Hello,
on my pmg (8.1.4) i won´t get dnsbl working on incoming emails.
I need some hints please to figure out where it´s lagging. I a sure i have forgotten something but no idea where.
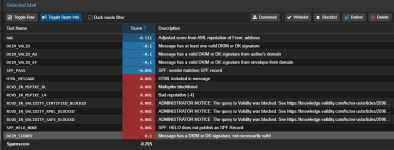
When i toggle the Spam Info - from a Mail in Quarantine - i got following results:
RCVD_IN_DNSWL_BLOCKED --> ADMINISTRATOR NOTICE: The query to DNSWL was blocked. See http://wiki.apache.org/spamassassin/DnsBlocklists\#dnsbl-block
RCVD_IN_VALIDITY_CERTIFIED_BLOCKED --> ADMINISTRATOR NOTICE: The query to Validity was blocked. See https://knowledge.validity.com/hc/en-us/articles/20961730681243 for more information.
RCVD_IN_VALIDITY_RPBL_BLOCKED --> ADMINISTRATOR NOTICE: The query to Validity was blocked. See https://knowledge.validity.com/hc/en-us/articles/20961730681243 for more information.
RCVD_IN_VALIDITY_SAFE_BLOCKED --> ADMINISTRATOR NOTICE: The query to Validity was blocked. See https://knowledge.validity.com/hc/en-us/articles/20961730681243 for more information.
URIBL_BLOCKED --> ADMINISTRATOR NOTICE: The query to DNSWL was blocked. See http://wiki.apache.org/spamassassin/DnsBlocklists\#dnsbl-block
What i have done so far:
Output of the /etc/unbound/unbound.conf.d/pmg-dnsbl.conf. (hint: privatedomain + domain-insecure is used for disabling DNSSec).
server:
do-not-query-localhost: no
# depending on your internal DNS-servers capabilities these options might be necessary
# harden-dnssec-stripped: no
# module-config: "iterator"
private-domain:"INTERNAL-DOMAIN1"
domain-insecure:"INTERNAL-DOMAIN1"
private-domain:"INTERNAL-DOMAIN2"
domain-insecure:"INTERNAL-DOMAIN2"
private-domain:"INTERNAL-DOMAIN3"
domain-insecure:"INTERNAL-DOMAIN3"
private-domain:"INTERNAL-DOMAIN4"
domain-insecure:"INTERNAL-DOMAIN4"
forward-zone:
name: "uceprotect.net"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "mailspike.net"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "sorbs.net"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "bl.spamcop.net"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "spamhaus.org"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "surbl.org"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "uribl.com"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "dnswl.org"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "."
forward-addr: CORRECT-IP-OF-MY-INTERNAL-DNS-SERVER
And generall it seems to work, based on the dig requests:
root@mail:~# dig any test.uribl.com.multi.uribl.com @127.0.0.1 +short
127.0.0.14
"permanent testpoint"
root@mail:~# dig a proxmox.com @127.0.0.1 +short
212.224.123.69
root@mail:~#
Both unbound services are running:
root@mail:~# systemctl status unbound
● unbound.service - Unbound DNS server
Loaded: loaded (/lib/systemd/system/unbound.service; disabled; preset: enabled)
Active: active (running) since Fri 2024-12-06 11:17:07 CET; 24h ago
Docs: man:unbound(8)
Process: 113288 ExecStartPre=/usr/libexec/unbound-helper chroot_setup (code=exited, status=0/SUCCESS)
Process: 113290 ExecStartPre=/usr/libexec/unbound-helper root_trust_anchor_update (code=exited, status=0/SUCCESS)
Main PID: 113292 (unbound)
Tasks: 1 (limit: 4624)
Memory: 11.0M
CPU: 3.223s
CGroup: /system.slice/unbound.service
└─113292 /usr/sbin/unbound -d -p
Dec 06 11:17:07 mail systemd[1]: Starting unbound.service - Unbound DNS server...
Dec 06 11:17:07 mail unbound[113292]: [113292:0] notice: init module 0: subnetcache
Dec 06 11:17:07 mail unbound[113292]: [113292:0] notice: init module 1: validator
Dec 06 11:17:07 mail unbound[113292]: [113292:0] notice: init module 2: iterator
Dec 06 11:17:07 mail unbound[113292]: [113292:0] info: start of service (unbound 1.17.1).
Dec 06 11:17:07 mail systemd[1]: Started unbound.service - Unbound DNS server.
Dec 06 11:17:46 mail unbound[113292]: [113292:0] info: generate keytag query _ta-4f66. NULL IN
Dec 06 23:03:45 mail unbound[113292]: [113292:0] info: generate keytag query _ta-4f66. NULL IN
Dec 07 09:57:38 mail unbound[113292]: [113292:0] info: generate keytag query _ta-4f66. NULL IN
root@mail:~# systemctl status unbound-rbl
● unbound-rbl.service - Unbound DNS server for DNSBL lookups
Loaded: loaded (/etc/systemd/system/unbound-rbl.service; enabled; preset: enabled)
Active: active (running) since Fri 2024-12-06 11:17:11 CET; 24h ago
Docs: man:unbound(8)
Process: 113295 ExecStartPre=/usr/lib/unbound/package-helper chroot_setup (code=exited, status=0/SUCCESS)
Process: 113296 ExecStartPre=/usr/lib/unbound/package-helper root_trust_anchor_update (code=exited, status=0/SUCCESS)
Main PID: 113297 (unbound)
Tasks: 1 (limit: 4624)
Memory: 10.9M
CPU: 1.617s
CGroup: /system.slice/unbound-rbl.service
└─113297 /usr/sbin/unbound -c /etc/unbound/unbound-rbl.conf -d
Dec 06 11:17:11 mail systemd[1]: Starting unbound-rbl.service - Unbound DNS server for DNSBL lookups...
Dec 06 11:17:11 mail (e-helper)[113296]: unbound-rbl.service: Executable /usr/lib/unbound/package-helper missing, skipping: No such file or directory
Dec 06 11:17:11 mail systemd[1]: Started unbound-rbl.service - Unbound DNS server for DNSBL lookups.
Dec 06 11:17:11 mail unbound[113297]: [113297:0] notice: init module 0: subnetcache
Dec 06 11:17:11 mail unbound[113297]: [113297:0] notice: init module 1: validator
Dec 06 11:17:11 mail unbound[113297]: [113297:0] notice: init module 2: iterator
Dec 06 11:17:11 mail unbound[113297]: [113297:0] info: start of service (unbound 1.17.1).
Dec 06 11:17:46 mail unbound[113297]: [113297:0] info: generate keytag query _ta-4f66. NULL IN
Dec 06 22:16:35 mail unbound[113297]: [113297:0] info: generate keytag query _ta-4f66. NULL IN
Dec 07 09:08:38 mail unbound[113297]: [113297:0] info: generate keytag query _ta-4f66. NULL IN
Last but not least, on Configuration - Network/Time --> DNS is only one present: 127.0.0.1
Implementing the local DNS-Server has been done yesterday so quite unlikely that i have matched a rate limit on the dnsbl (even with the activated keys+ip adresses).
Anyone an idea what the issue / problem could be that dnsbl wont work?
Regards
Winni
on my pmg (8.1.4) i won´t get dnsbl working on incoming emails.
I need some hints please to figure out where it´s lagging. I a sure i have forgotten something but no idea where.
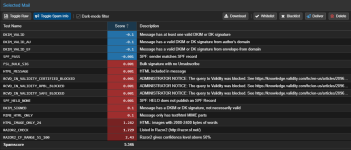
When i toggle the Spam Info - from a Mail in Quarantine - i got following results:
RCVD_IN_DNSWL_BLOCKED --> ADMINISTRATOR NOTICE: The query to DNSWL was blocked. See http://wiki.apache.org/spamassassin/DnsBlocklists\#dnsbl-block
RCVD_IN_VALIDITY_CERTIFIED_BLOCKED --> ADMINISTRATOR NOTICE: The query to Validity was blocked. See https://knowledge.validity.com/hc/en-us/articles/20961730681243 for more information.
RCVD_IN_VALIDITY_RPBL_BLOCKED --> ADMINISTRATOR NOTICE: The query to Validity was blocked. See https://knowledge.validity.com/hc/en-us/articles/20961730681243 for more information.
RCVD_IN_VALIDITY_SAFE_BLOCKED --> ADMINISTRATOR NOTICE: The query to Validity was blocked. See https://knowledge.validity.com/hc/en-us/articles/20961730681243 for more information.
URIBL_BLOCKED --> ADMINISTRATOR NOTICE: The query to DNSWL was blocked. See http://wiki.apache.org/spamassassin/DnsBlocklists\#dnsbl-block
What i have done so far:
- Create SPAMHaus Account and got an Key. Used this Spamhaus URL with key in DNSBL. Configuration - Mailproxy - Options - DNSBL Sites are: bl.spamcop.net,b.barracudacentral.org,MYKEY.zen.dq.spamhaus.net
- Created an Validity.com Account and entered there the public ip of my pmg
- Have done am SPAMHaus Check which was successfull until the DomainBlocklist (which i havent activated)
Output of the /etc/unbound/unbound.conf.d/pmg-dnsbl.conf. (hint: privatedomain + domain-insecure is used for disabling DNSSec).
server:
do-not-query-localhost: no
# depending on your internal DNS-servers capabilities these options might be necessary
# harden-dnssec-stripped: no
# module-config: "iterator"
private-domain:"INTERNAL-DOMAIN1"
domain-insecure:"INTERNAL-DOMAIN1"
private-domain:"INTERNAL-DOMAIN2"
domain-insecure:"INTERNAL-DOMAIN2"
private-domain:"INTERNAL-DOMAIN3"
domain-insecure:"INTERNAL-DOMAIN3"
private-domain:"INTERNAL-DOMAIN4"
domain-insecure:"INTERNAL-DOMAIN4"
forward-zone:
name: "uceprotect.net"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "mailspike.net"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "sorbs.net"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "bl.spamcop.net"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "spamhaus.org"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "surbl.org"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "uribl.com"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "dnswl.org"
forward-addr: 127.0.0.1@5003
forward-zone:
name: "."
forward-addr: CORRECT-IP-OF-MY-INTERNAL-DNS-SERVER
And generall it seems to work, based on the dig requests:
root@mail:~# dig any test.uribl.com.multi.uribl.com @127.0.0.1 +short
127.0.0.14
"permanent testpoint"
root@mail:~# dig a proxmox.com @127.0.0.1 +short
212.224.123.69
root@mail:~#
Both unbound services are running:
root@mail:~# systemctl status unbound
● unbound.service - Unbound DNS server
Loaded: loaded (/lib/systemd/system/unbound.service; disabled; preset: enabled)
Active: active (running) since Fri 2024-12-06 11:17:07 CET; 24h ago
Docs: man:unbound(8)
Process: 113288 ExecStartPre=/usr/libexec/unbound-helper chroot_setup (code=exited, status=0/SUCCESS)
Process: 113290 ExecStartPre=/usr/libexec/unbound-helper root_trust_anchor_update (code=exited, status=0/SUCCESS)
Main PID: 113292 (unbound)
Tasks: 1 (limit: 4624)
Memory: 11.0M
CPU: 3.223s
CGroup: /system.slice/unbound.service
└─113292 /usr/sbin/unbound -d -p
Dec 06 11:17:07 mail systemd[1]: Starting unbound.service - Unbound DNS server...
Dec 06 11:17:07 mail unbound[113292]: [113292:0] notice: init module 0: subnetcache
Dec 06 11:17:07 mail unbound[113292]: [113292:0] notice: init module 1: validator
Dec 06 11:17:07 mail unbound[113292]: [113292:0] notice: init module 2: iterator
Dec 06 11:17:07 mail unbound[113292]: [113292:0] info: start of service (unbound 1.17.1).
Dec 06 11:17:07 mail systemd[1]: Started unbound.service - Unbound DNS server.
Dec 06 11:17:46 mail unbound[113292]: [113292:0] info: generate keytag query _ta-4f66. NULL IN
Dec 06 23:03:45 mail unbound[113292]: [113292:0] info: generate keytag query _ta-4f66. NULL IN
Dec 07 09:57:38 mail unbound[113292]: [113292:0] info: generate keytag query _ta-4f66. NULL IN
root@mail:~# systemctl status unbound-rbl
● unbound-rbl.service - Unbound DNS server for DNSBL lookups
Loaded: loaded (/etc/systemd/system/unbound-rbl.service; enabled; preset: enabled)
Active: active (running) since Fri 2024-12-06 11:17:11 CET; 24h ago
Docs: man:unbound(8)
Process: 113295 ExecStartPre=/usr/lib/unbound/package-helper chroot_setup (code=exited, status=0/SUCCESS)
Process: 113296 ExecStartPre=/usr/lib/unbound/package-helper root_trust_anchor_update (code=exited, status=0/SUCCESS)
Main PID: 113297 (unbound)
Tasks: 1 (limit: 4624)
Memory: 10.9M
CPU: 1.617s
CGroup: /system.slice/unbound-rbl.service
└─113297 /usr/sbin/unbound -c /etc/unbound/unbound-rbl.conf -d
Dec 06 11:17:11 mail systemd[1]: Starting unbound-rbl.service - Unbound DNS server for DNSBL lookups...
Dec 06 11:17:11 mail (e-helper)[113296]: unbound-rbl.service: Executable /usr/lib/unbound/package-helper missing, skipping: No such file or directory
Dec 06 11:17:11 mail systemd[1]: Started unbound-rbl.service - Unbound DNS server for DNSBL lookups.
Dec 06 11:17:11 mail unbound[113297]: [113297:0] notice: init module 0: subnetcache
Dec 06 11:17:11 mail unbound[113297]: [113297:0] notice: init module 1: validator
Dec 06 11:17:11 mail unbound[113297]: [113297:0] notice: init module 2: iterator
Dec 06 11:17:11 mail unbound[113297]: [113297:0] info: start of service (unbound 1.17.1).
Dec 06 11:17:46 mail unbound[113297]: [113297:0] info: generate keytag query _ta-4f66. NULL IN
Dec 06 22:16:35 mail unbound[113297]: [113297:0] info: generate keytag query _ta-4f66. NULL IN
Dec 07 09:08:38 mail unbound[113297]: [113297:0] info: generate keytag query _ta-4f66. NULL IN
Last but not least, on Configuration - Network/Time --> DNS is only one present: 127.0.0.1
Implementing the local DNS-Server has been done yesterday so quite unlikely that i have matched a rate limit on the dnsbl (even with the activated keys+ip adresses).
Anyone an idea what the issue / problem could be that dnsbl wont work?
Regards
Winni
Last edited: