Hello dear proxmox forum!
TLDR: I want to allow particular MAC through mac filter rule. How I could edit ebtables rule for particular VM, so it will fit ergonomically into pve itself?
I tried searching proxmox forum before creating new thread. Well.. I tried searching internet for this. But looks like I'm alone with this problem
Feel free to correct me at any point, as I'm frontend developer for life, and playing with proxmox / things at my homelab just for fun. BTW, proxmox is awesome, I really love it.
So, my setup is:
* L0 vm is ProxMox itself
* L1 vm is Alpine with docker installed
* L2 is python3 webserver container
For networking,
* ProxMox: vmbr0 to eno1 interface. vmbr0 is VLAN aware; and vmbr.20 is VLAN for all vm's at proxmox
* Alpine: eth1 is tied to vmbr0, with VLAN tag 20
* As for python3-webserver, I want to use macvlan docker network
Macvlan network on docker is tied to vm's eth1 (e.g. parent=eth1), with same subnet, etc.
The problem is, when I try to `docker exec python3 sh` into that container (as root), and try to ping/dig/tracert anything, there is no ... no connection, I guess. It's just timeouting all the things.
Sure, I was testing all things with firewall turned off, just to make sure it's not firewall.
And, turns out, there is mac filtering feature at alpine options. When I turn off this feature, container starts to work normally. I could reach it via my usual router network, just like it's my regular machine. And, of course, ping/dig/tracert inside of container works normally in this case.
I guess, this is called Mac spoofing. Docker container is using different mac, that is assigned to VM, and inputs/outputs network packets with it.
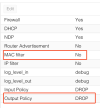
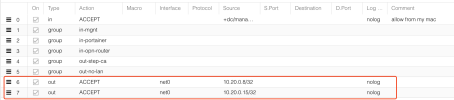
Anyway, I figured out (I don't remember how, may be some link in pve docs), that for mac filtering, ebtables is used.
I started to digging into it, and, indeed, for my VM I see this rule:
```
Bridge chain: veth101i0-OUT, entries: 2, policy: ACCEPT
-s ! bc:24:11:98:44:1d -j DROP
-j ACCEPT
```
I don't want to turn off mac filtering, because I want to keep this layer of security. But I want to edit this ebtables rule, so it will allow me to use mac 02:42:0a:14:00:02, for example.
So, finally, question is : how I could edit ebtables rule for VM, so it will fit ergonomically into pve itself? I mean, I want to do it so things inside of pve will not break: speaking of removing VM, adding new VM, even booting pve and so on.
and so on.
TLDR: I want to allow particular MAC through mac filter rule. How I could edit ebtables rule for particular VM, so it will fit ergonomically into pve itself?
I tried searching proxmox forum before creating new thread. Well.. I tried searching internet for this. But looks like I'm alone with this problem
Feel free to correct me at any point, as I'm frontend developer for life, and playing with proxmox / things at my homelab just for fun. BTW, proxmox is awesome, I really love it.
So, my setup is:
* L0 vm is ProxMox itself
* L1 vm is Alpine with docker installed
* L2 is python3 webserver container
For networking,
* ProxMox: vmbr0 to eno1 interface. vmbr0 is VLAN aware; and vmbr.20 is VLAN for all vm's at proxmox
* Alpine: eth1 is tied to vmbr0, with VLAN tag 20
* As for python3-webserver, I want to use macvlan docker network
Macvlan network on docker is tied to vm's eth1 (e.g. parent=eth1), with same subnet, etc.
The problem is, when I try to `docker exec python3 sh` into that container (as root), and try to ping/dig/tracert anything, there is no ... no connection, I guess. It's just timeouting all the things.
Sure, I was testing all things with firewall turned off, just to make sure it's not firewall.
And, turns out, there is mac filtering feature at alpine options. When I turn off this feature, container starts to work normally. I could reach it via my usual router network, just like it's my regular machine. And, of course, ping/dig/tracert inside of container works normally in this case.
I guess, this is called Mac spoofing. Docker container is using different mac, that is assigned to VM, and inputs/outputs network packets with it.
Anyway, I figured out (I don't remember how, may be some link in pve docs), that for mac filtering, ebtables is used.
I started to digging into it, and, indeed, for my VM I see this rule:
```
Bridge chain: veth101i0-OUT, entries: 2, policy: ACCEPT
-s ! bc:24:11:98:44:1d -j DROP
-j ACCEPT
```
I don't want to turn off mac filtering, because I want to keep this layer of security. But I want to edit this ebtables rule, so it will allow me to use mac 02:42:0a:14:00:02, for example.
So, finally, question is : how I could edit ebtables rule for VM, so it will fit ergonomically into pve itself? I mean, I want to do it so things inside of pve will not break: speaking of removing VM, adding new VM, even booting pve