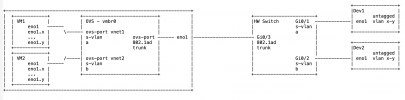
We try to crossconnect traffic from external devices into VMs running on pve. The external devices operate with untagged and vlan-tagged traffic. The VMs are supposed to receive the traffic the same way - untagged and tagged. The VMs have proper vlan configs "inside" to receive the traffic properly.
Since there are several devices out there using all untagged traffic and the same vlan IDs it requires to tunnel the traffic from the switch port, where the devices connect to, to the VM. There is a 1:1 mapping between device ports and ports at the VM.
I tried to configure a OVS bridge associated with the physical port connetced to the external switch. Then I defined a SDN zone. The zone required a s-valn tag. Then I configured a vnet associated with the zone. This vnet requires a tag. I'm confused about this because in essense the vnet is supposed to be a .1q trunk for tagged and untagged traffic.
The documentation is to me also very confusing.
May I ask for your advice?
TIA
Since there are several devices out there using all untagged traffic and the same vlan IDs it requires to tunnel the traffic from the switch port, where the devices connect to, to the VM. There is a 1:1 mapping between device ports and ports at the VM.
I tried to configure a OVS bridge associated with the physical port connetced to the external switch. Then I defined a SDN zone. The zone required a s-valn tag. Then I configured a vnet associated with the zone. This vnet requires a tag. I'm confused about this because in essense the vnet is supposed to be a .1q trunk for tagged and untagged traffic.
The documentation is to me also very confusing.
May I ask for your advice?
TIA