Hi, I'm new around here and trying to learn Proxmox.
I installed Proxmox on Linux. Everything is very good. In it, I installed Windows Server 2022, as a VM.
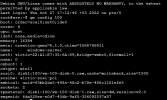
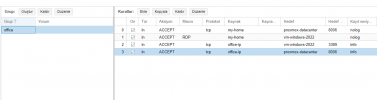
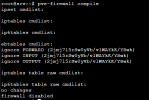
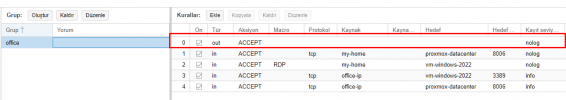
Normally all ports are closed when I activate the firewall.
I open the necessary ports for 8006 and RDP, no problem.
The problem also starts with not being able to access any website in Windows.
In short, there is no internet output from the Windows VM system.
What can be done for this? A different firewall? Or are there rule types for this in Proxmox?
Thanks.
I installed Proxmox on Linux. Everything is very good. In it, I installed Windows Server 2022, as a VM.
Normally all ports are closed when I activate the firewall.
I open the necessary ports for 8006 and RDP, no problem.
The problem also starts with not being able to access any website in Windows.
In short, there is no internet output from the Windows VM system.
What can be done for this? A different firewall? Or are there rule types for this in Proxmox?
Thanks.