Hi all,
As of today I'm running some Raspberry Pi's at home providing some services (nextcloud, mailserver etc.) for me and a few friends(we're running a "art/draw club"). Since I was able to get an old workstation from work and I didn't really cared about security back when I was setting the services up, I would like to run proxmox on the workstation, run the services within vm's on proxmox and establish a secure setup. I'm working as a sysadmin, therefore setting up proxmox isn't a problem at all (working with vmware at work) but my security/networking knowledge aren't as good as they should be. I would like to realize the following setup (based on the various posts within this thread https://forum.proxmox.com/threads/how-to-protect-proxmox-with-a-virtual-virewall.31414/):
- Running a proxmox host behind a virtual pfSense firewall (all traffic from and to the proxmox-host should be routed via the firewall --> except access to proxmox within the lan-zone(see below) )
- Setup a virtual "DMZ" for the services and connect them to the internet via the virtual firewall
- Setup a virtual/physical "LAN" for my private equipment and connect them to the internet via the virtual firewall (and perhaps some internal vm's which shouldn't be accessible from internet)
Below you can find a drawing(much love for https://draw.io ) of what I've got in my mind. I just would like to hear if I'm missing something basically or if I'm on the right way from a theoretical perspective. I know that I would have to do "a lot" of configuration within pfSense (Configure FW-Rules/Port-Forwarding and so on for all services within dmz, setup dhcp/dns for each zone, setup routing between the zones and so on).
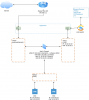
A special thing to note is that the router of my isp isn't supporting a "real bridged"-mode(they say it will be available with one of the next firmware-releases...), instead I can configure a "dmz-ip"(which would be 192.16.1.10 in the above setup). The ISP-Router will then forward all traffic to a client with the configured ip without considering any defined fw-rules/filtering and so on(sounds a bit like ip-passthrough). I know from others that they've got HW-Firewalls to work behind the isp-router like that(including services like voip, so this shouldn't be a problem at all).
There is one more thing which I'm curious about if i look into the future(but I'm quite sure this is not related to proxmox and therefore the worng place to ask but maybe....): I'm thinking about enabling/configuring vpn on the VM0/pfSense instance for remote administration of proxmox and all the vm's. Would i habe to add a new zone (vmbr3, 10.10.30.0/24 for example) within proxmox/pfSense in which the vpn-clients whould live or what is the best way to go ?
Thanks already for any hints/alternative suggestions
As of today I'm running some Raspberry Pi's at home providing some services (nextcloud, mailserver etc.) for me and a few friends(we're running a "art/draw club"). Since I was able to get an old workstation from work and I didn't really cared about security back when I was setting the services up, I would like to run proxmox on the workstation, run the services within vm's on proxmox and establish a secure setup. I'm working as a sysadmin, therefore setting up proxmox isn't a problem at all (working with vmware at work) but my security/networking knowledge aren't as good as they should be. I would like to realize the following setup (based on the various posts within this thread https://forum.proxmox.com/threads/how-to-protect-proxmox-with-a-virtual-virewall.31414/):
- Running a proxmox host behind a virtual pfSense firewall (all traffic from and to the proxmox-host should be routed via the firewall --> except access to proxmox within the lan-zone(see below) )
- Setup a virtual "DMZ" for the services and connect them to the internet via the virtual firewall
- Setup a virtual/physical "LAN" for my private equipment and connect them to the internet via the virtual firewall (and perhaps some internal vm's which shouldn't be accessible from internet)
Below you can find a drawing(much love for https://draw.io ) of what I've got in my mind. I just would like to hear if I'm missing something basically or if I'm on the right way from a theoretical perspective. I know that I would have to do "a lot" of configuration within pfSense (Configure FW-Rules/Port-Forwarding and so on for all services within dmz, setup dhcp/dns for each zone, setup routing between the zones and so on).

A special thing to note is that the router of my isp isn't supporting a "real bridged"-mode(they say it will be available with one of the next firmware-releases...), instead I can configure a "dmz-ip"(which would be 192.16.1.10 in the above setup). The ISP-Router will then forward all traffic to a client with the configured ip without considering any defined fw-rules/filtering and so on(sounds a bit like ip-passthrough). I know from others that they've got HW-Firewalls to work behind the isp-router like that(including services like voip, so this shouldn't be a problem at all).
There is one more thing which I'm curious about if i look into the future(but I'm quite sure this is not related to proxmox and therefore the worng place to ask but maybe....): I'm thinking about enabling/configuring vpn on the VM0/pfSense instance for remote administration of proxmox and all the vm's. Would i habe to add a new zone (vmbr3, 10.10.30.0/24 for example) within proxmox/pfSense in which the vpn-clients whould live or what is the best way to go ?
Thanks already for any hints/alternative suggestions
Last edited:

