Hello,
I just upgraded my PBS to 4.0 and noticed that I'm no longer able to access it through the reverse proxy hosted on the same server (tailscale serve).
After restarting the proxmox-backup-proxy service I can access it via 8007, but even that stops working after I try to open the proxied version in the browser. Accessing the proxied version via curl does not trigger the crash, so I'm assuming it has to do something with one of the assets being fetched.
First load of the proxied host in the browser:
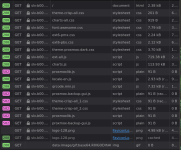
Subsequent loads only generate a 502.
Following this, attempting to access the site via curl also fails:
Restarting the proxmox-backup-proxy service fixes the issue until the next access through the reverse proxy. Accessing the website using the 8007 port works fine and doesn't trigger the crash.
The proxmox-backup-proxy service doesn't seem to log anything at the time of crash, but this error is being repeatedly printed:
FWIW, my ip link output looks like this (MAC addresses obfuscated):
I just upgraded my PBS to 4.0 and noticed that I'm no longer able to access it through the reverse proxy hosted on the same server (tailscale serve).
After restarting the proxmox-backup-proxy service I can access it via 8007, but even that stops working after I try to open the proxied version in the browser. Accessing the proxied version via curl does not trigger the crash, so I'm assuming it has to do something with one of the assets being fetched.
Code:
$ curl https://localhost:8007 -k
<!DOCTYPE html>
(etc.)
$ curl https://<proxied-host>
<!DOCTYPE html>
(etc.)
Subsequent loads only generate a 502.
Following this, attempting to access the site via curl also fails:
Code:
$ curl https://localhost:8007 -k
curl: (56) Recv failure: Connection reset by peerThe proxmox-backup-proxy service doesn't seem to log anything at the time of crash, but this error is being repeatedly printed:
Code:
get_network_interfaces failed - could not deserialize ip link output
Code:
$ ip link
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: enp7s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP mode DEFAULT group default qlen 1000
link/ether 11:22:23:12:55:44 brd ff:ff:ff:ff:ff:ff
altname enx123456
3: enp8s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP mode DEFAULT group default qlen 1000
link/ether 13:12:aa:bb:cc:aa brd ff:ff:ff:ff:ff:ff
altname enx123457
4: tailscale0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1280 qdisc fq_codel state UNKNOWN mode DEFAULT group default qlen 500
link/none
Last edited:

