care: there are two calls to upgrade within it):
It isn't present in VirtIO ISO builds eitherAnother point: Win11 could be added here:
ostype enum for that to drop some cruft/change some defaults instead of just rendering it in the GUI.Thanks for the report, a fixed build of swtpm which ensures the respecive users are created even with reduced dependencies is now available.
Thanks for the fast fix. There is still an issue:
Code:
Warning: The home dir /var/lib/tpm you specified can't be accessed: No such file or directory
Adding system user `tss' (UID 111) ...
Adding new user `tss' (UID 111) with group `tss' ...
Not creating home directory `/var/lib/tpm'.That is just cosmetic, and it can be ignored, it's a bit of a chicken/egg problem here.Thanks for the fast fix. There is still an issue:
ok, maybe you could avoid the warning when you are usingThat is just cosmetic, and it can be ignored, it's a bit of a chicken/egg problem here.
adduser --system --no-create-home tss internally
Last edited:
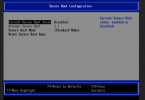
"Attempt Secure Boot" is greyed out. What am I doing wrong? I can't change "Current Secure Boot State" to "Enabled".
This is probably a pre-existing VM I guess? Then it'd be the legacy EFI/EFIvars images.
See https://forum.proxmox.com/threads/v...add-the-vtpm-support.56982/page-3#post-421654 for how to re-create those to get the new variants.
This is probably a pre-existing VM I guess? Then it'd be the legacy EFI/EFIvars images.
See https://forum.proxmox.com/threads/v...add-the-vtpm-support.56982/page-3#post-421654 for how to re-create those to get the new variants.
Thank you. I already did that. I shut down all my VM's (Linux and Windows). I deleted the EFI disks. I added a TPM 2.0 and then added a new EFI Disk using pre-enrolled keys. I restarted the VM's. In the UEFI boot menu I configured the correct start disk. The VM's boot, but none of them recognize the TPM and Secure Boot is not available.
Thank you. I already did that. I shut down all my VM's (Linux and Windows). I deleted the EFI disks. I added a TPM 2.0 and then added a new EFI Disk using pre-enrolled keys. I restarted the VM's. In the UEFI boot menu I configured the correct start disk. The VM's boot, but none of them recognize the TPM and Secure Boot is not available.
Disregard... I need more coffee. I didn't reboot the nodes or migrate the VM's first in order to get them on the newest QEMU build. The packages were updated, but the VM's were running under the old builds.
how did you get it working nested?Setup a nested PVE to test this, my poor 32GB desktop Install is groaning...but it works.
Can confirm TPM works perfect, passing that side of the W11 health test.
Noticed there's a new qemu-server (7.0-16) and efi (3.20210831-1), do they implement the UEFI secure boot as above? if so, can they be retoactively applied to an existing W10 install? not seeing any secure boot options in the UEFI bios for myexisting test W10 VM.
i cant seem to get it to run, i keep getting a message in the vnc console saying 'guest has not initialized the display (yet)'
but the kvm does run and show success
the only logs ive found from syslog is the following 'Oct 07 16:30:36 pve kernel: kvm: vmwrite failed: field=2018 val=0 err=0'
the other thing i have spotted is if change the boot device to BIOS the vm loads the setup iso no problem, but change it back to UEFI, its then stuck with this message?
im running proxmox inside parallels desktop on my mac (proxmox has 8gb, 4 core) (win 11 has 2 core, 4gb)
how did you get it working nested?
i cant seem to get it to run, i keep getting a message in the vnc console saying 'guest has not initialized the display (yet)'
In hardware options for the Win11 VM, if you change the machine type to q35, that resolved the issue for me.
Last edited:
sorry i ment to reply to my message before saying i fixed it haha! it was the q35 indeedIn hardware options if you change the machine type to q35, that resolved the issue for me.
my other issue i now have is the iscsi virtio drivers keep crashing the VM and the VM physically powers off so i have to use SATA instead
the iscsi virtio drivers keep crashing the VM
What version of the drivers?
the latest 0.1.208, i attach the CD to a second drive, run the windows setup, browse drivers, select the scsi one, format blank 64gb drive, then setup does it thing, then half way through, just crashes, and the VM has powered off? very weirdWhat version of the drivers?
Last edited: