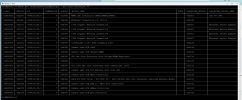
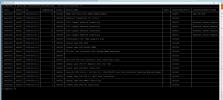
Thank you for the reply! Let me answer you
Are you trying to pass the Quadro or the GeForce? If its the GeForce then you have some problems bc it is not in its own IOMMU group and could be your issue.
I'm trying to pass the GeForce, so that maybe be why I'm having trouble with it... I would prefer not doing the acs_override so I might switch the card places in the end, but before that I'll try to see if the problem is with the ethernet port being named wrongly like seen in
this reddit post.
So lets talk about your PC. What kind of PC is it? How many PCIe slots does it have? Which PCIe slots are the GPUs plugged into? Have you tried to pass one GPU and removed the other one?
I do love talking about my PC

)))))) Ok so the motherboard is a Asus PRIME B460-PLUS ATX with a i7-10700K with a GeForce 3060. It was an gaming PC at first, but I didn't use it a lot so I'm converting it into a little server with a Remote Gaming VM hence all these posts. I added the
Quadro for a future Jellyfin media library to do video transcoding on different LXC which I will do after the pass-through since that is much easier (I think). It had a WIFI PCI adapter on the closest PCIe slot of the CPU, but I recently removed it since I thought that was the problem. Just to clarify, from the CPU socket to the bottom of the board:
1. Wifi (Gigabyte GC-WBAX200) in a PCI slot (I think)
2. Quadro P400 on the 16x PCIe slot (I think)
3. all empty until the second 16x PCIe slot
4. GeForce 3060 on the 16x PCIe slot (if the Quadro is on the 16x slot, then this one is on the one that can run in 4x mode (if that changes anything))
Looking back at the IOMMU grouping, I should swap the GPUs since the Quadro is in its own group. Before installing Proxmox on it, I had the GeForce on the first PCIe 16x slot, but PCPartPicker recommended I put the Quadro on top. I haven't tried passing with only one GPU on the motherboard, but I will try if it comes to it.
UPDATE: The reddit post didn't help since the networking is right.
@spetrillo is right, there's something else in the IOMMU group of the GeForce making it fail. I'm removing the GPU pass-through, swapping the cards and then passing it again to see if it works, I'll let yall know if it works and I'll post my set up