[TUTORIAL] Tutorial: Unprivileged LXCs - Mount CIFS shares
- Thread starter TheHellSite
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
I found it rough setting these up with read/write access. Ended up finding a script someone else wrote that makes it easy:
https://gist.github.com/NorkzYT/14449b247dae9ac81ba4664564669299
Make sure the container is running when you run the script. Works great! Cudos to the author.
Too bad its not part of the GUI. Lot of hoops for something I needed to move a lot of VMs to containers.
This worked to a point, but I'm still having issues.
Before I rebooted, I could access the share from within the LXC, I had write access to the root share but I couldn't write to any of the subfolders. If I created a new folder in the root from the LXC, I could write to that. Whilst troubleshooting that I rebooted the host and now it's back up, I can't access the share from the PVE host anymore. The samba NAS runs on the PVE host, it's booted and I can access the shares from my PC, but no matter what, it doesn't seem want to mount it on the host. I just get a No such device error.
This new Proxmox server was supposed to simplify my NAS setup and upgrade it, but I've been working on this for 3 days now and can't even get simple shares working.
This is insanely complicate and for some reason worked for me for 5 minutes to then cripple the container which then would not be accessible anymore, and also is painful, because the container ist manually runtime customized, as Docker itself is way too copmplicated for achieving anything that a template does not come with.  I guess Docker just sucks for any real use. It should not be an issue to add some arbitrary storage ..
I guess Docker just sucks for any real use. It should not be an issue to add some arbitrary storage ..
I ended up running through this guide on setting up direct access to the ZFS without CIFS but also using CIFS for other client connections. https://blog.kye.dev/proxmox-series
Just wanted to say thanks for this guide. It got me up and running when I needed to mount my torrent server and nas to my Sonarr and Radarr containers. I do have a question though. I've done it as cifs in the orginal post and its worked. On the torrent server (windows for the moment) I can see its using SMB 3.1.1 and from the PMV host I can see its connected using cifs version 3.1.1 to both my torrent server and NAS (Synology with SMB3 enabled) however I'm getting slow transfers, about 200mbps. This is over 10Gbps connections (server and switch) to a NAS with 1Gbps. I know this to be ok, as before when my host was hyper-v I had SMB3 muilti path working and was getting 2 maxed out 1Gbps sessions going. I'm not worried about multipath for moment as I have joined the 10Gbps in a lacp trunk .
I'm new to linux and Proxmox so would appicate the help. Would switching the mounting protocol over to smb in the mounting config line work better? Is there anything or any syntax that is needed to be adjusted for this?
I'm new to linux and Proxmox so would appicate the help. Would switching the mounting protocol over to smb in the mounting config line work better? Is there anything or any syntax that is needed to be adjusted for this?
Edit: It's ok. I'm just dumb. JellyFin is quite particular on how you layout the folder structure. Dropping the files straight in to the root directory is not the way to go 
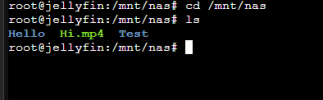
I've done this. In the shell it shows the files in the Mount Point on JellyFin eg: "Hi.mp4" and the Test, Hello folders.
But the issue I have now seems to be JellyFin not showing those folders when you add a media library. It just has /mnt/nas with no sub folders visible?
Also just rolling with it, and doing a Movies library on /mnt/nas, it doesn't show the "Hi.mp4" file in JellyFin.
Showing the SMB files via the mount directory from the guide.
Go to add to library annnd the files and folders don't appear:

But the issue I have now seems to be JellyFin not showing those folders when you add a media library. It just has /mnt/nas with no sub folders visible?
Also just rolling with it, and doing a Movies library on /mnt/nas, it doesn't show the "Hi.mp4" file in JellyFin.
Showing the SMB files via the mount directory from the guide.


Go to add to library annnd the files and folders don't appear:


Last edited:
Hey
I have got this Problem.
Truenas is running with SMB share and I can entry it via my Windows pc.
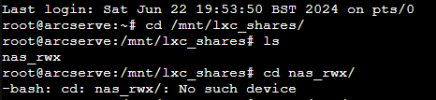
All steps work for me except "mount"
When I use mount "mount /mnt/lxc_shares/nas_rwx" I always get the error: Couldn´t chdir to /mnt/lxc_shares/nas_rwx.
I have created that directory in first place with mdir.
Has anyone got the same problem?
here is a screenshot.
Greetings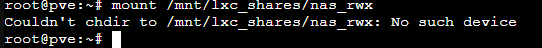
I have got this Problem.
Truenas is running with SMB share and I can entry it via my Windows pc.
All steps work for me except "mount"
When I use mount "mount /mnt/lxc_shares/nas_rwx" I always get the error: Couldn´t chdir to /mnt/lxc_shares/nas_rwx.
I have created that directory in first place with mdir.
Has anyone got the same problem?
here is a screenshot.
Greetings
Now my problem expanded. But i solved the first one.
When I try to mount I get this message:
mount error(16): Device or resource busyRefer to the mount.cifs(8) manual page (e.g. man mount.cifs) and kernel log messages (dmesg)Do I need to turn off my truenas?
When I try to mount I get this message:
mount error(16): Device or resource busyRefer to the mount.cifs(8) manual page (e.g. man mount.cifs) and kernel log messages (dmesg)Do I need to turn off my truenas?
Hi,
thanks for the tutorial, but i am having an issue:
i am getting the "permission denied" error either if I follow this guide or use the script.
On the pve i used this command
the folder gets mountet, as root on the pve I can access, modify and delete files on the samba-share
on the lxc folder I can not access, even as root:
I am assuming that the issue relates to the user and group id, but i am missing the linkage to do that, as described in the beginning of the tutorial:
Is that the reason for the missing permission and, if , how do i configure it?
Thanks
thanks for the tutorial, but i am having an issue:
i am getting the "permission denied" error either if I follow this guide or use the script.
On the pve i used this command
{ echo '' ; echo '# Mount CIFS share on demand with rwx permissions for use in LXCs (manually added)' ; echo '//192.168.2.1/fritz/My_Passport_/ /mnt/lxc_shares/fritz_smb cifs vers=1.0,_netdev,x-systemd.automount,noatime,uid=100000,gid=110000,dir_mode=0770,file_mode=0770,user=smb_client,pass=smb_pass 0 0' ; } | tee -a /etc/fstab{ echo 'mp0: /mnt/lxc_shares/fritz_smb/,mp=/mnt/fritz' ; } | tee -a /etc/pve/lxc/2157.confthe folder gets mountet, as root on the pve I can access, modify and delete files on the samba-share
on the lxc folder I can not access, even as root:
paperless@paperless1310:/mnt$ sudo su[sudo] password for paperless:root@paperless1310:/mnt# lsfritz root@paperless1310:/mnt# cd fritzbash: cd: fritz: Permission deniedls- ergibt:drwxrwx--- 2 nobody nogroup 0 Oct 11 19:57 fritzgetent group paperlesspaperless:x:1000:I am assuming that the issue relates to the user and group id, but i am missing the linkage to do that, as described in the beginning of the tutorial:
PVE host (UID=100000/GID=110000) <--> unprivileged LXC (UID=0/GID=10000)Is that the reason for the missing permission and, if , how do i configure it?
Thanks
Danke, genauso hat es funktioniert. Schade, dass ich diesen Post so spät gefunden habeSince unprivileged LXCs are not allowed to mount CIFS shares and priviliged LXCs are considered unsafe (for a reason) I was scraping my head around how to still have my NAS shares available in my LXCs, f.e. (Jellyfin, Plex, ...).
The solution provided by the Proxmox Wiki would require many changes to the PVE host config, which I was not willing to do.
https://pve.proxmox.com/wiki/Unprivileged_LXC_containers#Using_local_directory_bind_mount_points
Thanks to the following source I was able to assemble a solution that should work for everyone in under 10 minutes.
https://bayton.org/docs/linux/lxd/mount-cifssmb-shares-rw-in-lxd-containers/
How does it work?
By default CIFS shares are mounted as user root(uid=0) and group root(gid=0) on the PVE host which makes them inaccessible to other users,groups and LXCs.
This is because UIDs/GIDs on the PVE host and LXC guests are both starting at 0. But a UID/GID=0 in an unprivileged LXC is actually a UID/GID=100000 on the PVE host. See the above Proxmox Wiki link for more information on this.
@Jason Bayton's solution was to mount the share on the PVE host with the UID/GID of the LXC-User that is going to access the share. While this is working great for a single user it would not work for different LXCs with different users having different UIDs and GIDs. I mean it would work, but then you would have to create a single mount entry for your CIFS share for each UID/GID.
My solution is doing this slightly different and more effective I think.
You simply mount the CIFS share to the UID that belongs to the unprivileged LXC root user, which by default is always uid=100000.
But instead of also mounting it to the GID of the LXC root user, your are going to create a group in your LXC calledlxc_cifs_shareswith a gid=10000 which refers to gid=110000 on the PVE host.
PVE host (UID=100000/GID=110000) <--> unprivileged LXC (UID=0/GID=10000)
How to configure it
1. In the LXC (run commands as root user)
2. On the PVE host (run commands as root user)
- Create the group "lxc_shares" with GID=10000 in the LXC which will match the GID=110000 on the PVE host.
groupadd -g 10000 lxc_shares- Add the user(s) that need access to the CIFS share to the group "lxc_shares".
f.e.: jellyfin, plex, ... (the username depends on the application)
usermod -aG lxc_shares USERNAME- Shutdown the LXC.
- Create the mount point on the PVE host.
mkdir -p /mnt/lxc_shares/nas_rwx- Add NAS CIFS share to
/etc/fstab.
!!! Adjust_netdevForces systemd to consider the mount unit a network mount.
x-systemd.automountAutomatically remounts the CIFS share in case the NAS went offline for some time.
noatimeAccess timestamps are not updated when a file/folder is read.
uid=100000,gid=110000See part "How does it work?" paragraph two for explanation.
dir_mode=0770,file_mode=0770Only that uid/gid will have rwx access to the share. (PVE root user always has rwx to everything.)//NAS/nas/in the middle of the command to match your CIFS hostname (or IP)//NAS/and the share name/nas/. !!!
!!! Adjustuser=smb_username,pass=smb_passwordat the end of the command. !!!
Code:{ echo '' ; echo '# Mount CIFS share on demand with rwx permissions for use in LXCs (manually added)' ; echo '//NAS/nas/ /mnt/lxc_shares/nas_rwx cifs _netdev,x-systemd.automount,noatime,uid=100000,gid=110000,dir_mode=0770,file_mode=0770,user=smb_username,pass=smb_password 0 0' ; } | tee -a /etc/fstab- Mount the share on the PVE host.
mount /mnt/lxc_shares/nas_rwx- Add a bind mount of the share to the LXC config.
!!! Adjust the LXC_ID at the end of the command. !!!
Code:You can mount it in the LXC with read+write+execute (rwx) permissions. { echo 'mp0: /mnt/lxc_shares/nas_rwx/,mp=/mnt/nas' ; } | tee -a /etc/pve/lxc/LXC_ID.conf You can also mount it in the LXC with read-only (ro) permissions. { echo 'mp0: /mnt/lxc_shares/nas_rwx/,mp=/mnt/nas,ro=1' ; } | tee -a /etc/pve/lxc/LXC_ID.conf- Start the LXC.
If you havent solved it already. Old mount is still holding.Now my problem expanded. But i solved the first one.
When I try to mount I get this message:
mount error(16): Device or resource busyRefer to the mount.cifs(8) manual page (e.g. man mount.cifs) and kernel log messages (dmesg)Do I need to turn off my truenas?
Unmount everything, wait a bit, than mount -a - or reboot after dismounting.
This script fixed everything for me.I found it rough setting these up with read/write access. Ended up finding a script someone else wrote that makes it easy:
https://gist.github.com/NorkzYT/14449b247dae9ac81ba4664564669299
Make sure the container is running when you run the script. Works great! Cudos to the author.
Too bad its not part of the GUI. Lot of hoops for something I needed to move a lot of VMs to containers.
Thanks for the share!
Thank you, this did the trick for me (TruNAS VM -> SMB share -> Plex in LXC) <3I found it rough setting these up with read/write access. Ended up finding a script someone else wrote that makes it easy:
https://gist.github.com/NorkzYT/14449b247dae9ac81ba4664564669299
Make sure the container is running when you run the script. Works great! Cudos to the author.
Too bad its not part of the GUI. Lot of hoops for something I needed to move a lot of VMs to containers.
Thanks to @TheHellSite for the tutorial. I have a problem with my installation / homela
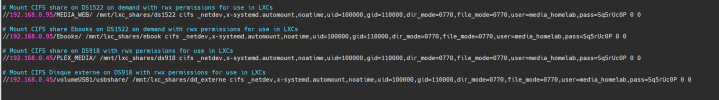
I have two synology NAS, a DS1522 and a DS918.
By following the tutorial, I end up with a problem for the two mounts on my 2nd NAS - user is root (not "10000")... I just don't get it.
On the DS918, l'UID of my user is1029 and GID is100: should i change the step 1?
Thanks a lot !
I have two synology NAS, a DS1522 and a DS918.
- On the DS1522, I have two share folders:
- one share folder that is my maine one, on which the 5/6 LXCs .arr are connected.
- a share folder as catalog for my ebooks
- On the DS918, i have one share folder containing my older media files and one external hard drive.
By following the tutorial, I end up with a problem for the two mounts on my 2nd NAS - user is root (not "10000")... I just don't get it.
On the DS918, l'UID of my user is1029 and GID is100: should i change the step 1?
Thanks a lot !
Attachments
I'm struggling with this as well and found this overall to be really helpful and I had it working for a few days but I recently moved my nas to a new IP and so I needed to make what I expected to be a simple edit. After updating the location no matter what I do I can't seem to access the share by the preferred user. Everything looks right, but the target user doesn't have access. I removed everything and tried adding it back manually but got the same result. I tried using the script referenced by slickdakine thinking that I had missed something but I ended up with the same result. I feel like I'm missing something obvious about the permissions but trying to use chgrp or chown doesn't seem to execute or at least there's no change.
I have no issues on the host mounting and viewing all files on the network share.
My fstab has:
Inside the LXC I have an account called 'dockeruser' and 'myadmin' - right now the myadmin account is the only one that can access.
doing an ls -l in the directory as dockeruser just shows the target directory as having owner and group of myadmin and that's the only user that can access the share. Changing to my dockeruser I have no access even though both are members of the lxc_shares group.
Did I miss something? The GID=110000 should map to the 10000 of the lxc_shares group on the LXC and dockeruser is a member of that group but has no access. I have fully shutdown and restarted both the container and host but no change. I'm confused because this was working just fine but after changing the share ip address it stopped working.
Any ideas on where the permissions are getting tripped up? I feel like this is obvious to someone more experienced.
I have no issues on the host mounting and viewing all files on the network share.
My fstab has:
Code:
//192.168.1.127/storage /mnt/lxc_shares/nas_rwx cifs _netdev,x-systemd.automount,noatime,nobrl,uid=100000,gid=110000,dir_mode=0770,file_mode=0770,username=USERNAME,password=PASS 0 0Inside the LXC I have an account called 'dockeruser' and 'myadmin' - right now the myadmin account is the only one that can access.
Code:
$ id
uid=1001(dockeruser) gid=1001(dockeruser) groups=1001(dockeruser),27(sudo),112(docker),10000(lxc_shares)
$ id myadmin
uid=1000(myadmin) gid=1000(myadmin) groups=1000(myadmin),27(sudo),100(users),10000(lxc_shares)doing an ls -l in the directory as dockeruser just shows the target directory as having owner and group of myadmin and that's the only user that can access the share. Changing to my dockeruser I have no access even though both are members of the lxc_shares group.
Did I miss something? The GID=110000 should map to the 10000 of the lxc_shares group on the LXC and dockeruser is a member of that group but has no access. I have fully shutdown and restarted both the container and host but no change. I'm confused because this was working just fine but after changing the share ip address it stopped working.
Any ideas on where the permissions are getting tripped up? I feel like this is obvious to someone more experienced.