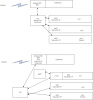
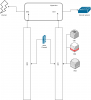
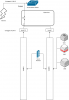
I'm looking to run a virtual FW appliance on ProxMox and would like it to protect all incoming traffic - for the hypervisor and all guests but am not sure how the networking part has to look like. I have attached a drawing of the current situation. Any hints on how to achieve this are very welcome.
At a later stage I'd like outgoing traffic to be also routed through this FW but I guess that would be achieved by simply using the FW as the gateway for the hypervisor + guests?
At a later stage I'd like outgoing traffic to be also routed through this FW but I guess that would be achieved by simply using the FW as the gateway for the hypervisor + guests?