Another thing I would like to add, I was having the same issues with Ventoy and Secure Boot enabled.
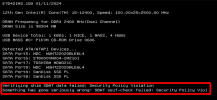
I created a bootable USB using Ventoy (both on Windows and Linux) and was getting exact same shim sbat data failed error.
Digging into the error further, I was able to get the Ventoy USB running with secure boot by replacing a few files in the /EFI/Boot and enrolling the key via MOK Manager.
- mount VTOYEFI partition of ventoy usb. (If you do it on windows, you need to install ventoy as MBR partition and manually assign letter.)
- prepare signed shim (v15.8) files, I got these files from a fedora package (https://kojipkgs.fedoraproject.org/packages/shim/15.8/3/x86_64/shim-x64-15.8-3.x86_64.rpm)
- copy BOOTX64.efi and mmx64.efi from the shim package to /EFI/BOOT in VTOYEFI partition.
- rename grub.efi in /EFI/BOOT as grubx64.efi.
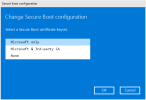
- reboot and enroll ventoy key using mok manager.
Upon installation though, I was unable to boot Proxmox even with the fix for Ventoy. But I figured it was because I was only enrolling the key for Ventoy USB boot and not the Proxmox install

I tried to see if I can find the Proxmox USB directory, but I couldn't find the same directory/files.
Fedora and Debian boots up right away with Secure Boot enabled and all

Right now with the current setup, having to disable, enable, enrolling keys, using a 'hacked up' legacy boot on UEFI Secure Boot, and having no ESP, it feels like I have a Proxmox install that's hanging by a thread waiting for something to go wrong.
Once a fix happens, I'll be more than happy to test it out. Not too sure if Proxmox ever does any betas but I'll be more than happy to try it out.