Hello!
As some of you may have heard, a huge security hole has been found in the Java package "log4j".
(https://www.bleepingcomputer.com/ne...og4j-java-library-is-an-enterprise-nightmare/)
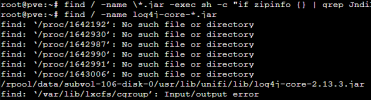
So my question is, does Proxmox also use this package?
Do we admins have to do something?
Many thanks in advance &
kind regards,
Fabian
As some of you may have heard, a huge security hole has been found in the Java package "log4j".
(https://www.bleepingcomputer.com/ne...og4j-java-library-is-an-enterprise-nightmare/)
So my question is, does Proxmox also use this package?
Do we admins have to do something?
Many thanks in advance &
kind regards,
Fabian