$ update-ca-certificates -v --fresh
Clearing symlinks in /etc/ssl/certs...
done.
Updating certificates in /etc/ssl/certs...
Doing .
link D-TRUST_Root_Class_3_CA_2_EV_2009.pem -> d4dae3dd.0
link Entrust_Root_Certification_Authority_-_G4.pem -> 5e98733a.0
link Amazon_Root_CA_1.pem -> ce5e74ef.0
link Autoridad_de_Certificacion_Firmaprofesional_CIF_A62634068.pem -> 3bde41ac.0
link Certum_Trusted_Network_CA_2.pem -> 40193066.0
[...]
link ExampleCom_CA_HTTPS_2018.pem -> 7fdfe7ce.0
link ExampleCom_CA_2018.pem -> ffa5834b.0
[...]
link IdenTrust_Public_Sector_Root_CA_1.pem -> 1e08bfd1.0
link Trustwave_Global_Certification_Authority.pem -> f249de83.0
link certSIGN_ROOT_CA.pem -> 8d86cdd1.0
131 added, 0 removed; done.
Running hooks in /etc/ca-certificates/update.d...
done.
$
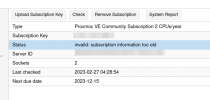
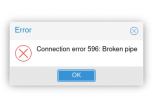
$ RUST_BACKTRACE=full pvesubscription update
thread '<unnamed>' panicked at 'Failed to add native certificate too root store: UnsupportedCriticalExtension', /usr/share/cargo/registry/ureq-2.4.0/src/rtls.rs:73:14
stack backtrace:
0: 0x7f9c8bcb92e0 - <unknown>
1: 0x7f9c8bcd671e - <unknown>
2: 0x7f9c8bca46f5 - <unknown>
3: 0x7f9c8bca6eb4 - <unknown>
4: 0x7f9c8bca6b01 - <unknown>
5: 0x7f9c8bca748a - <unknown>
6: 0x7f9c8bcb9637 - <unknown>
7: 0x7f9c8bcb942c - <unknown>
8: 0x7f9c8bca7182 - <unknown>
9: 0x7f9c8b900693 - <unknown>
10: 0x7f9c8b9007c3 - <unknown>
11: 0x7f9c8badda27 - <unknown>
12: 0x7f9c8bac857b - <unknown>
13: 0x7f9c8bc8b5bf - <unknown>
14: 0x7f9c8b8f5ad2 - <unknown>
15: 0x7f9c8bac8898 - <unknown>
16: 0x7f9c8baaedd4 - <unknown>
17: 0x7f9c8baaf9dd - <unknown>
18: 0x7f9c8b96b6eb - <unknown>
19: 0x7f9c8b9674de - <unknown>
20: 0x7f9c8b967fb7 - <unknown>
21: 0x7f9c8b967546 - <unknown>
22: 0x558e06d62157 - Perl_pp_entersub
23: 0x558e06d58846 - Perl_runops_standard
24: 0x558e06cc6b1c - perl_run
25: 0x558e06c99482 - main
26: 0x7f9c8cc16d0a - __libc_start_main
27: 0x558e06c994ca - _start
28: 0x0 - <unknown>
fatal runtime error: failed to initiate panic, error 5
Aborted