Yes, looks like an error returned from backblaze. But in that case stopping the task and starting again shouldn't clear that?
Proxmox Backup Server 4.0 BETA released!
- Thread starter t.lamprecht
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
It could, as the connection is reset and a new connection established in between backblaze API and PBS s3 client.Yes, looks like an error returned from backblaze. But in that case stopping the task and starting again shouldn't clear that?
Code:
2025-08-14T06:13:04+00:00: verify backblaze:ct/103/2025-04-20T08:28:37Z
2025-08-14T06:13:04+00:00: check pct.conf.blob
2025-08-14T06:13:04+00:00: check root.ppxar.didx
2025-08-14T06:16:48+00:00: "can't verify chunk, load failed - client error (SendRequest)"
2025-08-14T06:16:50+00:00: corrupted chunk renamed to "/mnt/cache/.chunks/9b04/9b0470ce8a908c5695dc83c70f9c13f0aa5d007db5a676b43cf0ea9ef72b9b39.0.bad"Maybe I should change my backblaze account to EU instead of US (I am based in EU and made that account before EU was an option).
this s3 client error should indeed not lead to the locally cached chunk being renamed. This has also been reported in https://bugzilla.proxmox.com/show_bug.cgi?id=6665, please subscribe there to get status updates on this issue.Is that a network error? Or is the chunk actually bad?Code:2025-08-14T06:13:04+00:00: verify backblaze:ct/103/2025-04-20T08:28:37Z 2025-08-14T06:13:04+00:00: check pct.conf.blob 2025-08-14T06:13:04+00:00: check root.ppxar.didx 2025-08-14T06:16:48+00:00: "can't verify chunk, load failed - client error (SendRequest)" 2025-08-14T06:16:50+00:00: corrupted chunk renamed to "/mnt/cache/.chunks/9b04/9b0470ce8a908c5695dc83c70f9c13f0aa5d007db5a676b43cf0ea9ef72b9b39.0.bad"
Maybe I should change my backblaze account to EU instead of US (I am based in EU and made that account before EU was an option).
Hm, did I miss something but do I understand correctly that client-encrypted backups (like described on https://pve.proxmox.com/wiki/Storage:_Proxmox_Backup_Server#storage_pbs_encryption ) are encrypted in any case, even if the first datastore used by the PBS is on a S3 storage? I mean the feature request is about adding server-level encryption (e.g. for encrypting a datastore before offsite replication) while the wiki-page is about client-level encryption.No, this is currently not planned, but given that datastore plain text datastore contents can be synced to a potentially less or un-trusted provider, it could make sense to add an additional server side encryption layer. Note however that there are also server side encryption options for buckets. But do open an enhancement request for this at https://bugzilla.proxmox.com linking this post (the thread itself is to crowded to be liked as a whole).
Yes, client side encrypted snapshots are and will be encrypted also on the s3 backend. As you understood correctly, the request is to add server side encyrption (performed by the PBS host before sending it to S3). Currently unencrypted snapshots are stored in plain text in the s3 bucket, only the transfer is encrypted by using TLS.Hm, did I miss something but do I understand correctly that client-encrypted backups (like described on https://pve.proxmox.com/wiki/Storage:_Proxmox_Backup_Server#storage_pbs_encryption ) are encrypted in any case, even if the first datastore used by the PBS is on a S3 storage? I mean the feature request is about adding server-level encryption (e.g. for encrypting a datastore before offsite replication) while the wiki-page is about client-level encryption.
Hi, I try to mount a S3 bucket from Backblaze, but still have:
access time safety check failed: failed to upload chunk to s3 backend: chunk upload failed: unexpected status code 501 Not Implemented
Proxmox Backup Server is the latest stable, with no subscription
access time safety check failed: failed to upload chunk to s3 backend: chunk upload failed: unexpected status code 501 Not Implemented
Proxmox Backup Server is the latest stable, with no subscription
You need to set theHi, I try to mount a S3 bucket from Backblaze, but still have:
access time safety check failed: failed to upload chunk to s3 backend: chunk upload failed: unexpected status code 501 Not Implemented
Proxmox Backup Server is the latest stable, with no subscription
Skip If-None-Match header in the provider quirks (advanced options for the endpoint create/edit window). Unfortunately not all providers implement the conditional upload.Just got a bunch off:
```
2025-10-02T07:16:30+00:00: chunk 609608675341b0b043b3accb719ab25d5d7a5c7979b72748dc82a7c5f25e7d2d was marked as corrupt
2025-10-02T07:22:13+00:00: <?xml version="1.0" encoding="UTF-8"?>
<Error>
<Code>GatewayTimeout</Code>
<Message>The server did not respond in time.</Message>
<RequestId>N/A</RequestId>
<HostId>N/A</HostId>
</Error>
2025-10-02T07:22:13+00:00: "can't verify chunk, load failed - unexpected status code 504 Gateway Timeout"
```
Definitely something from hetznet but I kind wish it would lead to marking hunks as corrupt so I can retry it?
```
2025-10-02T07:16:30+00:00: chunk 609608675341b0b043b3accb719ab25d5d7a5c7979b72748dc82a7c5f25e7d2d was marked as corrupt
2025-10-02T07:22:13+00:00: <?xml version="1.0" encoding="UTF-8"?>
<Error>
<Code>GatewayTimeout</Code>
<Message>The server did not respond in time.</Message>
<RequestId>N/A</RequestId>
<HostId>N/A</HostId>
</Error>
2025-10-02T07:22:13+00:00: "can't verify chunk, load failed - unexpected status code 504 Gateway Timeout"
```
Definitely something from hetznet but I kind wish it would lead to marking hunks as corrupt so I can retry it?
Should be fixed with https://bugzilla.proxmox.com/show_bug.cgi?id=6665 What version are you running?Just got a bunch off:
```
2025-10-02T07:16:30+00:00: chunk 609608675341b0b043b3accb719ab25d5d7a5c7979b72748dc82a7c5f25e7d2d was marked as corrupt
2025-10-02T07:22:13+00:00: <?xml version="1.0" encoding="UTF-8"?>
<Error>
<Code>GatewayTimeout</Code>
<Message>The server did not respond in time.</Message>
<RequestId>N/A</RequestId>
<HostId>N/A</HostId>
</Error>
2025-10-02T07:22:13+00:00: "can't verify chunk, load failed - unexpected status code 504 Gateway Timeout"
```
Definitely something from hetznet but I kind wish it would lead to marking hunks as corrupt so I can retry it?
Can you please post the full task log? As the error you are showing does not seem to lead to the chunk being renamed incorrectly. See the timestamps and ordering of the log message. Could it be that your chunk with digest 609608675341b0b043b3accb719ab25d5d7a5c7979b72748dc82a7c5f25e7d2d was indeed corrupt or missing?
Thanks for the logs, after having a closer look I noticed that unfortunately the bugfix patch did not make it into proxmox-backup-server 4.0.15. It has been applied since [0], but will not be packaged before 4.0.17-1 or later.Here is my full log.
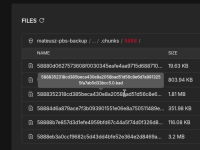
In terms what I found on hetzner s3
View attachment 91261
This is some chunk that was marked corrupted too and it is on my hetzner storage.
[0] https://git.proxmox.com/?p=proxmox-backup.git;a=commit;h=3c350f358e2c2c5513bd87d6ec7bc698677cc7f1
Mine s3.cfg
s3-endpoint: minio-bucket
access-key <minio-username>
endpoint 10.200.5.77
path-style yes
port 9000
secret-key <minio-password>
and datastore.cfg
datastore: minio-ds
backend bucket=mdp,client=minio-bucket,type=s3
path /mnt/datastore
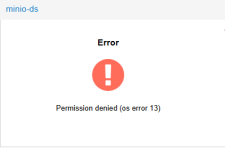
I got error with the bucket like the picture below.
Could you help me with connet to self-hosted minio ?
s3-endpoint: minio-bucket
access-key <minio-username>
endpoint 10.200.5.77
path-style yes
port 9000
secret-key <minio-password>
and datastore.cfg
datastore: minio-ds
backend bucket=mdp,client=minio-bucket,type=s3
path /mnt/datastore
I got error with the bucket like the picture below.
Could you help me with connet to self-hosted minio ?

What is the output ofMine s3.cfg
s3-endpoint: minio-bucket
access-key <minio-username>
endpoint 10.200.5.77
path-style yes
port 9000
secret-key <minio-password>
and datastore.cfg
datastore: minio-ds
backend bucket=mdp,client=minio-bucket,type=s3
path /mnt/datastore
I got error with the bucket like the picture below.
Could you help me with connet to self-hosted minio ?
View attachment 91630
proxmox-backup-manager s3 check minio-bucket mdp executed on the PBS host? How did you create the datastore, is the path /mnt/datastore correct and points to your local datastore cache?proxmox-backup-manager s3 check minio-bucket mdpWhat is the output ofproxmox-backup-manager s3 check minio-bucket mdpexecuted on the PBS host? How did you create the datastore, is the path/mnt/datastorecorrect and points to your local datastore cache?
Error: head object failed
Caused by:
0: client error (Connect)
1: error:0A0000C6:SSL routines:tls_get_more_records
2: error:0A0000C6:SSL routines:tls_get_more_records
i think there a problem with ssl
And the path /mnt/datastore is correct
Okay, so this points towards your TLS setup for the S3 API. Note that PBS requires a TLS encrypted communication, plain text is not supported. You therefore will have to make sure that the certificate is set up correctly on you MinIO, and that you configure the fingerprint on the PBS S3 endpoint in case a self signed certificate is used.proxmox-backup-manager s3 check minio-bucket mdp
Error: head object failed
Caused by:
0: client error (Connect)
1: error:0A0000C6:SSL routines:tls_get_more_recordsacket length too long:../ssl/record/methods/tls_common.c:662:, error:0A000139:SSL routines::record layer failure:../ssl/record/rec_layer_s3.c:696:
2: error:0A0000C6:SSL routines:tls_get_more_recordsacket length too long:../ssl/record/methods/tls_common.c:662:, error:0A000139:SSL routines::record layer failure:../ssl/record/rec_layer_s3.c:696:
i think there a problem with ssl
And the path /mnt/datastore is correct
Further, I'm not sure how you did setup the datastore without the working S3 endpoint connection, but most likely you will have to do that again once the endpoint is working.