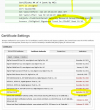
Hello, we are using PMG v 7.1-2
We started using the integrated ACME, but when the certificates are automatically generated, for some reason, they always contain outdated Let's Encrypt R3 certificate chain which expired in 2021.
This means that TLS with our customers stops working every time the certificate is renewed.
We fix the problem by removing the outdated part of the chain in pmg-api.pem and pmg-tls.pem (it always seems to be the last certificate in the file), but we have to do this every time the certificate is renewed.
Why is this happening?
We started using the integrated ACME, but when the certificates are automatically generated, for some reason, they always contain outdated Let's Encrypt R3 certificate chain which expired in 2021.
This means that TLS with our customers stops working every time the certificate is renewed.
We fix the problem by removing the outdated part of the chain in pmg-api.pem and pmg-tls.pem (it always seems to be the last certificate in the file), but we have to do this every time the certificate is renewed.
Why is this happening?