Description:
I am currently in the process of transitioning from my existing VLAN topology to SDN but have encountered issues that I need assistance with.
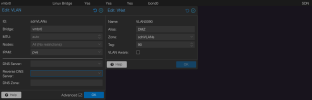
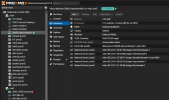
Current Working Setup:
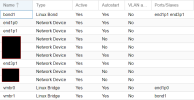
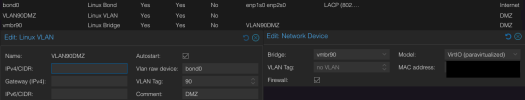
• Linux Bond: bond0 (802.3ad) (layer 3+4)
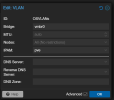
• Linux VLAN: VLAN90DMZ (raw device: bond0; VLAN Tag: 90)
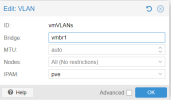
• Linux Bridge: vmbr90 (Bridge ports: VLAN90DMZ)
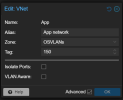
In this setup, passing the vmbr90 to a VM works seamlessly. The VM itself is unaware of any VLAN tags as it operates untagged. Only the Linux VLAN is aware of the tag.
Objective:
I want to replicate this setup using SDN, but it is not working as expected.
Ideal Scenario:
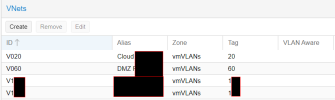
• Maintain my router/switch with tagged ports (e.g., VLAN 90) with DHCP assigning IPs in the range 192.168.1.0/24.
• Default DHCP to use the range 192.168.1.100 - 192.168.1.200 for real servers.
• Utilize SDN for internal VMs, assigning the range 192.168.1.50 - 192.168.1.99.
Problem Encountered:
Despite several attempts, I am unable to convert the current setup to SDN. The VMs do not receive any IP addresses.
Request:
I need guidance on how to transition from my current VLAN topology to SDN while ensuring VMs receive appropriate IP addresses as per the defined ranges. Detailed steps or documentation references would be highly appreciated.
Thank you for your assistance.
Best regards
I am currently in the process of transitioning from my existing VLAN topology to SDN but have encountered issues that I need assistance with.
Current Working Setup:
• Linux Bond: bond0 (802.3ad) (layer 3+4)
• Linux VLAN: VLAN90DMZ (raw device: bond0; VLAN Tag: 90)
• Linux Bridge: vmbr90 (Bridge ports: VLAN90DMZ)
In this setup, passing the vmbr90 to a VM works seamlessly. The VM itself is unaware of any VLAN tags as it operates untagged. Only the Linux VLAN is aware of the tag.
Objective:
I want to replicate this setup using SDN, but it is not working as expected.
Ideal Scenario:
• Maintain my router/switch with tagged ports (e.g., VLAN 90) with DHCP assigning IPs in the range 192.168.1.0/24.
• Default DHCP to use the range 192.168.1.100 - 192.168.1.200 for real servers.
• Utilize SDN for internal VMs, assigning the range 192.168.1.50 - 192.168.1.99.
Problem Encountered:
Despite several attempts, I am unable to convert the current setup to SDN. The VMs do not receive any IP addresses.
Request:
I need guidance on how to transition from my current VLAN topology to SDN while ensuring VMs receive appropriate IP addresses as per the defined ranges. Detailed steps or documentation references would be highly appreciated.
Thank you for your assistance.
Best regards