Meltdown and Spectre Linux Kernel fixes
- Thread starter martin
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
The Intel microcode update has been withdrawn because of bugs, so basically nobody can be reliably protected against Spectre today.
In the meanwhile, Linus explained how its use was crappy, and Google is developing retpoline to mitigate Spectre instead of relying to new x86 instructions.
So about Spectre, the situation is very confuse for now...
In the meanwhile, Linus explained how its use was crappy, and Google is developing retpoline to mitigate Spectre instead of relying to new x86 instructions.
So about Spectre, the situation is very confuse for now...
Are your windows machines up-to-date? Maybe you are missing a patch?
https://support.microsoft.com/en-us...your-windows-devices-against-spectre-meltdown
I cannot say for sure, they should be up to date since they have windows updates set to automatic. By all means, even if one VM was outdated, there is nothing you can do to fix it, I have tried everything. Only full reinstall of the OS can fix it.
The Intel microcode update has been withdrawn because of bugs, so basically nobody can be reliably protected against Spectre today.
In the meanwhile, Linus explained how its use was crappy, and Google is developing retpoline to mitigate Spectre instead of relying to new x86 instructions.
So about Spectre, the situation is very confuse for now...
some Intel microcode updates for some platforms/cpu models have been retracted.
the current version of Spectre mitigation in our and Ubuntu's kernel is also more than just IBRS, which Linus ranted against - there is also IBPB, other barriers, explicit register clearing, RSB stuffing. moving to retpoline is not an option for PVE at the moment because there is no supported compiler yet. in the mid- to long-term, the PVE kernels will likely move to a combination of retpoline+microcode based mitigations. if upstream decides to go with an alternative to IBRS (which is currently still being discussed), we will likely follow. in the meantime, we can only do what is currently possible.
Can we actually deploy the intel-microcode package on Proxmox 5 without any issue ?
For the moment I don't have install this one, but we need it for spectre...
I suggest you get in touch with your hardware vendor and ask for a bios update. So far a lot of hardware vendors are quite busy to get this fixed.
Yeah but I rent my server with OVH, it's not "my" server.
Asking OVH Support?
We had a pve 4.4/ceph Jewel to pve 5.1/ceph Luminous upgrade scheduled for this week. With all that's going on regarding Meltdown/Spectre is it safe to proceed with an upgrade?
Second... Well, my understanding is, that for LXC containers it is even more problematic to not fix the problem as they share the hosts kernel afaik. So if the host is vulnerable to Meltdown and Spectre attacks, so will be your LXC containers. Due to the nature of sharing the same kernel with the host, LXC containers are all but isolated.
Dear Proxmox Staff Members,
Do you verify speedbird's reply?
Does privileged LXC containers can dump whole proxmox server memory?
Regards
Dear Proxmox Staff Members,
Do you verify speedbird's reply?
Does privileged LXC containers can dump whole proxmox server memory?
Regards
if a system is vulnerable to Meltdown, any user space process can dump the whole memory unless the kernel the process is running under has mitigations in place. this includes processes running in containers/namespaces, as they share a kernel with the host. KVM accelerated VMs are not vulnerable to Meltdown across the VM-hypervisor barrier, so you cannot dump the whole host memory from a process in a VM - Meltdown still affects the guest kernel though, so you can dump the whole guest memory from an unprivileged guest process in a VM.
We just published new kernels for Proxmox VE 4.x and 5.x, addressing Meltdown and Spectre in the kernel.
Please upgrade your Proxmox VE hosts via "apt update && apt dist-upgrade".
Proxmox VE 5.x: pve-kernel (4.13.13-34)
-- Proxmox Support Team <support@proxmox.com> Sun, 7 Jan 2018 13:19:58 +0100
- cherry-pick / backport of KPTI / Meltdown fixes (from Ubuntu-4.13.0-23.25)
- add Google Spectre PoC fix for KVM
- fix objtool build regression
Proxmox VE 4.x: pve-kernel (4.4.98-102)
-- Proxmox Support Team <support@proxmox.com> Sun, 7 Jan 2018 13:15:19 +0100
- cherry-pick / backport of KPTI / Meltdown fix (based on Ubuntu-4.4.0-107.130)
- add Google Spectre PoC fix for KVM
__________________
Best regards,
Martin Maurer
Proxmox VE project leader
Hello Martin
I am wondering if there is any possibility of a fix for the kernel on version 3.4 ?
I have around 20 odd 3.4 machines which are rather difficult to move across due to the number of openvz containers!
Rob
Hello all, there is already released script for checking Specte and Meltdown vulnerables - see below
https://github.com/speed47/spectre-meltdown-checker
Current kernels 4.4.98-10x patched only for CVE-2017-5754 (Meltdown)
but not for
CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1'
CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2'
Can someone suggest when patches for CVE-2017-5753,CVE-2017-5715 will be in proxmox kernel
https://github.com/speed47/spectre-meltdown-checker
Current kernels 4.4.98-10x patched only for CVE-2017-5754 (Meltdown)
but not for
CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1'
CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2'

Can someone suggest when patches for CVE-2017-5753,CVE-2017-5715 will be in proxmox kernel
Last edited:
...
Can someone suggest when patches for CVE-2017-5753[4] will be in proxmox kernel
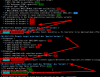
Looks like you do not run latest kernel, the script shows here:
Code:
CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1'
* Checking count of LFENCE opcodes in kernel: YES
> STATUS: NOT VULNERABLE (117 opcodes found, which is >= 70, heuristic to be improved when official patches become available)Latest kernel:
pve-kernel-4.4.98-5-pve: 4.4.98-105
Yes 105 already patched against CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1'
and not patched CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2'
View attachment 6782
So can anyone suggest when planning implement patch for CVE-2017-5715
the current spectre_v2 mitigation in PVE kernel requires matching microcode updates (many of which have subsequently been retracted by Intel).
if a system is vulnerable to Meltdown, any user space process can dump the whole memory unless the kernel the process is running under has mitigations in place. this includes processes running in containers/namespaces, as they share a kernel with the host. KVM accelerated VMs are not vulnerable to Meltdown across the VM-hypervisor barrier, so you cannot dump the whole host memory from a process in a VM - Meltdown still affects the guest kernel though, so you can dump the whole guest memory from an unprivileged guest process in a VM.
Hi fabian, with spectre v2, a guest vm can read host memory.
https://googleprojectzero.blogspot.be/2018/01/reading-privileged-memory-with-side.html
here a ubuntu kernel with spectre V1, V2 retpoline && meltdown fixed (builded with gcc 7.3 to have retpoline working)
https://launchpad.net/~canonical-ke...-33-generic_4.13.0-33.36~retpoline4_amd64.deb
https://launchpad.net/~canonical-ke...-33-generic_4.13.0-33.36~retpoline4_amd64.deb
I have installed the latest OpenVZ kernel on several of our remaining Proxmox 3.x hosts using the .deb packages they provide. If you're using ZFS, you'll also need to add those modules to the new kernel. I have made .debs for ZFS 0.7.5 under Proxmox 3.x that you're welcome to (PM me), if you're willing to trust a complete stranger. If you're not using ZFS, the kernel alone is probably all you need.Hello Martin
I am wondering if there is any possibility of a fix for the kernel on version 3.4 ?
I have around 20 odd 3.4 machines which are rather difficult to move across due to the number of openvz containers!
Rob