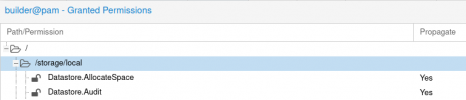
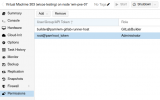
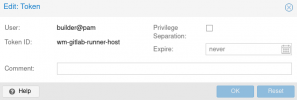
First - I'm doing all with root API-key without limits.
Previously doing with special limited key but not worked too.
What I'm doing? I'm try to insert ISO in virtual CD-ROM.
How I'm doing?
See:
BUT! I can remove ISO from virtual drive easy and it works with unpriveleget limited API-token:
I'm try this with some drives - SCSI, IDE, CDROM - with same effects.
So, from host via
PVE Proxy logs say me
But dismount is OK:
Wat I'm doing wrong?
Previously doing with special limited key but not worked too.
What I'm doing? I'm try to insert ISO in virtual CD-ROM.
How I'm doing?
See:
Code:
~: $ curl --insecure --silent -H "Authorization: PVEAPIToken=$PVEAPIToken" -X POST --data-urlencode scsi1='local:iso/my_iso.iso,media=cdrom' https://$PVEAPINode:8006/api2/json/nodes/$PVETargetNode/qemu/$PVEVMID/config | jq '.'
{
"data": null
}
Code:
~: $ curl --insecure --silent -H "Authorization: PVEAPIToken=$PVEAPIToken" -X POST --data-urlencode scsi1='none' https://$PVEAPINode:8006/api2/json/nodes/$PVETargetNode/qemu/$PVEVMID/config | jq '.'
{
"data": "UPID:wm-pve-01:002523EA:07782A44:6495C95F:qmconfig:303:builder@pam!wm-gitlab-runner-host:"
}I'm try this with some drives - SCSI, IDE, CDROM - with same effects.
So, from host via
pvesh it works perfectly:
Code:
~: # pvesh set /nodes/wm-pve-01/qemu/303/config -scsi1 local:iso/my_iso.iso,media=cdrom
update VM 303: -scsi1 local:iso/my_iso.iso,media=cdromPVE Proxy logs say me
403 Forbidden then try to mount ISO:
Code:
root@pam!root_token [23/06/2023:19:00:53 +0300] "POST /api2/json/nodes/wm-pve-01/qemu/303/config HTTP/1.1" 403 13
Code:
root@pam!root_token [23/06/2023:19:00:50 +0300] "GET /api2/json/nodes/wm-pve-01/qemu/303/status/current HTTP/1.1" 200 1895Wat I'm doing wrong?