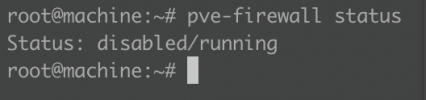
# Generated by iptables-save v1.8.7 on Mon Sep 5 15:12:17 2022
*raw
:PREROUTING ACCEPT [4096899:2629073691]
:OUTPUT ACCEPT [295346:178793848]
COMMIT
# Completed on Mon Sep 5 15:12:17 2022
# Generated by iptables-save v1.8.7 on Mon Sep 5 15:12:17 2022
*filter
:INPUT ACCEPT [140:8346]
:FORWARD ACCEPT [10221:635287]
:OUTPUT ACCEPT [90:10716]
:GROUP-proxmox-IN - [0:0]
:GROUP-proxmox-OUT - [0:0]
:PVEFW-Drop - [0:0]
:PVEFW-DropBroadcast - [0:0]
:PVEFW-FORWARD - [0:0]
:PVEFW-FWBR-IN - [0:0]
:PVEFW-FWBR-OUT - [0:0]
:PVEFW-HOST-IN - [0:0]
:PVEFW-HOST-OUT - [0:0]
:PVEFW-INPUT - [0:0]
:PVEFW-OUTPUT - [0:0]
:PVEFW-Reject - [0:0]
:PVEFW-SET-ACCEPT-MARK - [0:0]
:PVEFW-logflags - [0:0]
:PVEFW-reject - [0:0]
:PVEFW-smurflog - [0:0]
:PVEFW-smurfs - [0:0]
:PVEFW-tcpflags - [0:0]
:f2b-sshd - [0:0]
:veth100i0-IN - [0:0]
:veth100i0-OUT - [0:0]
:veth103i0-IN - [0:0]
:veth103i0-OUT - [0:0]
:veth103i1-IN - [0:0]
:veth103i1-OUT - [0:0]
-A INPUT -p tcp -m tcp --dport 22 -j f2b-sshd
-A INPUT -j PVEFW-INPUT
-A FORWARD -j PVEFW-FORWARD
-A OUTPUT -j PVEFW-OUTPUT
-A GROUP-proxmox-IN -j MARK --set-xmark 0x0/0x80000000
-A GROUP-proxmox-IN -p udp -m udp --dport 5404:5405 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-proxmox-IN -p tcp -m tcp --dport 8006 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-proxmox-IN -p tcp -m tcp --dport 85 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-proxmox-IN -p tcp -m tcp --dport 111 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-proxmox-IN -p tcp -m tcp --dport 5900:5999 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-proxmox-IN -p tcp -m tcp --dport 22 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-proxmox-IN -p tcp -m tcp --dport 3128 -g PVEFW-SET-ACCEPT-MARK
-A GROUP-proxmox-IN -m comment --comment "PVESIG:Kie2+hhlsZsVrtYe16AfvMb4DvQ"
-A GROUP-proxmox-OUT -j MARK --set-xmark 0x0/0x80000000
-A GROUP-proxmox-OUT -m comment --comment "PVESIG:tZr2a960IhOJdtNbHplv0z6TvE0"
-A PVEFW-Drop -j PVEFW-DropBroadcast
-A PVEFW-Drop -p icmp -m icmp --icmp-type 3/4 -j ACCEPT
-A PVEFW-Drop -p icmp -m icmp --icmp-type 11 -j ACCEPT
-A PVEFW-Drop -m conntrack --ctstate INVALID -j DROP
-A PVEFW-Drop -p udp -m multiport --dports 135,445 -j DROP
-A PVEFW-Drop -p udp -m udp --dport 137:139 -j DROP
-A PVEFW-Drop -p udp -m udp --sport 137 --dport 1024:65535 -j DROP
-A PVEFW-Drop -p tcp -m multiport --dports 135,139,445 -j DROP
-A PVEFW-Drop -p udp -m udp --dport 1900 -j DROP
-A PVEFW-Drop -p tcp -m tcp ! --tcp-flags FIN,SYN,RST,ACK SYN -j DROP
-A PVEFW-Drop -p udp -m udp --sport 53 -j DROP
-A PVEFW-Drop -m comment --comment "PVESIG:83WlR/a4wLbmURFqMQT3uJSgIG8"
-A PVEFW-DropBroadcast -m addrtype --dst-type BROADCAST -j DROP
-A PVEFW-DropBroadcast -m addrtype --dst-type MULTICAST -j DROP
-A PVEFW-DropBroadcast -m addrtype --dst-type ANYCAST -j DROP
-A PVEFW-DropBroadcast -d 224.0.0.0/4 -j DROP
-A PVEFW-DropBroadcast -m comment --comment "PVESIG:NyjHNAtFbkH7WGLamPpdVnxHy4w"
-A PVEFW-FORWARD -m conntrack --ctstate INVALID -j DROP
-A PVEFW-FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A PVEFW-FORWARD -m physdev --physdev-in fwln+ --physdev-is-bridged -j PVEFW-FWBR-IN
-A PVEFW-FORWARD -m physdev --physdev-out fwln+ --physdev-is-bridged -j PVEFW-FWBR-OUT
-A PVEFW-FORWARD -m comment --comment "PVESIG:qnNexOcGa+y+jebd4dAUqFSp5nw"
-A PVEFW-FWBR-IN -m physdev --physdev-out veth100i0 --physdev-is-bridged -j veth100i0-IN
-A PVEFW-FWBR-IN -m physdev --physdev-out veth103i0 --physdev-is-bridged -j veth103i0-IN
-A PVEFW-FWBR-IN -m physdev --physdev-out veth103i1 --physdev-is-bridged -j veth103i1-IN
-A PVEFW-FWBR-IN -m comment --comment "PVESIG:1GVtyKCqPoPpVXcxuMiz5bQXcac"
-A PVEFW-FWBR-OUT -m physdev --physdev-in veth100i0 --physdev-is-bridged -j veth100i0-OUT
-A PVEFW-FWBR-OUT -m physdev --physdev-in veth103i0 --physdev-is-bridged -j veth103i0-OUT
-A PVEFW-FWBR-OUT -m physdev --physdev-in veth103i1 --physdev-is-bridged -j veth103i1-OUT
-A PVEFW-FWBR-OUT -m comment --comment "PVESIG:mXQMl8JJRT3Qbo8XNwsin1sfo2E"
-A PVEFW-HOST-IN -i lo -j ACCEPT
-A PVEFW-HOST-IN -m conntrack --ctstate INVALID -j DROP
-A PVEFW-HOST-IN -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A PVEFW-HOST-IN -p igmp -j RETURN
-A PVEFW-HOST-IN -s x.x.x.x/32 -d x.x.x.x/32 -i vmbr0 -p tcp -m tcp --dport 655 -j RETURN
-A PVEFW-HOST-IN -p icmp -m icmp --icmp-type any -j RETURN
-A PVEFW-HOST-IN -i vmbr0 -j GROUP-proxmox-IN
-A PVEFW-HOST-IN -m mark --mark 0x80000000/0x80000000 -j RETURN
-A PVEFW-HOST-IN -j DROP
-A PVEFW-HOST-IN -s x.x.x.x/32 -d x.x.x.x/32 -i vmbr0 -p tcp -m tcp --dport 655 -j RETURN
-A PVEFW-HOST-IN -p icmp -m icmp --icmp-type any -j RETURN
-A PVEFW-HOST-IN -i vmbr0 -j GROUP-proxmox-IN
-A PVEFW-HOST-IN -m mark --mark 0x80000000/0x80000000 -j RETURN
-A PVEFW-HOST-IN -j DROP
-A PVEFW-HOST-IN -p tcp -m set --match-set PVEFW-0-management-v4 src -m tcp --dport 8006 -j RETURN
-A PVEFW-HOST-IN -p tcp -m set --match-set PVEFW-0-management-v4 src -m tcp --dport 5900:5999 -j RETURN
-A PVEFW-HOST-IN -p tcp -m set --match-set PVEFW-0-management-v4 src -m tcp --dport 3128 -j RETURN
-A PVEFW-HOST-IN -p tcp -m set --match-set PVEFW-0-management-v4 src -m tcp --dport 22 -j RETURN
-A PVEFW-HOST-IN -p tcp -m set --match-set PVEFW-0-management-v4 src -m tcp --dport 60000:60050 -j RETURN
-A PVEFW-HOST-IN -j RETURN
-A PVEFW-HOST-IN -m comment --comment "PVESIG:CWGHnPvCjoonuZQou6UuwIs1UTM"
-A PVEFW-HOST-OUT -o lo -j ACCEPT
-A PVEFW-HOST-OUT -m conntrack --ctstate INVALID -j DROP
-A PVEFW-HOST-OUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A PVEFW-HOST-OUT -p igmp -j RETURN
-A PVEFW-HOST-OUT -o vmbr0 -j GROUP-proxmox-OUT
-A PVEFW-HOST-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A PVEFW-HOST-OUT -o vmbr0 -j GROUP-proxmox-OUT
-A PVEFW-HOST-OUT -m mark --mark 0x80000000/0x80000000 -j RETURN
-A PVEFW-HOST-OUT -d x.x.x.x/29 -p tcp -m tcp --dport 8006 -j RETURN
-A PVEFW-HOST-OUT -d x.x.x.x/29 -p tcp -m tcp --dport 22 -j RETURN
-A PVEFW-HOST-OUT -d x.x.x.x/29 -p tcp -m tcp --dport 5900:5999 -j RETURN
-A PVEFW-HOST-OUT -d x.x.x.x/29 -p tcp -m tcp --dport 3128 -j RETURN
-A PVEFW-HOST-OUT -j RETURN
-A PVEFW-HOST-OUT -m comment --comment "PVESIG:5AwHZHZWtACMiGjfisci0I1qA58"
-A PVEFW-INPUT -j PVEFW-HOST-IN
-A PVEFW-INPUT -m comment --comment "PVESIG:+5iMmLaxKXynOB/+5xibfx7WhFk"
-A PVEFW-OUTPUT -j PVEFW-HOST-OUT
-A PVEFW-OUTPUT -m comment --comment "PVESIG:LjHoZeSSiWAG3+2ZAyL/xuEehd0"
-A PVEFW-Reject -j PVEFW-DropBroadcast
-A PVEFW-Reject -p icmp -m icmp --icmp-type 3/4 -j ACCEPT
-A PVEFW-Reject -p icmp -m icmp --icmp-type 11 -j ACCEPT
-A PVEFW-Reject -m conntrack --ctstate INVALID -j DROP
-A PVEFW-Reject -p udp -m multiport --dports 135,445 -j PVEFW-reject
-A PVEFW-Reject -p udp -m udp --dport 137:139 -j PVEFW-reject
-A PVEFW-Reject -p udp -m udp --sport 137 --dport 1024:65535 -j PVEFW-reject
-A PVEFW-Reject -p tcp -m multiport --dports 135,139,445 -j PVEFW-reject
-A PVEFW-Reject -p udp -m udp --dport 1900 -j DROP
-A PVEFW-Reject -p tcp -m tcp ! --tcp-flags FIN,SYN,RST,ACK SYN -j DROP
-A PVEFW-Reject -p udp -m udp --sport 53 -j DROP
-A PVEFW-Reject -m comment --comment "PVESIG:h3DyALVslgH5hutETfixGP08w7c"
-A PVEFW-SET-ACCEPT-MARK -j MARK --set-xmark 0x80000000/0x80000000
-A PVEFW-SET-ACCEPT-MARK -m comment --comment "PVESIG:Hg/OIgIwJChBUcWU8Xnjhdd2jUY"
-A PVEFW-logflags -j DROP
-A PVEFW-logflags -m comment --comment "PVESIG:MN4PH1oPZeABMuWr64RrygPfW7A"
-A PVEFW-reject -m addrtype --dst-type BROADCAST -j DROP
-A PVEFW-reject -s 224.0.0.0/4 -j DROP
-A PVEFW-reject -p icmp -j DROP
-A PVEFW-reject -p tcp -j REJECT --reject-with tcp-reset
-A PVEFW-reject -p udp -j REJECT --reject-with icmp-port-unreachable
-A PVEFW-reject -p icmp -j REJECT --reject-with icmp-host-unreachable
-A PVEFW-reject -j REJECT --reject-with icmp-host-prohibited
-A PVEFW-reject -m comment --comment "PVESIG:Jlkrtle1mDdtxDeI9QaDSL++Npc"
-A PVEFW-smurflog -j DROP
-A PVEFW-smurflog -m comment --comment "PVESIG:2gfT1VMkfr0JL6OccRXTGXo+1qk"
-A PVEFW-smurfs -s 0.0.0.0/32 -j RETURN
-A PVEFW-smurfs -m addrtype --src-type BROADCAST -g PVEFW-smurflog
-A PVEFW-smurfs -s 224.0.0.0/4 -g PVEFW-smurflog
-A PVEFW-smurfs -m comment --comment "PVESIG:HssVe5QCBXd5mc9kC88749+7fag"
-A PVEFW-tcpflags -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,PSH,URG -g PVEFW-logflags
-A PVEFW-tcpflags -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG NONE -g PVEFW-logflags
-A PVEFW-tcpflags -p tcp -m tcp --tcp-flags SYN,RST SYN,RST -g PVEFW-logflags
-A PVEFW-tcpflags -p tcp -m tcp --tcp-flags FIN,SYN FIN,SYN -g PVEFW-logflags
-A PVEFW-tcpflags -p tcp -m tcp --sport 0 --tcp-flags FIN,SYN,RST,ACK SYN -g PVEFW-logflags
-A PVEFW-tcpflags -m comment --comment "PVESIG:CMFojwNPqllyqD67NeI5m+bP5mo"
-A f2b-sshd -s 61.177.173.20/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 179.43.155.196/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.50/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.35/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.172.98/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.172.108/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.37/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.49/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.36/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.53/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.52/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.51/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.48/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.47/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.46/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.173.39/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.172.90/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.172.19/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.172.124/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.172.114/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -s 61.177.172.104/32 -j REJECT --reject-with icmp-port-unreachable
-A f2b-sshd -j RETURN
-A veth100i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A veth100i0-IN -p udp -m udp --dport 1194 -j ACCEPT
-A veth100i0-IN -j DROP
-A veth100i0-IN -j ACCEPT
-A veth100i0-IN -m comment --comment "PVESIG:T9fcPpV5sUkjZVKe1kMzc7aYXZs"
-A veth100i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A veth100i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A veth100i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A veth100i0-OUT -m comment --comment "PVESIG:o0+oSK2K63BSenHYls+lolXaHvY"
-A veth103i0-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A veth103i0-IN -j ACCEPT
-A veth103i0-IN -m comment --comment "PVESIG:As6KRnNJMyq1JFx/W4bBXN/2XgI"
-A veth103i0-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A veth103i0-OUT -j MARK --set-xmark 0x0/0x80000000
-A veth103i0-OUT -g PVEFW-SET-ACCEPT-MARK
-A veth103i0-OUT -m comment --comment "PVESIG:lxiTwPzICA1pTgyI8Jdk0fk4G9w"
-A veth103i1-IN -p udp -m udp --sport 67 --dport 68 -j ACCEPT
-A veth103i1-IN -j ACCEPT
-A veth103i1-IN -m comment --comment "PVESIG:wTL0uExsSaDsxtY5qoB/wP8nCXA"
-A veth103i1-OUT -p udp -m udp --sport 68 --dport 67 -g PVEFW-SET-ACCEPT-MARK
-A veth103i1-OUT -j MARK --set-xmark 0x0/0x80000000
-A veth103i1-OUT -g PVEFW-SET-ACCEPT-MARK
-A veth103i1-OUT -m comment --comment "PVESIG:0kkURfbt6WPYbDhB82s82Fb6vl8"
COMMIT
# Completed on Mon Sep 5 15:12:17 2022