Feel free to ignore all of this, it turned out to be a lack of bridge configuration on my router.
Hi, I have two nodes in a cluster. Both see each other and so do the VMs/CTs. This has been a testing bed and now I'm ready to move on with segmenting the different (future) services. So I'm trying to get this to work on a single node for now. Not even testing both, yet... I would really appreciate some more experienced eyes on this. I've been reading all the things I can find on the subject, but nothing seems thorough enough for my dense head!
I tried configuring a VLAN Zone:
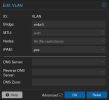
With several VNETs:
They have several different types of Subnets configured. Some with combinations of SNAT, DNS Prefix, DHCP Ranges, or nothing...
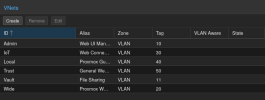
I then set the VM Bridges to the VNETs:
Also leaving the original vmbr0 bridge (tried both with and without this Network Device).
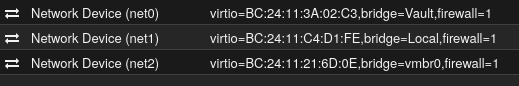
None of this seems to be working as I get no IPs assigned to the VM. I'm pretty sure I'm missing something very basic, but not even the original Network Device configuration (net2) seems to work anymore.
Hi, I have two nodes in a cluster. Both see each other and so do the VMs/CTs. This has been a testing bed and now I'm ready to move on with segmenting the different (future) services. So I'm trying to get this to work on a single node for now. Not even testing both, yet... I would really appreciate some more experienced eyes on this. I've been reading all the things I can find on the subject, but nothing seems thorough enough for my dense head!
I tried configuring a VLAN Zone:

With several VNETs:
They have several different types of Subnets configured. Some with combinations of SNAT, DNS Prefix, DHCP Ranges, or nothing...

I then set the VM Bridges to the VNETs:
Also leaving the original vmbr0 bridge (tried both with and without this Network Device).

None of this seems to be working as I get no IPs assigned to the VM. I'm pretty sure I'm missing something very basic, but not even the original Network Device configuration (net2) seems to work anymore.

Code:
root@pod:~# cat /etc/pve/qemu-server/108.conf
balloon: 0
boot: order=scsi0;ide2;net0
cores: 1
cpu: x86-64-v2-AES
ide2: local:iso/openmediavault_7.0-32-amd64.iso,media=cdrom,size=936M
memory: 4096
meta: creation-qemu=8.1.5,ctime=1711512403
name: vault
net0: virtio=BC:24:11:3A:02:C3,bridge=Vault,firewall=1
net1: virtio=BC:24:11:C4:D1:FE,bridge=Local,firewall=1
net2: virtio=BC:24:11:21:6D:0E,bridge=vmbr0,firewall=1
numa: 0
onboot: 1
ostype: l26
scsi0: btr-vault:108/vm-108-disk-0.raw,iothread=1,size=6G
scsi1: btr-vault:108/vm-108-disk-1.raw,iothread=1,size=3000G,ssd=1
scsihw: virtio-scsi-single
smbios1: uuid=90ecca58-84b0-41ed-9a62-e6044da2638a
sockets: 1
startup: order=1,up=10
vmgenid: 9f2f687b-40e2-45f2-b39c-e397d2017745
Code:
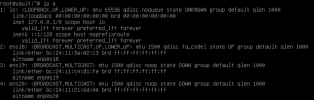
root@pod:~# cat /etc/network/interfaces
# network interface settings; autogenerated
# Please do NOT modify this file directly, unless you know what
# you're doing.
#
# If you want to manage parts of the network configuration manually,
# please utilize the 'source' or 'source-directory' directives to do
# so.
# PVE will preserve these directives, but will NOT read its network
# configuration from sourced files, so do not attempt to move any of
# the PVE managed interfaces into external files!
auto lo
iface lo inet loopback
iface enp4s0 inet manual
auto vmbr0
iface vmbr0 inet static
address 192.168.1.100/16
gateway 192.168.1.1
bridge-ports enp4s0
bridge-stp off
bridge-fd 0
iface wlo1 inet manual
source /etc/network/interfaces.d/*
Code:
source /etc/network/interfaces.d/*
root@pod:~# cat /etc/network/interfaces.d/sdn
#version:25
auto Admin
iface Admin
bridge_ports ln_Admin
bridge_stp off
bridge_fd 0
alias Web UI Management
auto IoT
iface IoT
bridge_ports ln_IoT
bridge_stp off
bridge_fd 0
alias Web Connected IoT
auto Local
iface Local
bridge_ports ln_Local
bridge_stp off
bridge_fd 0
alias Proxmox Guests Only
auto Trust
iface Trust
bridge_ports ln_Trust
bridge_stp off
bridge_fd 0
alias General Web Access
auto Vault
iface Vault
bridge_ports ln_Vault
bridge_stp off
bridge_fd 0
alias File Sharing
auto Wide
iface Wide
bridge_ports ln_Wide
bridge_stp off
bridge_fd 0
alias Proxmox Web Access
auto ln_Admin
iface ln_Admin
link-type veth
veth-peer-name pr_Admin
auto ln_IoT
iface ln_IoT
link-type veth
veth-peer-name pr_IoT
auto ln_Local
iface ln_Local
link-type veth
veth-peer-name pr_Local
auto ln_Trust
iface ln_Trust
link-type veth
veth-peer-name pr_Trust
auto ln_Vault
iface ln_Vault
link-type veth
veth-peer-name pr_Vault
auto ln_Wide
iface ln_Wide
link-type veth
veth-peer-name pr_Wide
auto pr_Admin
iface pr_Admin
link-type veth
veth-peer-name ln_Admin
auto pr_IoT
iface pr_IoT
link-type veth
veth-peer-name ln_IoT
auto pr_Local
iface pr_Local
link-type veth
veth-peer-name ln_Local
auto pr_Trust
iface pr_Trust
link-type veth
veth-peer-name ln_Trust
auto pr_Vault
iface pr_Vault
link-type veth
veth-peer-name ln_Vault
auto pr_Wide
iface pr_Wide
link-type veth
veth-peer-name ln_Wide
auto vmbr0v10
iface vmbr0v10
bridge_ports enp4s0.10 pr_Admin
bridge_stp off
bridge_fd 0
auto vmbr0v11
iface vmbr0v11
bridge_ports enp4s0.11 pr_Vault
bridge_stp off
bridge_fd 0
auto vmbr0v20
iface vmbr0v20
bridge_ports enp4s0.20 pr_Wide
bridge_stp off
bridge_fd 0
auto vmbr0v30
iface vmbr0v30
bridge_ports enp4s0.30 pr_IoT
bridge_stp off
bridge_fd 0
auto vmbr0v40
iface vmbr0v40
bridge_ports enp4s0.40 pr_Local
bridge_stp off
bridge_fd 0
auto vmbr0v50
iface vmbr0v50
bridge_ports enp4s0.50 pr_Trust
bridge_stp off
bridge_fd 0
Last edited:

