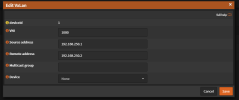
Hello,
we try to build a PVE Cluster with a EVPN VXLAN SDN.
The configuration for the VM to VM Communication is working, also SNAT with the Subnet Gateway is working.
Now we try to replace the subnet gateway with an external OPNsense, so that the OPNsense can provide all required network services (DHCP, NAT, etc.). The idea is to connect the OPNsense with a VXLAN interface to the PVE Hosts to build a Layer 2 network between the VMs and the Firewall.
Is this possible and has someone tried this, because we are currently not able to communicate between a VM and the Firewall?
we try to build a PVE Cluster with a EVPN VXLAN SDN.
The configuration for the VM to VM Communication is working, also SNAT with the Subnet Gateway is working.
Now we try to replace the subnet gateway with an external OPNsense, so that the OPNsense can provide all required network services (DHCP, NAT, etc.). The idea is to connect the OPNsense with a VXLAN interface to the PVE Hosts to build a Layer 2 network between the VMs and the Firewall.
Is this possible and has someone tried this, because we are currently not able to communicate between a VM and the Firewall?