Hey there!
I have been scavenging the internet without a result for my problem - not even chatgpt could help...
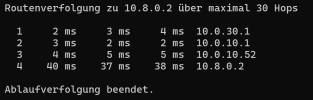
I have OpenVPN setup in an LXC Container in Proxmox and am able to use/connect to it with an external vpn-client, however the connected Client can't connect to any external or internal destinations. It's setup with this instruction https://pve.proxmox.com/wiki/OpenVPN_in_LXC (with debian 12.2.1). I am able to reach any destination from 10.0.10.52 but not from 10.8.0.X even though I created a tunnel-interface and actived it for the unpriviledged CT...
The Network:
Gateway: 10.0.10.1
Proxmox: 10.0.10.12
OpenVPN-Container: 10.0.10.52
OpenVPN-Subpool: 10.8.0.0/24
lxc OpenVPN-Container.conf
the last 2 entries are from a YT-Tutorial... added after it didn't work.
ip -c a
route (net-tools)
Kernel IP routing table
Do you have any ideas?
I have been scavenging the internet without a result for my problem - not even chatgpt could help...
I have OpenVPN setup in an LXC Container in Proxmox and am able to use/connect to it with an external vpn-client, however the connected Client can't connect to any external or internal destinations. It's setup with this instruction https://pve.proxmox.com/wiki/OpenVPN_in_LXC (with debian 12.2.1). I am able to reach any destination from 10.0.10.52 but not from 10.8.0.X even though I created a tunnel-interface and actived it for the unpriviledged CT...
The Network:
Gateway: 10.0.10.1
Proxmox: 10.0.10.12
OpenVPN-Container: 10.0.10.52
OpenVPN-Subpool: 10.8.0.0/24
lxc OpenVPN-Container.conf
Code:
arch: amd64
cores: 4
features: nesting=1
hostname: pveVPN
memory: 1024
net0: name=eth0,bridge=vmbr0,firewall=1,gw=10.0.10.1,hwaddr=BC:24:11:56:65:12,ip=10.0.10.52/24,rate=0,type=veth
onboot: 1
ostype: debian
rootfs: local-lvm:vm-101-disk-0,size=12G
swap: 1024
unprivileged: 1
lxc.cgroup.devices.allow: c 10:200 rwm
lxc.cgroup2.devices.allow: c 10:200 rwm
lxc.mount.entry: /dev/net dev/net none bind,create=dir
lxc.mount.entry: /dev/net/tun dev/net/tun none bind,create=fileip -c a
Code:
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: eth0@if25: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether bc:24:11:56:65:12 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 10.0.10.52/24 brd 10.0.10.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::be24:11ff:fe56:6512/64 scope link
valid_lft forever preferred_lft forever
974: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN group default qlen 500
link/none
inet 10.8.0.1/24 scope global tun0
valid_lft forever preferred_lft forever
inet6 fe80::48c8:8711:bb4a:b841/64 scope link stable-privacy
valid_lft forever preferred_lft foreverroute (net-tools)
Kernel IP routing table
Code:
Destination Gateway Genmask Flags Metric Ref Use Iface
default 10.0.10.1 0.0.0.0 UG 0 0 0 eth0
10.0.10.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
10.8.0.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0Do you have any ideas?