FYI: The next PVE 7.2 (2022/Q2) release will default to QEMU 6.2. Internal testing for that version started in February, and it has been made available on the pvetest repository and used for our production work loads since start of March. Besides some initial regression fixes, we saw no actual new issues coming up.
To upgrade ensure you got valid Proxmox VE repositories configured and then use the standard:
or use the upgrade functionality of the web-interface.
Note, as with all QEMU updates: A VM needs to be either fully restarted (shutdown/start or using restart via the CLI or web-interface) or, to avoid downtime, live-migrated to an already upgraded host to actually run with the newer QEMU version.
While we successfully run our production and lots of testing loads on this version since a while, no software is bug free, and often such issues are related to the specific setup. So, if you run into regressions that are definitively caused by installing the new QEMU version (and not some other change), please always include the affcted VM config and some basic HW and Storage details.
To upgrade ensure you got valid Proxmox VE repositories configured and then use the standard:
Bash:
apt update
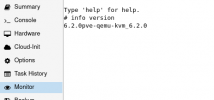
apt full-upgradepveversion -v (or the web-interface's Node Summary -> Packages versions) should then include something like pve-qemu-kvm: 6.2.0-2Note, as with all QEMU updates: A VM needs to be either fully restarted (shutdown/start or using restart via the CLI or web-interface) or, to avoid downtime, live-migrated to an already upgraded host to actually run with the newer QEMU version.
While we successfully run our production and lots of testing loads on this version since a while, no software is bug free, and often such issues are related to the specific setup. So, if you run into regressions that are definitively caused by installing the new QEMU version (and not some other change), please always include the affcted VM config and some basic HW and Storage details.