Hi Proxmoxers out there 
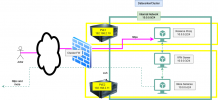
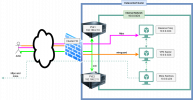
here is an abstraction of what I finally want to achieve in general:
That means:
Please tell me if I need to provide more information. I think more details of what I tried might be misleading at the first place so I want to keep the more abstract view to my problem if that is ok.
here is an abstraction of what I finally want to achieve in general:

That means:
- There is a cluster of at least two PVEs behind a firewall managed by PVE
- An actor should be able to access the PVEs via SSH
- Within the cluster I want to have an internal network
- In general instances in the internal network should be hidden to the outside world (incoming traffic) but should be able to communicate with the outside world (later on only to linux update servers etc. but no restrictions right now at the moment)
- The instances of the internal network are spread all over the nodes and might be migrated from node to node
- An admin and other people should be able to access a reverse proxy that would also serve content from "More Services"
- An admin should be able to access a vpn server to ultimately connect to instances in the internal network via SSH or other protocol
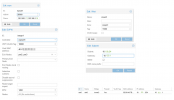
- Giving the admin access to the PVE instances is straight forward using the PVE datacenter and PVE node firewall.
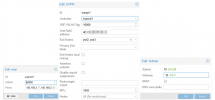
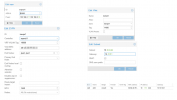
- Building the internal network crossing multiple PVE instances I came across SDNs and more specific VXLANs. Because seperate Linux Bridges on every node would overcomplicate the routing configuration.
- Enabling SDN and creating a VXLAN without specific configuration was simple so far.
- But how does the VXLAN/VNet/PVE nodes/VMs need to be configured that the above scenario applies?
- I would be happy if there is a solution that is independent of an additional gateway/router. It would be the best in my eyes if all the routing can be enabled in the datacenter/node level.
- How can incoming traffic from the internet be routet to the internal networks specific instances?
- How can outgoing traffic from the internal network be routet to the internet?
- Do I need a Subnet within the VNet?
- ...
Please tell me if I need to provide more information. I think more details of what I tried might be misleading at the first place so I want to keep the more abstract view to my problem if that is ok.
Last edited: